2017-01-23 Dridex Malware from Malspam
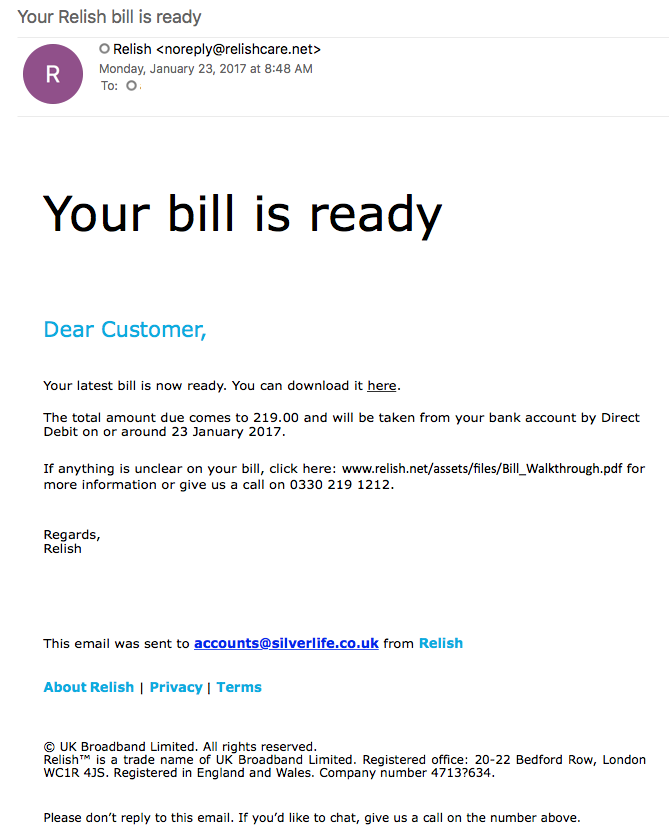
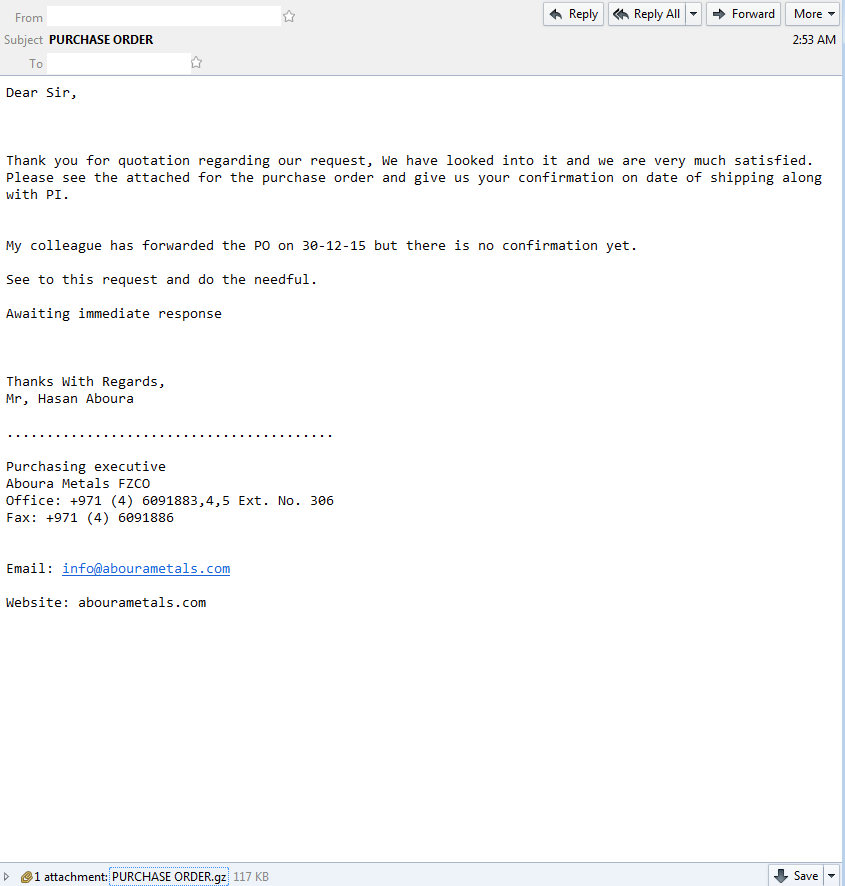
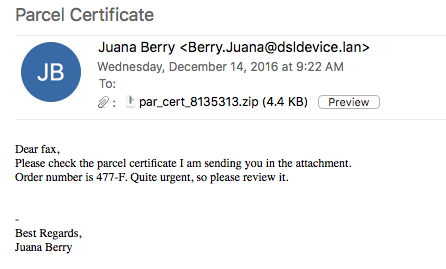
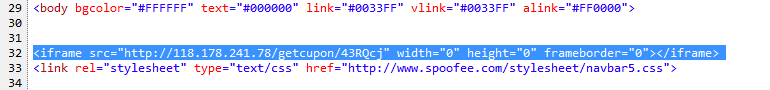
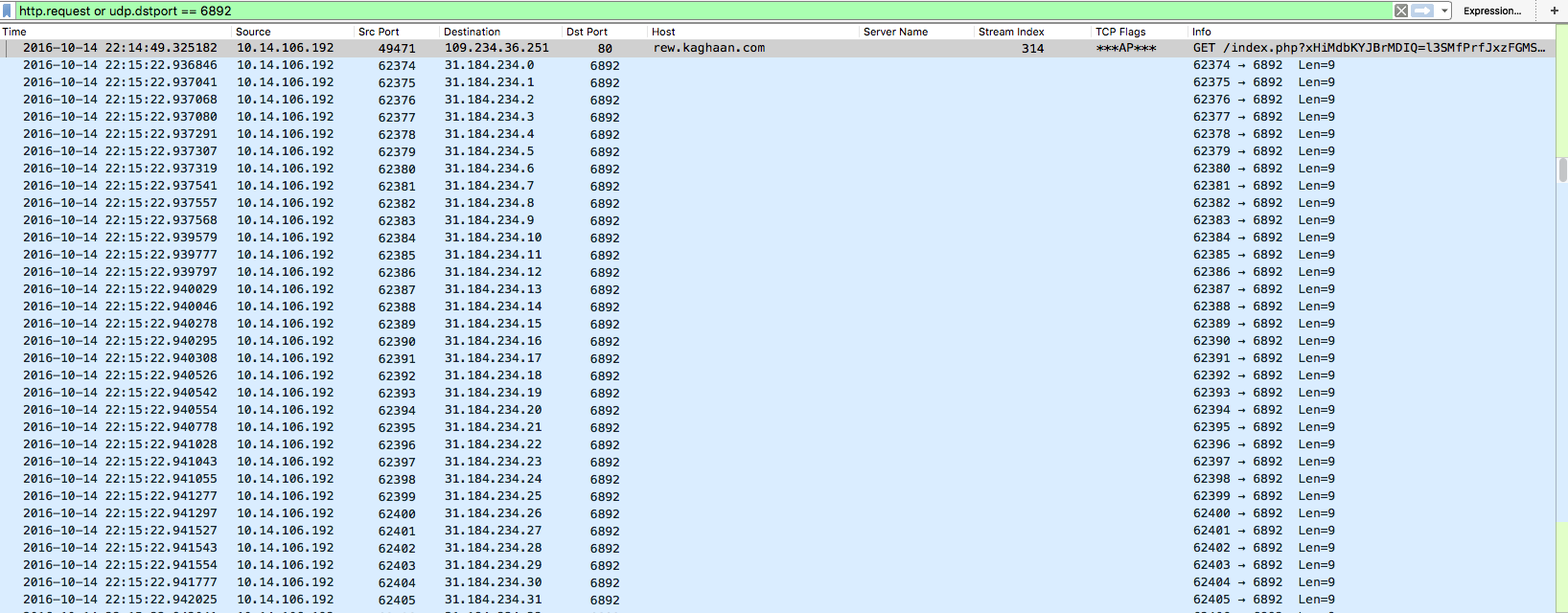
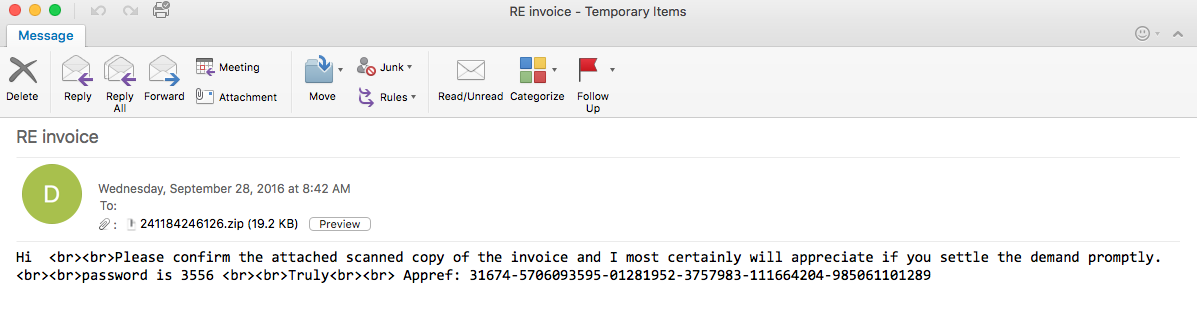
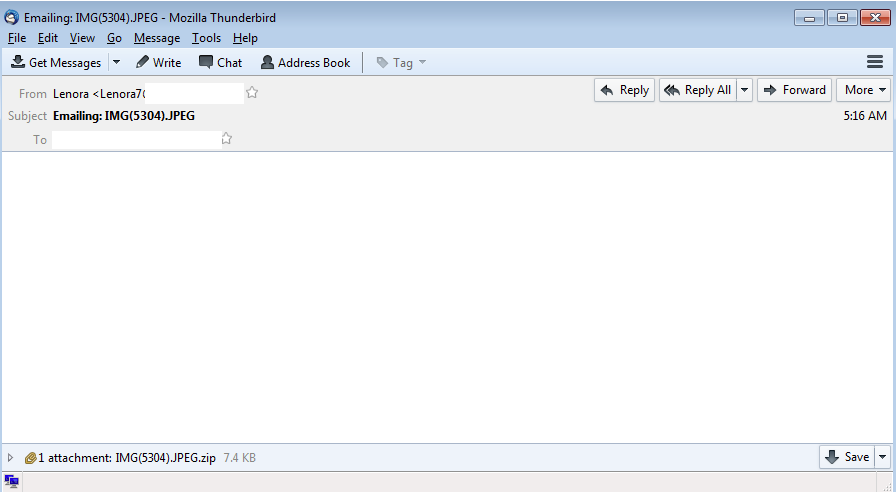
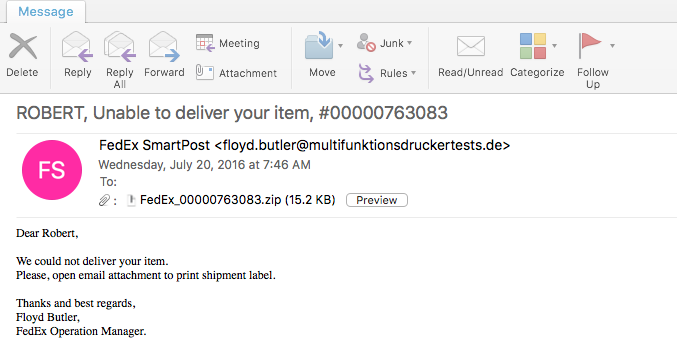
Here is an example of some Dridex malspam that I was able to analyze yesterday. As usual the artifacts and such can be found over in my Github repo found here. IOCs: ===== relish.net / 81.91.205.168 (Port 443) www1.relish.net / 81.91.205.167 (Port 443) u4593764.ct.sendgrid.net / 167.89.125.30 agfirstnz-my.sharepoint.com, prodnet329-325selectora0000.sharepointonline.com.akadns.net / 104.146.164.65 (Port 443) BrightSteps.sharepoint.com, prodnet324-328selectora0000.sharepointonline.com.akadns.net / 104.146.164.25 (Port 443) 212.227.105.182 (Port 8343) 91.121.30.169 (Port 4431) Artifacts: ========== File name: Bill View.js File size: 18KB MD5 hash: 16e101cd7af89f643efecd1aa59a39cd Virustotal: http://www.virustotal.com/en/file/149c8da70249e7ab3b055bd7b8afa15bac2a5d069195db9686b210fa6eb76073/analysis/ Payload Security: http://www.hybrid-analysis.com/sample/149c8da70249e7ab3b055bd7b8afa15bac2a5d069195db9686b210fa6eb76073?environmentId=100 File name: qqBfqaxXe.exe File size: 154KB MD5 hash: 55c2368aa15a128e946fafd700160375 Virustotal: http://www.virustotal.com/en/file/a38ea56e8849addbe6fd94c5196e02169504f9384618edb192b5e87d1a645b97/analysis/ Payload Security: http://www.hybrid-analysis.com/sample/149c8da70249e7ab3b055bd7b8afa15bac2a5d069195db9686b210fa6eb76073?environmentId=100 Analysis: ========= When looking at…