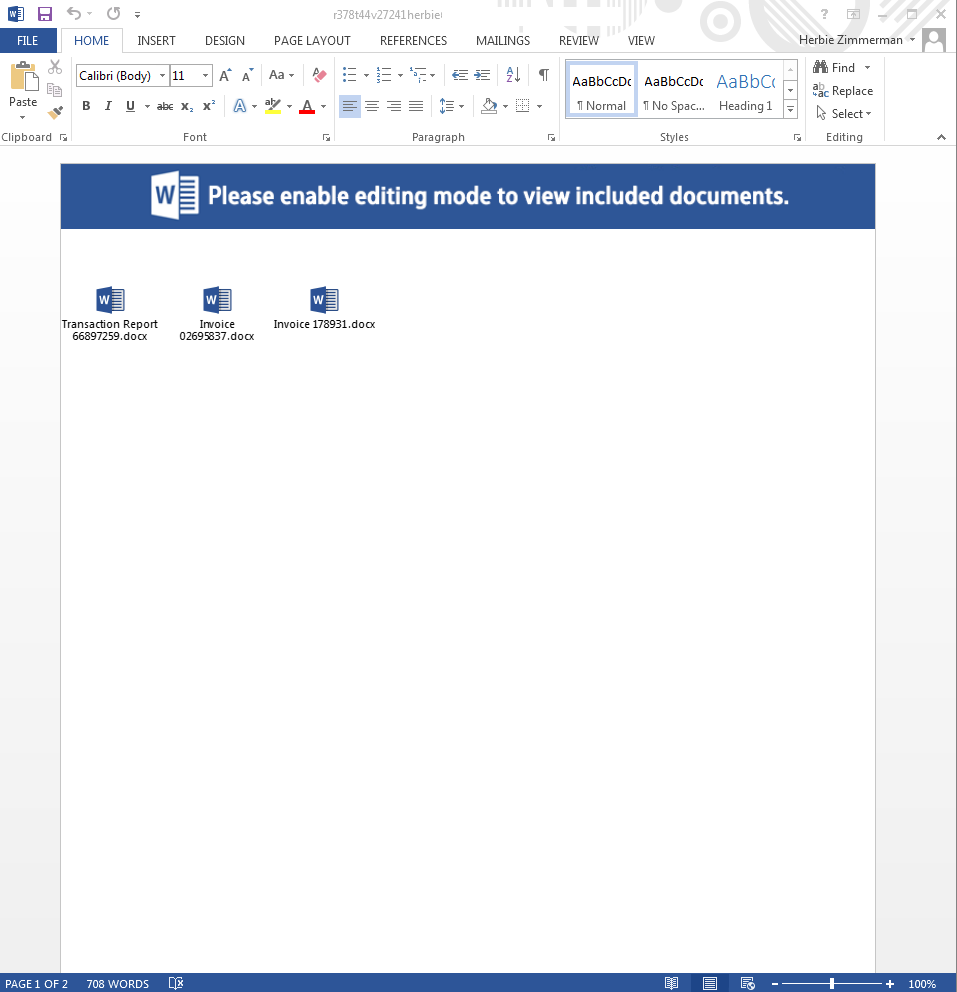
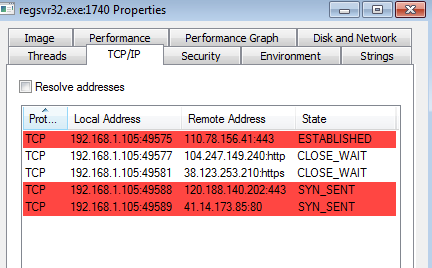
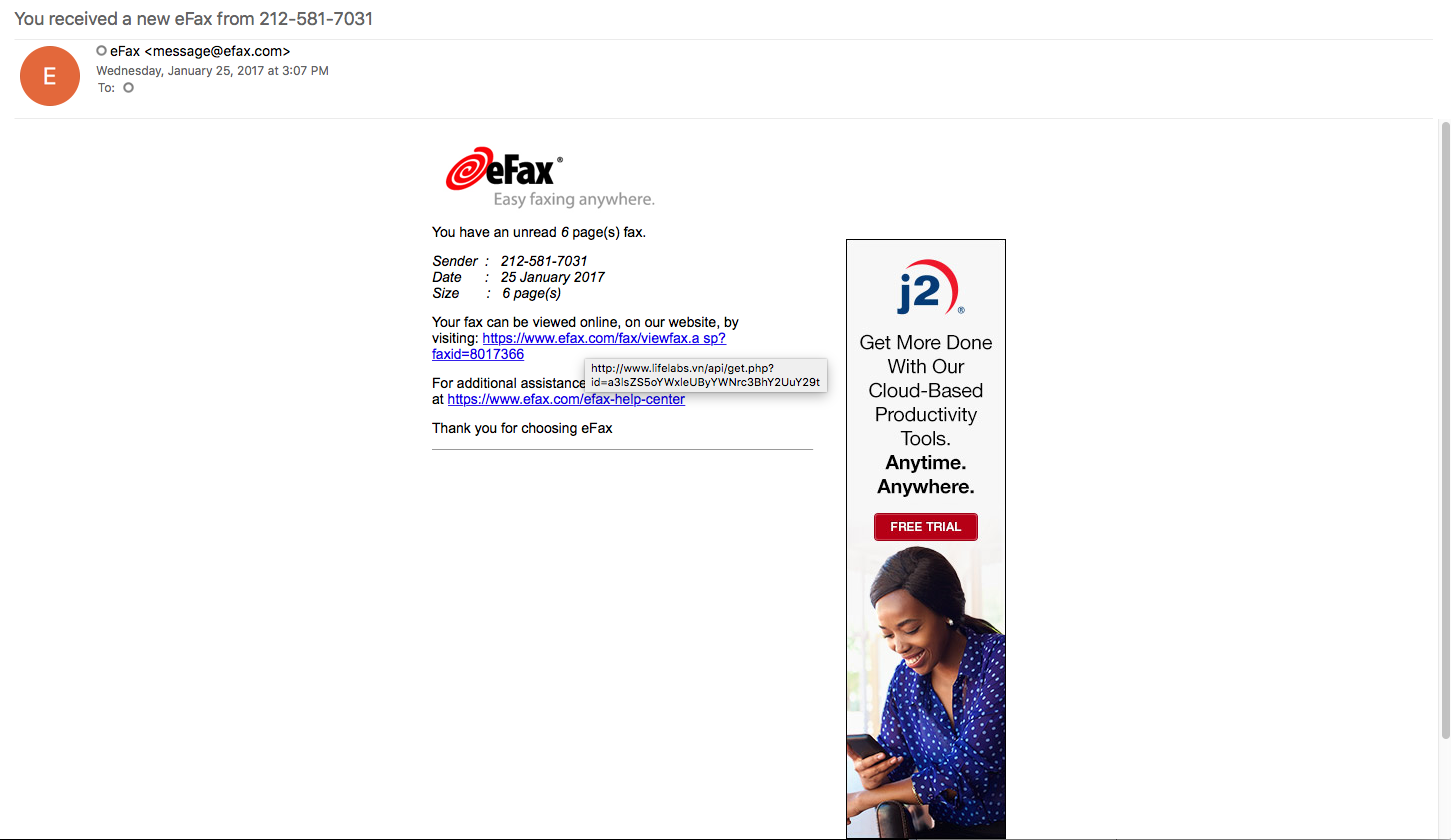
2017-05-03 Smokeloader/Dofoil malware from Malspam
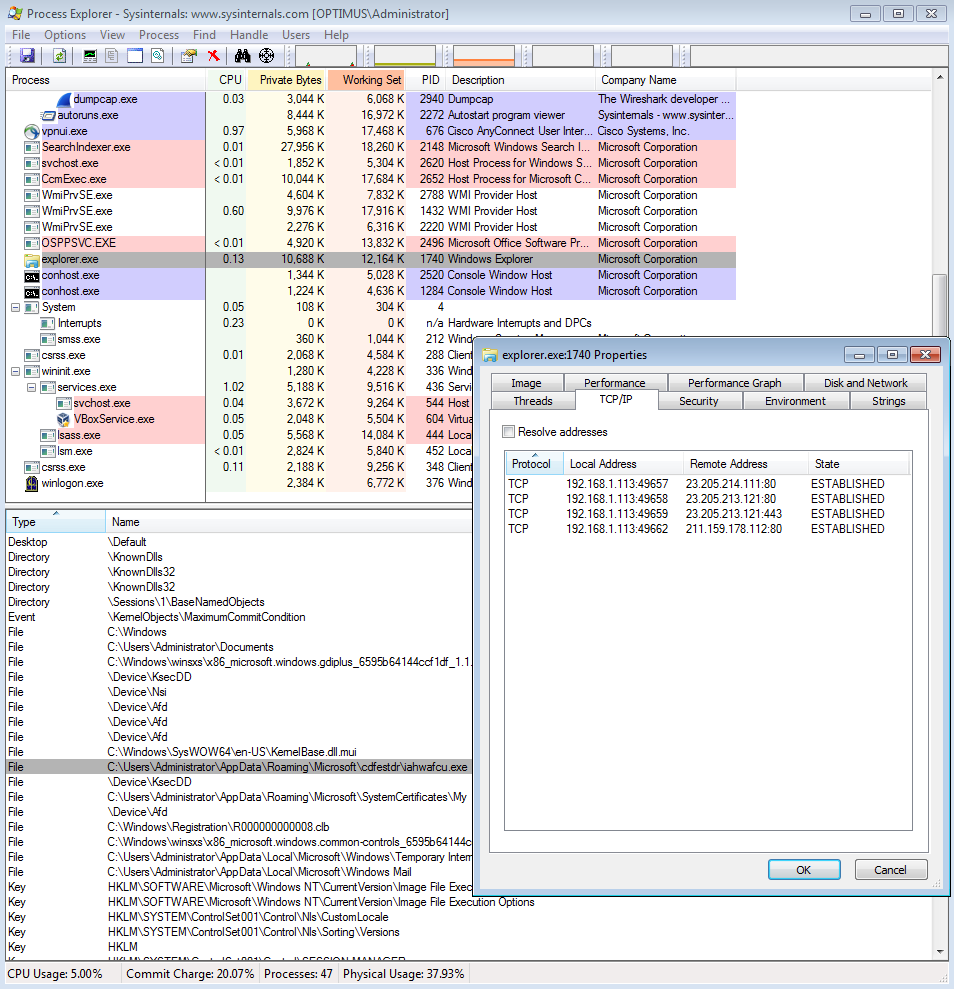
This investigation stems from a maldoc that was sent to us yesterday. It is your standard maldoc that requires you to enable content in order to get the embedded script to run. From the looks of it, the malware that is used in this infection is Smokeloader/Dofoil. For more information about this type of infection, Forcepoint had a good writeup about it which you can read about here. Granted it is not an exact match for this infection, but helps to explain some of the behavior that the malware used. I also had some fun trying my hand at de-obfuscating…