2019-07-17 AveMaria InfoStealer/RAT with interesting UAC bypass
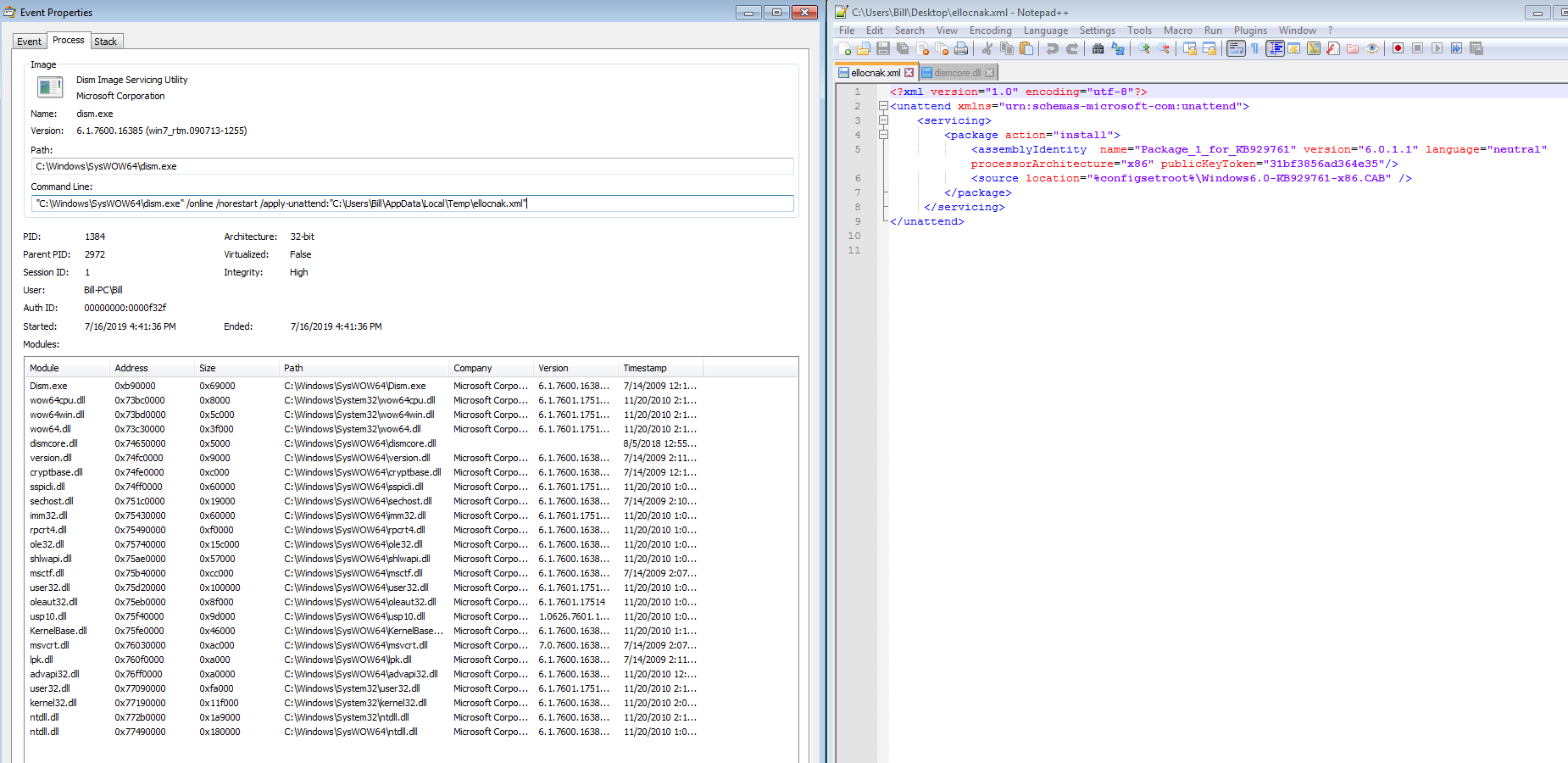
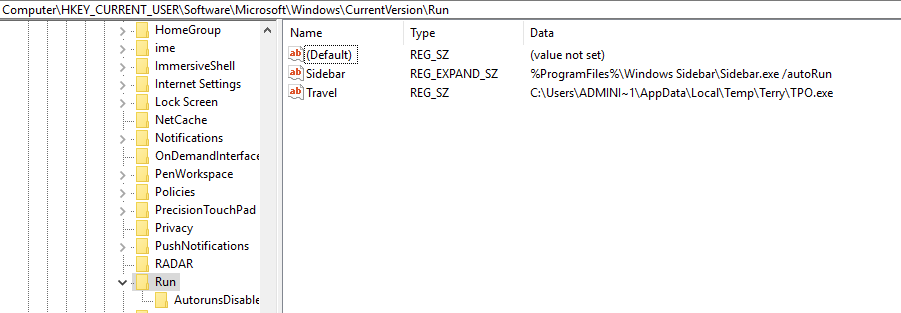
I came across this sample yesterday via my usual method – the email filters. The email is your pretty standard stuff acting as a proposal for an order. Once you open the zip file, there is an executable. From here, the fun began. For the artifacts/logs/PCAP from this analysis, please see my Github repo for this here. IOCs: ===== respainc.duckdns.org / 79.134.225.51:28 (TCP) 8.8.8.8:53 (TCP) Artifacts: ========== Microsoft.exe/Quotation.exe a07a5a3100544aceeade42e743218e6a http://www.virustotal.com/gui/file/a52f455f897f54af3e3d1505e686d391171d2f981ba7971b63cc491708b12fee/detection First Submission 2019-07-16 10:12:09 28/67 engines detected this file Path: C:\Users%USERNAME%\AppData\Roaming | %TEMP% dismcore.dll 6b906764a35508a7fd266cdd512e46b1 http://www.virustotal.com/gui/file/fc0c90044b94b080f307c16494369a0796ac1d4e74e7912ba79c15cca241801c/detection First Submission 2018-10-24 20:23:05 51/70 engines detected this file Path: %TEMP% ellocnak.xml 427eb7374887305b72f5c552837c9036 http://www.virustotal.com/gui/file/b3f421780a49cbe680a317259d4df9ce1d0cdaca3020b4df0dc18cc01d68ccbb/detection…