So continuing from my original post about the SANS 2015 Hack Challenge, here is my quick write up about exercise two.
Exercise 2
==========
> What operating system and CPU type are used in the Gnome? What type of web framework is the Gnome web interface built in?
– System
– DISTRIB_ID=’OpenWrt’
– DISTRIB_RELEASE=’Bleeding Edge’
– DISTRIB_REVISION=’r47650′
– DISTRIB_CODENAME=’designated_driver’
– DISTRIB_TARGET=’realview/generic’
– DISTRIB_DESCRIPTION=’OpenWrt Designated Driver r47650′
– DISTRIB_TAINTS=”
– CPU: ARM version 1 (SYSV)
– Gnome web framework: Looks to be node.js
> What kind of a database engine is used to support the Gnome web interface? What is the plaintext password stored in the Gnome database?
– MongoDB since there is a mongodb.conf file that points to dbPath: /opt/mongodb/
– Username and Password was found using strings against the gnome.0 file
– username admin / password SittingOnAShelf
Notes
=====
– Extracted bin file via 7Zip. Started to look around at files/dirs.
– Looking through the filesystem, came across the following files that give info about the OS
> /etc/openwrt_release and /etc/openwrt_version
– Grepped for ‘shadow’ and saw the path – C:\Users\Administrator\Desktop\Working\giyh-firmware-dump\bin\login.sh
> I could never find a shadow file though
– To verify that there was no massive difference between just uncompressing the bin file via 7Zip, I also used BinWalk and DD (which based on what I am seeing, there is a difference)
> sudo binwalk ~/Desktop/giyh-firmware-dump.bin
> dd if=giyh-firmware-dump.bin of=filesys.squash skip=168803 bs=1
> sudo binwalk ~/Desktop/filesystem.squash
– Running the Binwalk utility gave me the processor type
> ELF, 32-bit LSB shared object, ARM, version 1 (SYSV)
> This was also verified by using “binwalk -A” (-A used for common opcode signatures) as it returned nothing but pointers for “ARM instrutions, function prologue”
– Managed to get the filesystem (SquashFS) extracted using the squashfs-tools
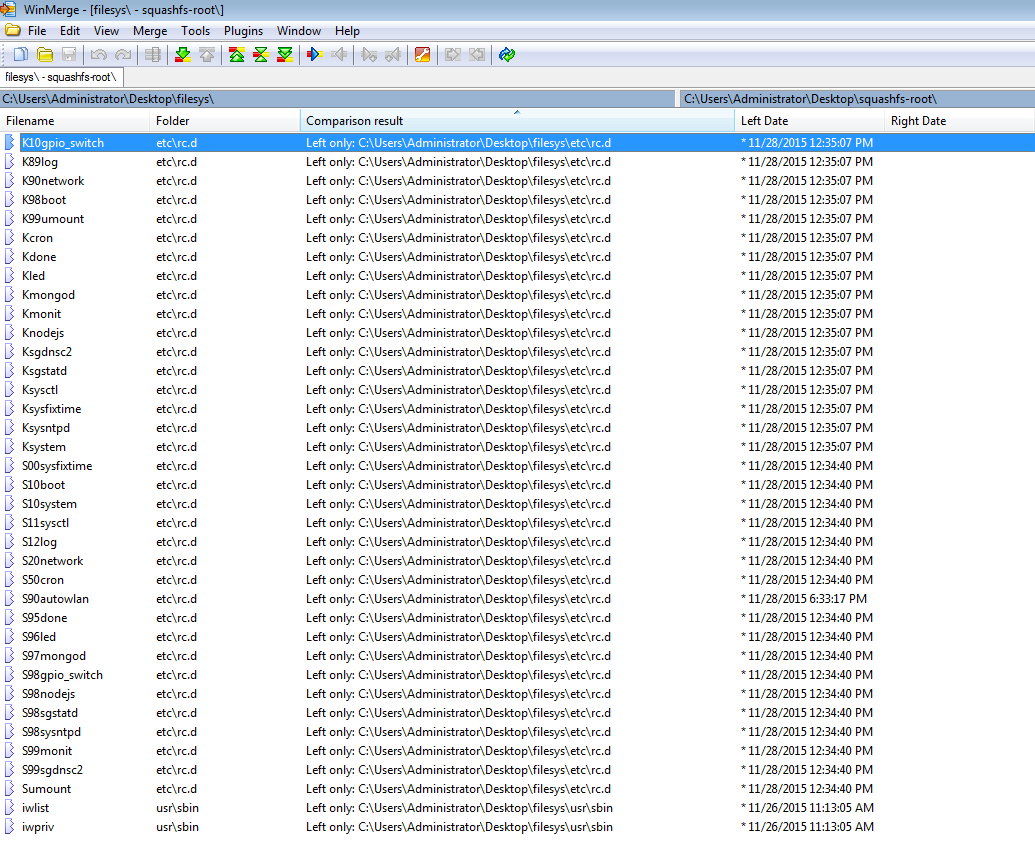
> unsquashfs – Both of the above commands (unsquashfs and dd) extract an image from the BIN file, with some differences between them (just not sure what)
Differences in folders – One on my SIFT system extracted via DD and the other from my Windows VM using 7Zip
– Saw a service for MongoDB so most likely MongoDB is supporting the web framework
> In the /etc folder there is a mongod.conf file that points to the DB path (/opt/mongodb)
> Googled for what files would be in a Mongo DB instance, noticed that there was the gnome.0 and gnome.ns
> Ran strings on the gnome.0 file and could see the username/password combo there
– Only users on this system:
> root:x:0:0:root:/root:/bin/ash
> daemon:*:1:1:daemon:/var:/bin/false
> ftp:*:55:55:ftp:/home/ftp:/bin/false
> network:*:101:101:network:/var:/bin/false
> nobody:*:65534:65534:nobody:/var:/bin/false
– In the /etc /init.d folder could also see a nodejs file
> This is most likely the web framework
***Update: Figured out the difference between the images. The one that was extracted using ‘unsquashfs’ seems to be missing files versus the other two that I did using dd and 7Zip as you can see below (dd image on the left and unsquashfs on the right):