Here is an example of some Dridex malspam that I was able to analyze yesterday. As usual the artifacts and such can be found over in my Github repo found here.
IOCs:
=====
relish.net / 81.91.205.168 (Port 443)
www1.relish.net / 81.91.205.167 (Port 443)
u4593764.ct.sendgrid.net / 167.89.125.30
agfirstnz-my.sharepoint.com, prodnet329-325selectora0000.sharepointonline.com.akadns.net / 104.146.164.65 (Port 443)
BrightSteps.sharepoint.com, prodnet324-328selectora0000.sharepointonline.com.akadns.net / 104.146.164.25 (Port 443)
212.227.105.182 (Port 8343)
91.121.30.169 (Port 4431)
Artifacts:
==========
File name: Bill View.js
File size: 18KB
MD5 hash: 16e101cd7af89f643efecd1aa59a39cd
Virustotal: http://www.virustotal.com/en/file/149c8da70249e7ab3b055bd7b8afa15bac2a5d069195db9686b210fa6eb76073/analysis/
Payload Security: http://www.hybrid-analysis.com/sample/149c8da70249e7ab3b055bd7b8afa15bac2a5d069195db9686b210fa6eb76073?environmentId=100
File name: qqBfqaxXe.exe
File size: 154KB
MD5 hash: 55c2368aa15a128e946fafd700160375
Virustotal: http://www.virustotal.com/en/file/a38ea56e8849addbe6fd94c5196e02169504f9384618edb192b5e87d1a645b97/analysis/
Payload Security: http://www.hybrid-analysis.com/sample/149c8da70249e7ab3b055bd7b8afa15bac2a5d069195db9686b210fa6eb76073?environmentId=100
Analysis:
=========
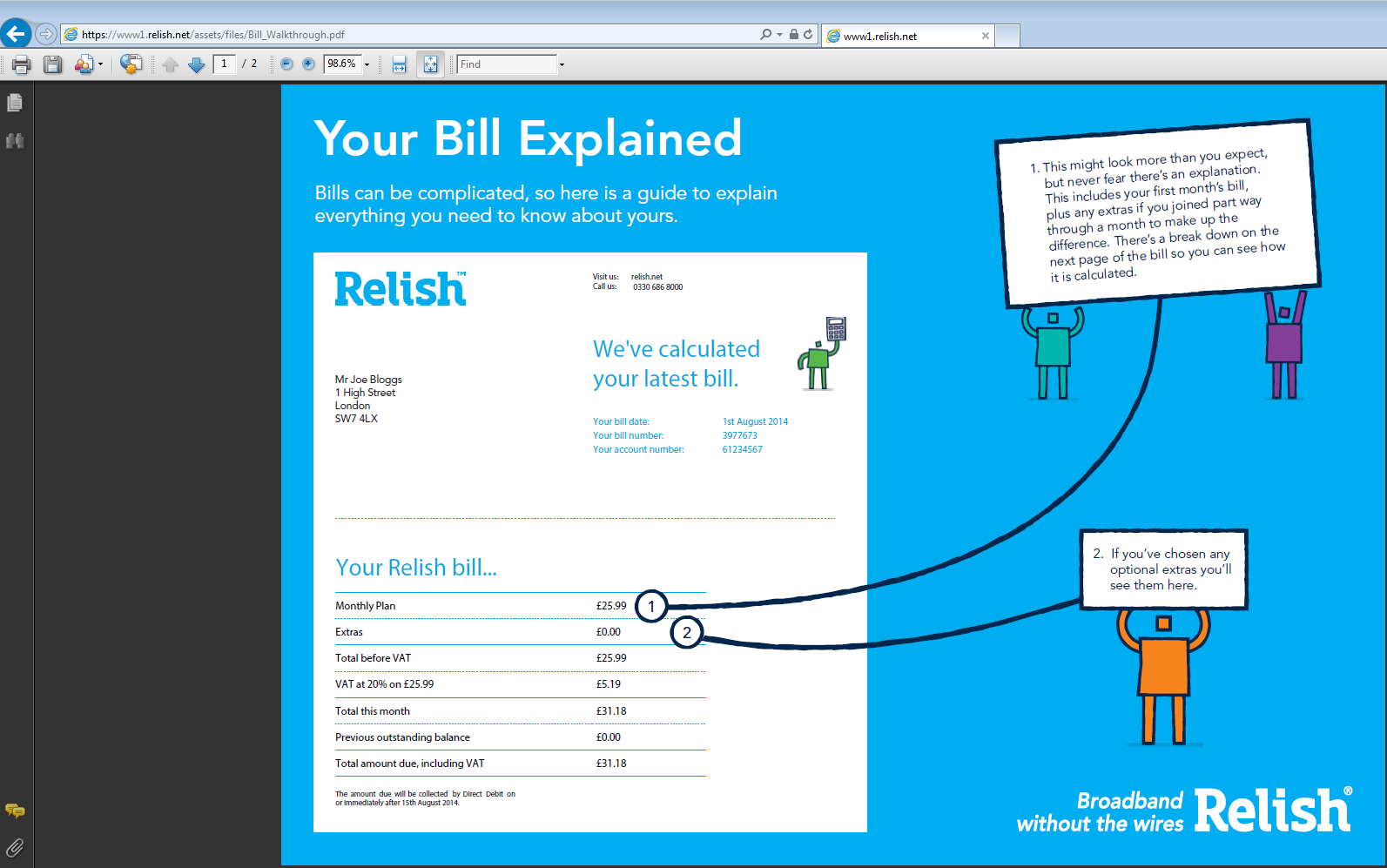
When looking at the email there are two links that one can choose from: one that is click-able and one that would require the user to copy the link and paste it into a browser. When I copied the link www[.]relish[.]net/assets/files/Bill_Walkthrough[.]pdf in my test VM, all I got was a redirect over to hxxps://www1[.]relish[.]net/assets/files/Bill_Walkthrough[.]pdf and a PDF within the browser. I was not able to see anything malicious in the traffic (granted since this is over HTTPS, there may be something there that I am not aware of). There are no odd calls to other IP addresses or to other odd ports either.
GET /assets/files/Bill_Walkthrough.pdf HTTP/1.1 Accept: text/html, application/xhtml+xml, */* Accept-Language: en-US User-Agent: Mozilla/5.0 (compatible; MSIE 10.0; Windows NT 6.1; WOW64; Trident/6.0) Accept-Encoding: gzip, deflate Host: www.relish.net DNT: 1 Connection: Keep-Alive HTTP/1.1 301 Moved Permanently Date: Tue, 24 Jan 2017 10:43:24 GMT Server: Shelob (Cirith Ungol) Location: http://www1.relish.net/assets/files/Bill_Walkthrough.pdf Content-Length: 265 Connection: close Content-Type: text/html; charset=iso-8859-1 Set-Cookie: SERVERID=a1; path=/ Cache-control: private <!DOCTYPE HTML PUBLIC "-//IETF//DTD HTML 2.0//EN"> <html><head> <title>301 Moved Permanently</title> </head><body> <h1>Moved Permanently</h1> <p>The document has moved <a href="http://www1.relish.net/assets/files/Bill_Walkthrough.pdf">here</a>.</p> </body></html>
So using the actual click-able link in the email,
hxxps://u4593764.ct.sendgrid.net/wf/click?upn=k9OTkOER8h7YFf7fJP9mBAZcqDUL275grn71x4zt0yw2Em-2B0a-2BmXdo47N2kVgjCKAQ1Q4LP4qPlK0ITYcdgZXoD9TfrtqJF1TVrkHwkWS2AGUTInNlOGo3s4bECuBRmpBZDxk4-2FyyyjSqrVyYIpGeMlu5zyOdP9WSTSPYuZmehzE3U9eUsbJWNoZokYy6WTf1d9DT7QUos1O0zaCktOPm3HiYfGpjJW0n91Q4gtzBr2PW6EbkbZPSK5-2Bi-2B8HLZ8p_-2BuyqbAT6LrWvGmCRH8NeQTy9rEdT64T-2FUVIvL-2BRmtG0XxQlgdBDnDMcjUVlyunGGxAEMitYZpPiTxvFp8hh2c2IOPMn071bJqWM-2FYi-2B8CQvR5Qe5YNE0kAJISNG2chxdjIMSuDpSeOLgW8LoxakqmxkUoTC7eg3hSYQiIddSs0IFLGUYe0F2f-2FNGSFJ50agi8VkBwdgGLChVGTqJxGn4m58PUGNGVx8Y1T3iFAplIPU-3D
I got asked if I wanted to save the file “Bill View.zip” which contained a Javascript file called “Bill View.js.” From what I can see, this file is hosted on a Sharepoint site as there is a request for the domain “agfirstnz-my.sharepoint.com” which ultimately directs points to the domain of “prodnet329-325selectora0000.sharepointonline.com.akadns.net.” The file is saved from that site over HTTPS:
...........X.2...|.3.e...HXq......y..P.O.D...../.5...
..... .
.2.8.......B........ .....agfirstnz-my.sharepoint.com..........
......................Q..X.2...]ZL.........xU..q..'.Z.B.. V.......>.c!...)..,.f..,b!...v1..... ...................0..
0..........Z.....V/.3-\[......0
. *.H..
.....0..1.0 ..U....US1.0...U...
Washington1.0...U....Redmond1.0...U.
..Microsoft Corporation1.0...U....Microsoft IT1.0...U....Microsoft IT SSL SHA20..
160223194210Z.
180222194210Z0..1.0 ..U....US1.0 ..U....WA1.0...U....Redmond1.0...U.
..Microsoft Corporation1.0...U....Microsoft Corporation1.0...U....*.sharepoint.com0.."0
. *.H..
..........0..
.......T....*'^.)....|....c..[.d.3..a..'....1.../...~..:j.a./..-.CP.l.Q;..y..e....:.WK..f10.......]..J........X.A.f.Y.Q..u.o.\.]3..%...QwY.....................d......1v..Oen.z.it..on.yHX`.r.ILD..........}R.uUd...7.pkM.o.w...=.%/b.....!..f....!......y...h.B.............j0..f0...U........0...U.%..0...+.........+.......0...U........m.z...... ..(...G.0....U.....0....*.sharepoint.com.%*.sharepoint.apac.microsoftonline.com.%*.sharepoint.emea.microsoftonline.com. *.sharepoint.microsoftonline.com0...U.#..0...Q.$&..h"W.&+;Fb.{...0}..U...v0t0r.p.n.6http://mscrl.microsoft.com/pki/mscorp/crl/msitwww2.crl.4http://crl.microsoft.com/pki/mscorp/crl/msitwww2.crl0p..+........d0b0<..+.....0..0http://www.microsoft.com/pki/mscorp/msitwww2.crt0"..+.....0...http://ocsp.msocsp.com0N..U. .G0E0C. +.....7*.0604..+........(http://www.microsoft.com/pki/mscorp/cps.0'. +.....7.
Once I executed the Javascript file that was downloaded above, I saw a callback to BrightSteps.sharepoint.com which points to “prodnet324-328selectora0000.sharepointonline.com.akadns.net,” which is encrypted over HTTPS again.
...........X.2.2^.%L;.^
.$.g....p..../..2.3..../.5...
..... .
.2.8.......D........". ...brightsteps-my.sharepoint.com..........
......................Q..X.2.....#..!........vD..[..o.... .?.......*..?i..0_[....3.uxa...Y.... ...................0..
0..........Z.....V/.3-\[......0
. *.H..
.....0..1.0 ..U....US1.0...U...
Washington1.0...U....Redmond1.0...U.
..Microsoft Corporation1.0...U....Microsoft IT1.0...U....Microsoft IT SSL SHA20..
160223194210Z.
180222194210Z0..1.0 ..U....US1.0 ..U....WA1.0...U....Redmond1.0...U.
..Microsoft Corporation1.0...U....Microsoft Corporation1.0...U....*.sharepoint.com0.."0
. *.H..
..........0..
.......T....*'^.)....|....c..[.d.3..a..'....1.../...~..:j.a./..-.CP.l.Q;..y..e....:.WK..f10.......]..J........X.A.f.Y.Q..u.o.\.]3..%...QwY.....................d......1v..Oen.z.it..on.yHX`.r.ILD..........}R.uUd...7.pkM.o.w...=.%/b.....!..f....!......y...h.B.............j0..f0...U........0...U.%..0...+.........+.......0...U........m.z...... ..(...G.0....U.....0....*.sharepoint.com.%*.sharepoint.apac.microsoftonline.com.%*.sharepoint.emea.microsoftonline.com. *.sharepoint.microsoftonline.com0...U.#..0...Q.$&..h"W.&+;Fb.{...0}..U...v0t0r.p.n.6http://mscrl.microsoft.com/pki/mscorp/crl/msitwww2.crl.4http://crl.microsoft.com/pki/mscorp/crl/msitwww2.crl0p..+........d0b0<..+.....0..0http://www.microsoft.com/pki/mscorp/msitwww2.crt0"..+.....0...http://ocsp.msocsp.com0N..U. .G0E0C. +.....7*.0604..+........(http://www.microsoft.com/pki/mscorp/cps.0'. +.....7.
From there, I then saw encrypted communication to the IP address of 212.227.105.182 via port 8343:
....c..._..X..g... A,....&...*F_..w.Y&w.1v...../.5...
..... .
.2.8.......................
..................Q...M..X..gzJ..4..1.....kl...#9........ 4.....o...{ZM4.Y....BhM*.D.....l./.......................0...0......... .....~..
0
. *.H..
.....0..1.0 ..U....IQ1+0)..U..."Isucot ssowartit rsmavi sbaratyto21.0...U....Baghdad1.0...U.
..Obonthat SEM1'0%..U....Supotinousa.athuauirsdwa.loans0..
170115150504Z.
170716150504Z0..1.0 ..U....IQ1+0)..U..."Isucot ssowartit rsmavi sbaratyto21.0...U....Baghdad1.0...U.
..Obonthat SEM1'0%..U....Supotinousa.athuauirsdwa.loans0.."0
. *.H..
..........0..
..........2..3..b.eez@K..:...H.Y..........eX.D ..l.u.sI=.*..{w....us..yY.Y.e.B.7.o...&w..\.O..ul4.%._...H\*Q.-.e....$....1I,#..\%..dt..z...;.x..!..L1....7
v.c..H|..?-...%...r...6U?.h.m|y.)....... ]......D&P/...7R...@. ..,..S.c_wQ3..~.W./...Q.I...A>.?U.R..x..."I......P0N0...U......{.Y.p.I...KLq.@..h..0...U.#..0...{.Y.p.I...KLq.@..h..0...U....0....0
. *.H..
..........|C.........sp.".y_....GJ9...P...v.......][.y...@P......0"J-.q..6.o....-$.I..h.._.....\-B.\.!<..E@..z`/C.....w.'0....Z...<..k..K.....hs.u....F.L#[..2#.r%.X...gr/.}......x.@94..P....r...~f]..{2....Z{.........q.........($3..|..w..&....g.u5..H...(#......T5R!2........................Y5...Q).;...1..Doo........r.....r......
..X.b..G(eMe.F..}....G..jK.Z..*WU...Z..C..t.....?0....#.....XOh........).........I.....Zpi.2Yy.!.......+Dj.....\9........F..e.5;...o.... .....T.]...k.(....R.6....[DvC...z.Rh/.{..nT*...$......e...] ....G.F..P2....j..........0y.9.EC."*.....?.1...J.C.q..
.6.4
.sR.h.z._..j
............0
..i.....J._..Xh.._._.v.......?.5<H.}.$..RKh...........<.`OTl......)Sw`+.8....M.....x.....JC.c.u.....*VK..f# P-..c...x...5..\h.dEY..../t.d.=...!.....]...7h.a.7....&ge2R.....7'.6..`....IP.=.............P
....A..Y........a.T.......xp..n...F....a\..<.v#..yd.nb......W7.=>&]=...........D...n...k..D......H.%.T..<...2.IL..n..gY.....w.s>...1Z.J.,'... ....9rlBu.7<........?.|..~F...o.L....J.....;..OV.w(..^.Fb*/^.H.
l6.K..^..Ps.f(.f.l)6....=.Y..J...u.n.....a.J...7;#..I........
k&
.K....{..blK..Vd8i.F.h$.....,...yU.I..H1=.(G-.g.l..R......4......8ykx..:.......<I.V.1...&/:...`...0F.......}...}O....).@..5 .Xw..L}.c....^..e.IR.pa4
......DmT...v.C}...CB......j..~t..?.OS.^l
^A<......Eq|(.T..R.Z."
g......~.....'...y..?..S....XyH..7.<..r_._
..f..)GK..Hd..,....F..@.7J..f......_W{O../.k...M..#....z
I..!.|. }..4...&..^#..%T.+p... |..T....I.T6(X...9.Viu>-.:..9..$..F...!q..pu...Au._.)?h..ZX....#!.~. .....[
." ..1i..b"..a'.>.p.xG....e-+qh>....=..1Hw........p../.6a{.i\.jG@...{TY.jr..$. .."....9..s.Ab|>L.HR....'.$.\.w.i....z...Q...`.An6...^.z..:..x./...[+.:%"oy...
...i>.|...y...*J.x(1.....P=,f.n>Q&....z..C.....1.......m........H
~..l.ON..*=jQ.K.(.}.c.o...0...N;....K.>5............D:.W.V..:.,..8... {.i.x}?...<....C..{v...W.F....zm;A1..=.r..h..-."N......3O....ve.%..78....w..C.os.2..mE.r6....C........;..<..q.o.}.HY-....`.I\.[I.2K...@h.0_(J.u.....]1..1z.k,.)Q....P...l..>...i%.V....(h......g..\l85k..?O...x"<yen..D......'.;...N.;..J....z..NlY.....L.....[...i.0.?..m..z.a..v.i..K.o?[../...J.Q..zf."}
u<y......w9.`.a...
....m..uv_=Y._..C#WX..(.CY....(...
.3.p.S....J.HL=....U......N....+F....w.cud..s..9.......S.l^...@W.....].>.R.&,...A..L...^.s......%5_N]...@........Pc..I..
and then encrypted communication to the IP address of 91.121.30.169 via port 4431.
....c..._..X....b8...Hd.....X'[.....d...}....../.5...
..... .
.2.8.......................
..................Q...M..X....>sE.
.+.../...Y...x$...h.%. .n\#[E...x.]...5...>mT}2k..<h.i../.......................0...0......... ...>.....0
. *.H..
.....0..1.0 ..U....JM1 0...U....Idnoim omirk2 Hantthan91.0...U....Kingston1.0...U.
.
Alerpe Co.1.0...U... elantelit1%0#..U....Thai_lerec.0alermedspaf.guge0..
170115150528Z.
170716150528Z0..1.0 ..U....JM1 0...U....Idnoim omirk2 Hantthan91.0...U....Kingston1.0...U.
.
Alerpe Co.1.0...U... elantelit1%0#..U....Thai_lerec.0alermedspaf.guge0.."0
. *.H..
..........0..
......H...Y.].x.p.5OhI\.,..5S..VMm...L.%..^.7.{'.*..'....w...r8..?..d. .....,..o.q.U*.\)$,.w..i....?.:.+fJj.k........-N0.P.N..D&l6.~l*.Pb...D....._-p. .D7.u}.[.7..z.L.0...R..;..z...]...[B.E...._.../...E....;.M`..N.+....>c8&
o.?.3....a.h...*... ...dQ..>...............P0N0...U........q.Qpt... i.Z.U...R0...U.#..0.....q.Qpt... i.Z.U...R0...U....0....0
. *.H..
..........J...x..Hu.j#.X,.J....O..0't.L.Wu.fd.FN.Wi...+).....;.........):.....*=...u..7.h....TX...#.......5:......&R1.......taq
"S..o.Q....S ..?..C.if9.7..2...IF.%._.AE...nY.s-.U.SUT{..qn.&...5...*.q.c...P0.v.W...g.....N..`...W.
.TK....E...!............... ..4j.j.......................D.m....WxB.o.t.......ue.........9......~\.... .?.UY...J.......l.*.pWU.).g.&g.">....~...=;...%%......'..JD..9\.t.V."@..N....]..Q..c.5#.......rnO...z. -R.wH..... ........^.@?.N....-..(..q..g6.....L..h'=....O...l......c........M_N......J.......
\.(k.u.$.pWh$\..........0.....9..).(..!.Q.... /..?..=..0q.,...].M}%Q.s
9...........0L.....F.....'.cCu..l?.h.5.)Mm.....%W+3.C.............T...vv....".|.55.^u.V.}.pA..j..j.,w.~.C.Z..0....;.H1.aChbl....6f.y..CD..7.;cs]..".....dUd.....J....w.._uJX...O..@.|.}k........"....{......<
........P...[.XL.....fd
..
f....-jn.\.D....5........m..eW...A.}..a.
#..+.5<".8.!.......'64.Gm.q.V...Y..M.Ys^.*1!c.......-...g.@ .db...[...c. ./jg..AG...x..........x.`C....`
..R.;....s.....\'.....[..F..@.;~.UF....y........N....WFc...1~s>z0....Gg'...$......). ...{..t...T
.|.k0f./!T........zw.....'...........9U.........?v..o..q.O....J..m........5D...[...w....U..'=.I...!{U.,..g.....E......w~.h..../..{Ox....#...+.N.&...w7.9=..@4H+........sF....{.;r......l . .....;..t.n.~..E.W....y.w.@.....Lj:..#..e8....DJn.J...I.h..}.d.D.n.....!O}....[K... ...+{........R.....ZD..#...>o...v.T..$.r..:W....-.i).`Z.i..4.....)^....7.iDN.8.$......}.w|.*........w.h;
.|rL......
...fl..1>.9...`.&m8[..&.c......M..[Fq..sL.....D;gN.w.(g.....1.NJ >].P..q".S..4.p..q...I..:.sk.7............G'".&."S.J.&..EkR\..Z%....z#..i.....Y.-.&~tc...+y...z.0.#>...|.......{ .x..#.P....[%\.9h.@E.*H2p.R.j.S.e..b,...QZ.....$&...~...%.....;cY.#B.g..W.<Jk..b+7.i..klK...f. ..k.1 J..N.e.@!i.1...^._...?..4}..`.FpI..H...........}Zn...i.>.M%..... ..5..O. .C|%....Y..J.1g.A
...T9.....y.N?...9.q..6:....C..T.p.*..RO.j.....mg(.....(....R..V.......z."".....F>N.wR....`..O.....7....b......O.....<.P...y.Q.m.......0...W.......L../.i.r.u+....K.Bzk*.'... ..
....H.....q)F..N.&W...y.>.?.......U..Z.Rb.B.]..\...y....P.&..F...E.:..n].m.9...Y...Pk...+.....(:)~l.ji>}..k..6V+..}laP_..$7qn....A.....B.<.......p..._....%...3...ph....oy.91....F..V#..{.Rs.Wx^..[N|....e..oHd...=%...
. ..`....l..P
.......9....]7..;A.....g..{....rzO.