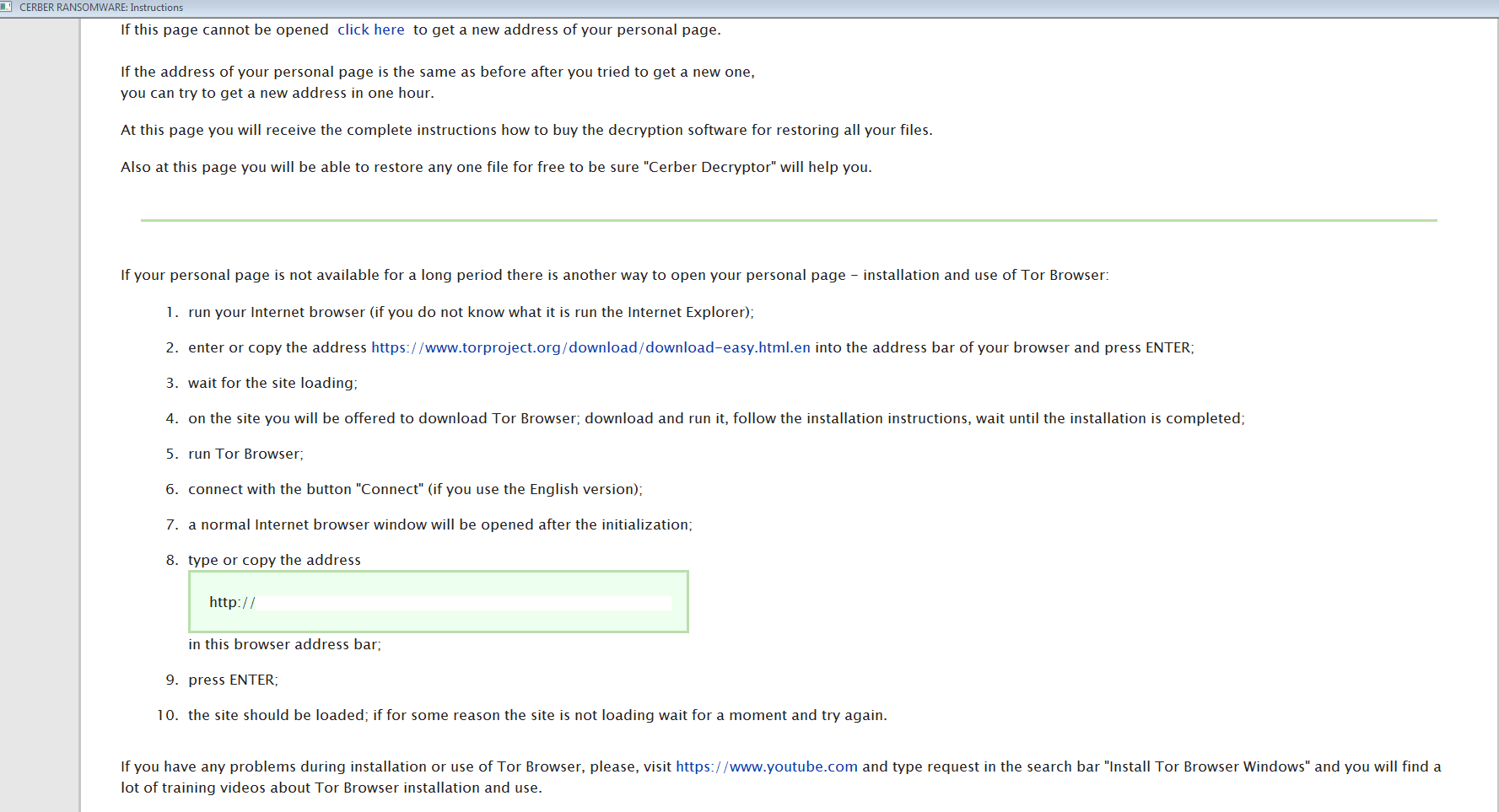
For this blog post, I was able to infect my VM with Cerber from a link that I found via a Tweet that @malware_traffic retweeted from @Techhelplistcom. I am not able to determine how a user would get directed to this site though, so that part is a mystery. Overall, this was pretty straight-forward Cerber infection that one has become used to seeing. The artifacts and logs/pcap for this infection can be found in this repo here.
IOCs:
=====
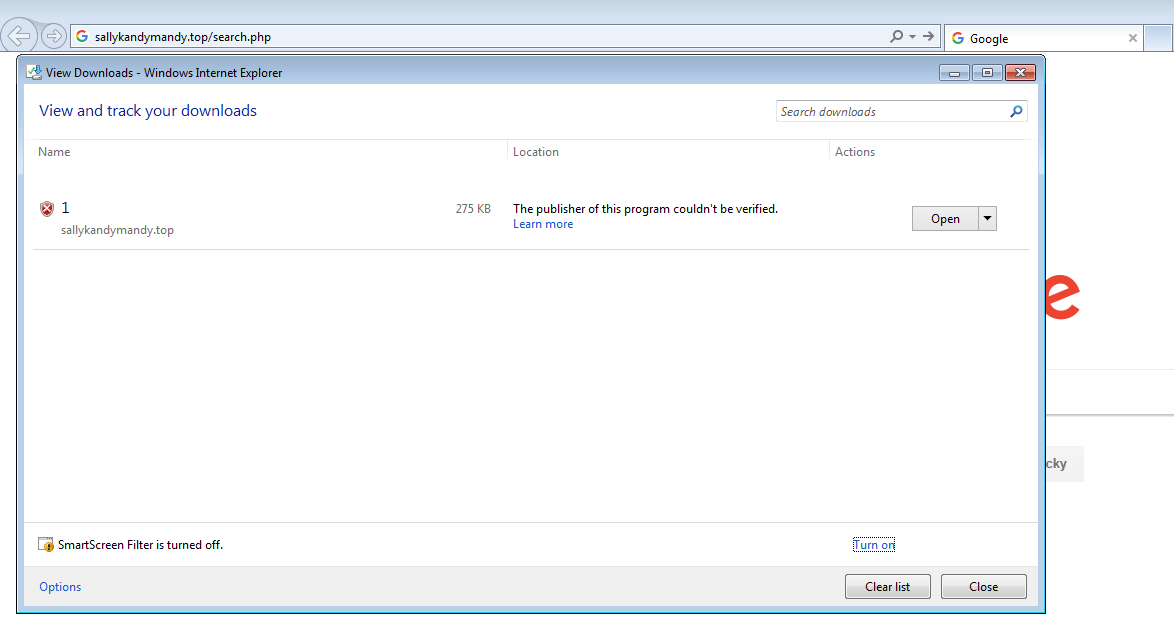
92.242.40.154 / sallykandymandy[.]top/search.php
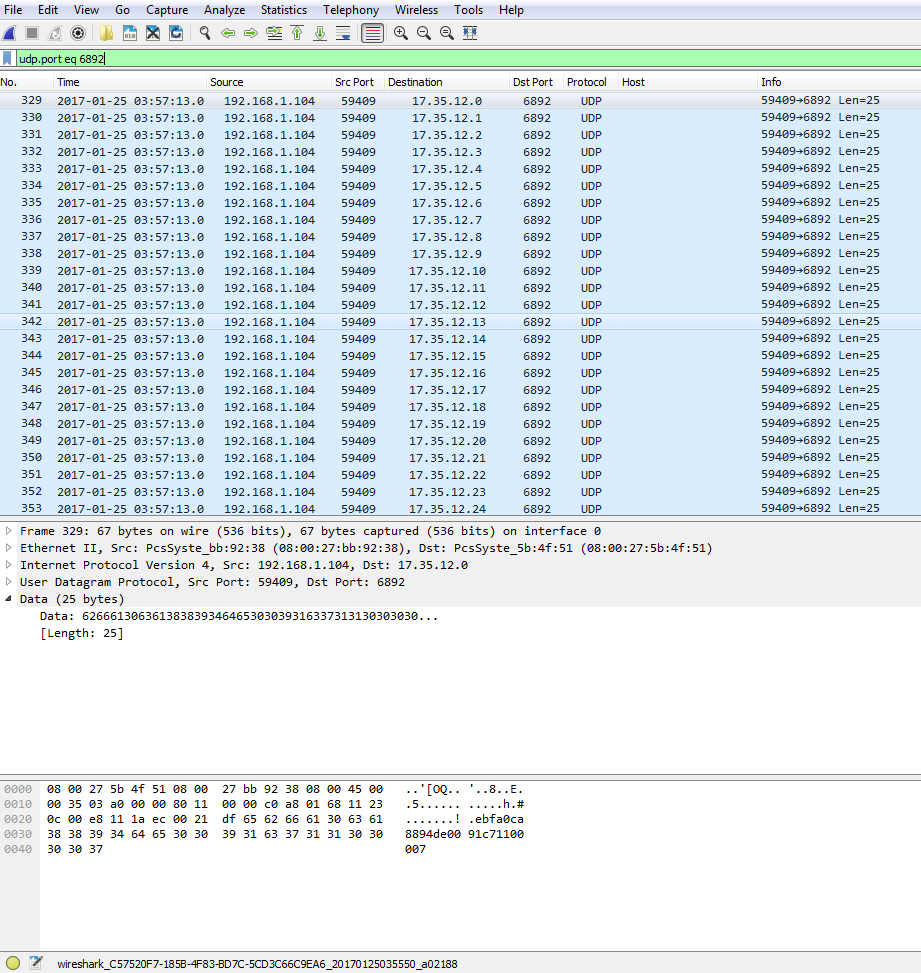
11.56.22.0 – 11.56.22.31 (UDP Port 6892)
17.35.12.0 – 17.35.12.30 (UDP Port 6892)
91.239.24.0 – 91.239.24.255 (UDP Port 6892)
91.239.25.0 – 91.239.25.255 (UDP Port 6892)
Artifacts:
==========
File name: 1
File size: 276KB
MD5 hash: 470cd3c8eade6de95bec9fd55c608d0a
Virustotal: http://www.virustotal.com/en/file/ddb73ca1570b01593734cea63940a7d09c0eb4aab896d24f8f264871467bbe5a/analysis/
First detection: 2017-01-25 10:05:35 UTC
Detection rate: 6 / 57
File name: 4f1b.tmp
File size: 344B
MD5 hash: bfa0ca8894dee5f00fd3617e513a6ce2
Virustotal: NA
File name: 812b.tmp
File size: 130B
MD5 hash: 185aa1b193f0cf9f913fff50633369b5
Virustotal: NA
Analysis:
=========
Based on what I am seeing, the user would be directed to the site “hxxp://sallykandymandy[.]top/search.php” and once there would be asked if they would want to download a file.
Once the file has been downloaded and saved, nothing can be executed since it is not a known-file type to Windows. In order to infect my VM, I had to add the extension of “.exe” to the file.
Once renamed, I then executed the binary which caused the usual traffic that we have seen before from Cerber, and the standard notifications as well.
One thing to note here – I did have a new folder created in the “C:\Users\%Username%\AppData\Local\Temp” folder called “35ff7078” with two files in it: 4f1b.tmp and 812b.tmp. The “4f1b.tmp” file looks to be base64 encoded:
Encoded G0o916oXNjlbIjr1JaWhG73gCT8BFZyaUrorLe56kGKnGdPwacgcbamActPI9C5xAGYONy+XOqKe1J6IKmN0CkY3id3mF6iCudbL7oSNBcoSQQ5ygRbqVkWGdZqQ01qXvYzwQg+5tzPS6921Ddh2/rHZ1rKMfTTJv+DxiKAs+4cuC4hl4OI2iXke65kKcBk+ybzOKrbEdL18N9stoHKVOJX4gtOcNM3YgMR1kKhfr3JVvVW7ArqBpseRMpSSCBb2h35Czs/G/WY6szjxDz2tDFuejbXRFUarDbNF8B+vmdD+me2APx406qDhm+x+LZ6V8RGO1lacwr3aaL7tMsKWYg== ----- Decoded J=ת69[":% ?R+-zbimr.q�f7/:Ԟ*ct F7ArVEuZB3ݵ vֲ}4ɿ,.e6y p>ɼ*t|7-r8Ӝ4u_rUUǑ2~Bf:8=[F E?4~-V½h2b
The other file (812b.tmp) looks like it could possibly be related to the file encryption since I am seeing the keyword “RSA” when looking at the file in Notepad++.
¤ RSA1p ufwÐ]µæÛZI܈åW²æÍp\„Ƈ×Õ,?ÇöXÉnÎÖc‹êE÷ê¥ Úf¡pÀ°ÒÎë‡îÞ4ÈDª¢+ *$ˆõDÇ»ç.ÍFƒ°» xìæ‡ãš!2çÕpJ +>¯¢É’«”ó